Last Updated on February 19, 2024 by Michael Morten Sonne
Stale Application Analysis for Entra ID – some power from PowerShell!
In the dynamic realm of Enterprise applications created over time in your Entra ID tenant, managing and securing user access is a paramount task. If you’ve recently implemented restrictions on user registrations or are simply delving into the labyrinth of your Enterprise applications, the Stale Application Analysis PowerShell script for Entra ID can be your trusty companion.
I have used it many times, and am sure it can help you too – and if not, let me know if it can be better – create an Issue or a Pull request on GitHub! 🫡😎
A script with a story
In the spirit of community and collaborative knowledge-sharing (here, on the internet and humans in real life), I’m excited to bring to light a hidden gem from my digital arsenal 🙈
This script has traversed the annals of my digital toolkit, quietly streamlining processes, tackling challenges, and making my tech life just a tad bit easier. It’s like an old friend, always there when you need it, and ready to lend a helping hand – or so! 🤣
Now, as I stand at the crossroads of opportunity and generosity, I believe it’s time to pass on the torch – I think more will come 🙈
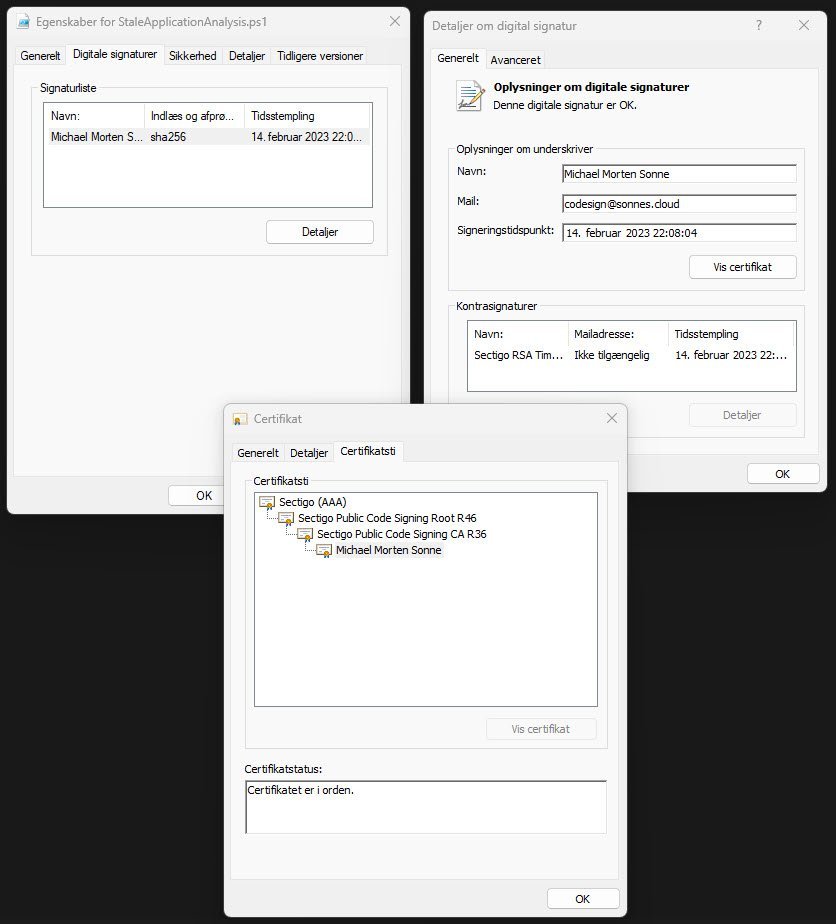
This script here, honed through trial and error, holds the potential to bring efficiency, clarity, or perhaps a touch of automation to your tasks. It´s last changed in the start of last year (2023), and is code signed with my code sign certificate too at that date.
In the spirit of collaboration and community support, I’m thrilled to share with you a hidden gem.
So today, I’m extending an invitation to all tech enthusiasts, sysadmins, and PowerShell aficionados out there to dive into the workings of a script that’s been a reliable companion on my digital journeys.
Im in the process (yes, still…) from migrateing all my stuff from Azure DevOps to GitHub to do it a bit easier for me to share stuff and keep my private stuff in one place – do it a bit easyer for me to manage and track all my code/scripts!
The script here use the Azure AD PowerShell module to get stuff from when you have exported your .csv file and set that as an argument to give it some work to do with our list of Entraprise Applications from the Entra ID Portal.
Yes I know the Azure AD Module is on it´s way out, but this is how the script is created back in time!
Check out this post for essential insights on why it’s crucial to keep your PowerShell modules up-to-date and discover how you can automate this process!
Check out the post here: The Importance of Updating Installed PowerShell Modules – And automate it too with my script – Blog – Sonne´s Cloud (sonnes.cloud)
Identifying unassigned Applications
The script simplifies the process of identifying applications without user useage if you have maby, offering a crucial first step in optimizing your application landscape. By pinpointing these unassigned/unused applications, you gain insights into potential security gaps and ensure that each application has an intended user audience.
Uncovering dormant Applications
The second leg of the script’s journey involves uncovering applications that have not witnessed any sign-ins in the last 30 days. This functionality is invaluable for recognizing dormant applications that may no longer serve a purpose or require attention to rekindle user engagement.
How to use the script
To use the script, perform the following actions – it´s easy 😉
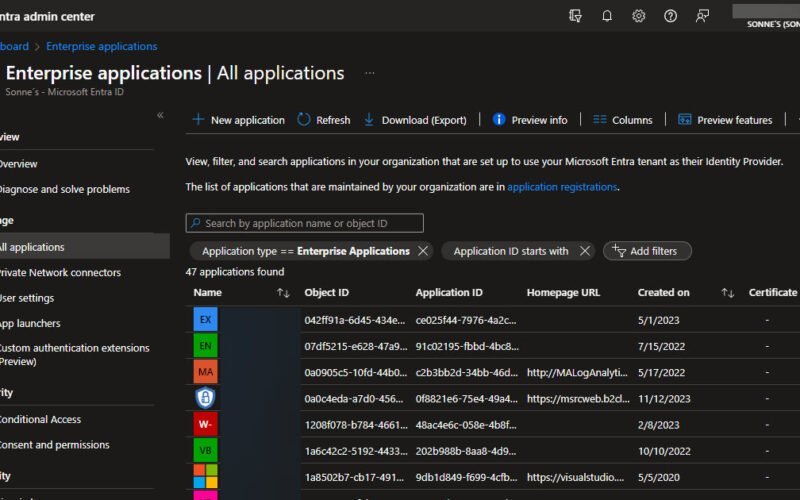
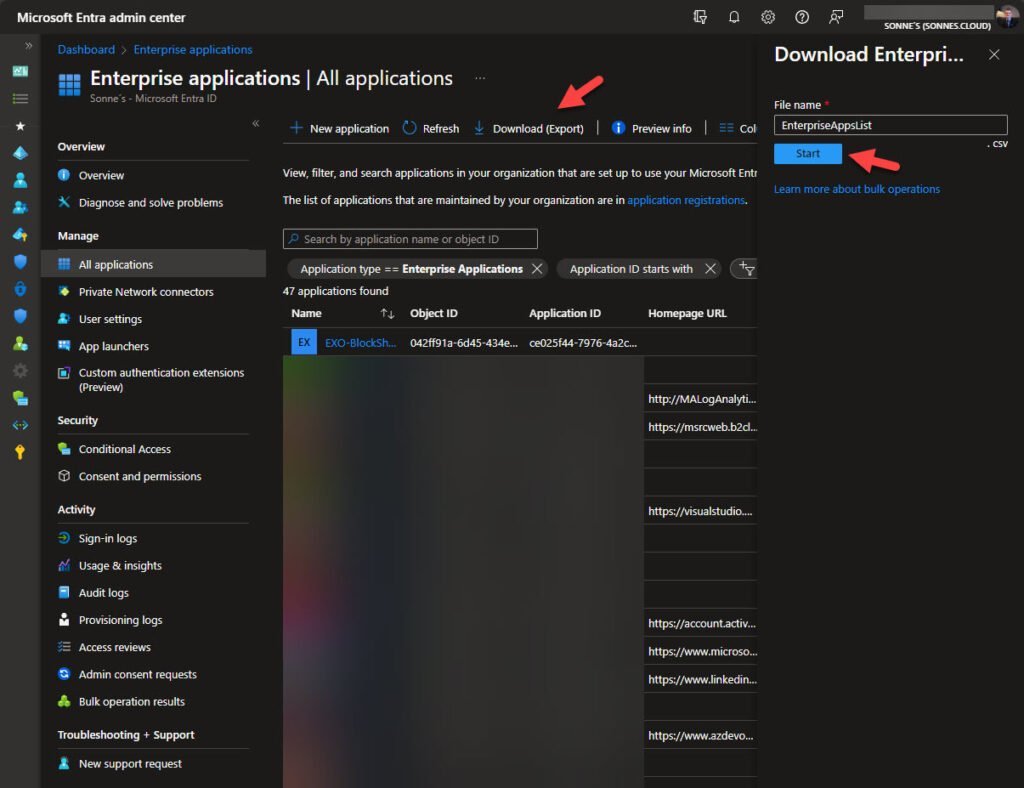
- Download Application Data: Begin by navigating to Azure portal and select Download (Export), and retrieve the .CSV file containing your application data like here (we need this information to later use):
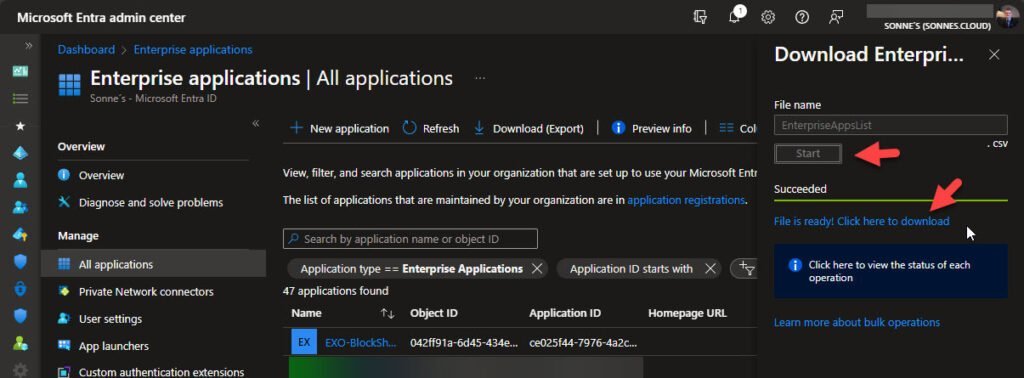
- Download the file when its ready to download (I agree, this can be better 🙈)
- Now move the downloaded EnterpriseAppsList.csv file to the same location as the script StaleApplicationAnalysis.ps1 is – the script for now as it is, looking for that filename in the same location as the script is.
- Azure Login: Now we need to ensure you are logged into Azure using the Connect-AzureAD command (if not, the script will ask you 🫡).
You need to have permissions to read login and auditlogs.
It’s recommended to use AzureADPreview for enhanced logging functionality – This can be changed in the future…
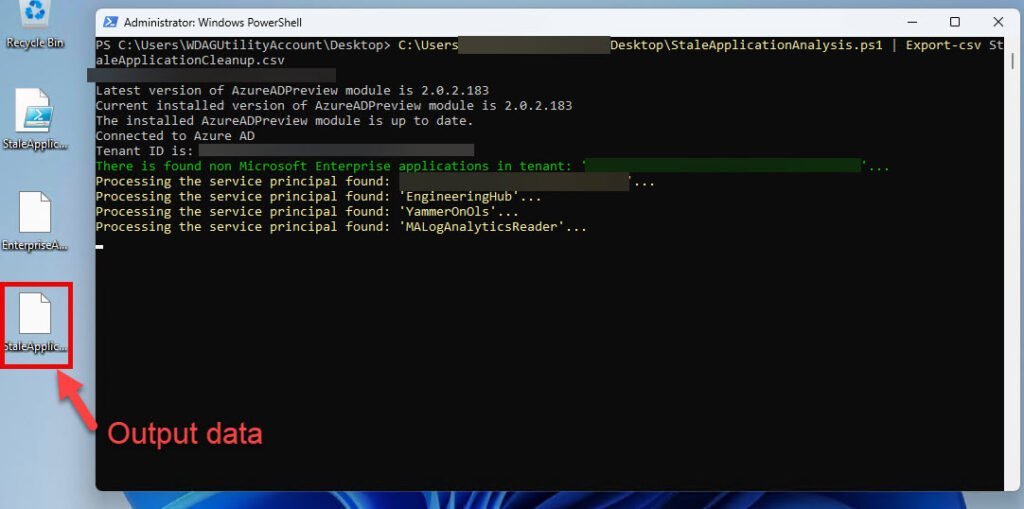
- Run the Script: Launch a PowerShell console and run the script using the command:
.\StaleApplicationAnalysis.ps1 | Export-csv StaleApplicationCleanup.csv
The filename for the output data can you select – here is an example.
If script executions is disabled on your computer, run this with administrative permissions in your PowerShell Console:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned
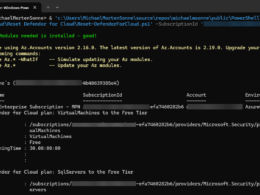
Now watch as the script does to work, analyzing your application data and generating insights.
The time it´s running may vary depending on the number of Enterprise applications it needs to analyze in your tenant.
Now after some time and the script is done with it´s work, it will show the output like this:
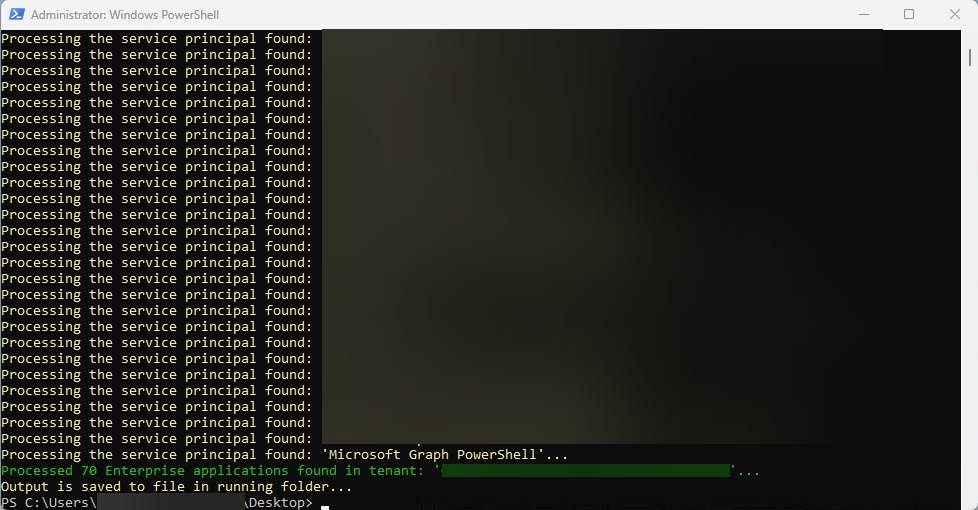
What to expect in the Output
The script generates a CSV output, highlighting crucial details for each application:
- ApplicationName: Clearly identifies the name of each application.
- ApplicationID: The ID identifies the unic ID of each application.
- SignIns: Reveals the number of sign-ins, shedding light on user activity.
- Users: Provides insights into the assigned users for each application.
This user-friendly output equips you with actionable information, empowering you to make informed decisions about your Enterprise application portfolio.
And yes it can be better and have much more data and etc. But the edition now is like it is for now – let me hear or see some pull request on GitHub it you will that!
The script
Here is the script itself direct from GitHub – and you can use it and change it for your need, as it can be changed a bit over time from the Community or me – some features can for sure be added:
Conclusion
In conclusion, the Stale Application Analysis PowerShell script is a versatile tool for administrators seeking to streamline application management and bolster security. By effortlessly identifying unassigned applications and spotlighting dormant ones, it paves the way for a more secure and optimized digital workspace. Try it out today and witness the power of streamlined application analysis in action!
Enhancing security posture and fostering sound application hygiene are achieved by eliminating unused applications. This action mitigates the risk of potential compromise, as discovering an unused application might lead to misuse for obtaining tokens. Depending on the application’s permissions and the exposed resources, a compromise could result in the exposure of sensitive organizational data.
Microsoft have some kind of this in preview, but there is some lack: Microsoft Entra recommendation – Remove unused apps (preview) – Microsoft Entra ID | Microsoft Learn
This inscludes etc. the following:
- The time frame for application usage that triggers this recommendation can’t be customized – change the code here, then you have that!
- The following apps won’t show up as a part of Microsoft´s build-it recommendation (again, in preview) but they are currently under review for future enhancements:
- Microsoft-owned applications
- Password single sign-on
- Linked single sign-on
- App proxy
- Add-in apps
More to come
I will over the next time share some stuff and scripts 😁
From this point forward, the script may see changes initiated by the community or by myself. The beauty lies in the fluidity of open-source development, where every suggestion can become a feature, and each improvement is a step forward.
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳