Last Updated on April 4, 2024 by Michael Morten Sonne
In Public Preview as this post is written
Intoduction
What is comming to the Microsoft Defender Portal
I’m excited to announce that the public preview of Microsoft´s new unified security operations platform is finally here! 😎
Having been part of the private preview stage myself (once again, of course 😂), I’ve had the opportunity to test it thoroughly and provide feedback on its functionality, performance, and overall experience. Back in November 2023, when they initially introduced a limited preview, it was evident that this platform stood out as one of the pioneers in the realm of security operations center platforms. It seamlessly integrates the full suite of features from a leading cloud-native security information and event management (SIEM) system, a comprehensive extended detection and response (XDR) platform, and AI tailored specifically for cybersecurity. This amalgamation of capabilities truly delivers a unified experience for analysts in the security operations center (SOC).
This exiting new public preview of Microsoft Defender is now accessible to users of both Microsoft Sentinel and Microsoft Defender XDR, consolidating these platforms into a single portal! 😮
This integration offers enhanced capabilities such as AI, automation, guided experiences, and curated threat intelligence to empower security teams in their efforts to prevent, detect, investigate, and respond to threats across various security domains. Microsoft Defender streamlines workflows, minimizing context switching, while automatically identifying and thwarting attacks across diverse environments, including non-Microsoft products, multicloud setups, and multiplatform ecosystems.
Additionally, it incorporates Microsoft Security Copilot to assist with pertinent tasks as needed there have GA (General available) here the 1. of April! See more here: Microsoft Security Copilot in Microsoft Defender XDR | Microsoft Learn🤘
Advantages of linking a workspace for hunting
The integrated advanced hunting feature in the unified portal enables you to access and query all data from Microsoft Defender XDR, along with data from diverse Microsoft security services and Microsoft Sentinel, incorporating information from non-Microsoft products, all within one platform. Moreover, you retain the ability to utilize your existing Microsoft Sentinel workspace content, including queries and functions and utilize KQL (Kusto Query Language)!
Some samples can etc. be:
- Utilizing Advanced Hunting in Microsoft Defender Portal:
- Investigating potential threats across multiple data sources is made easier with Advanced Hunting. It seamlessly queries data from both Microsoft Sentinel and Microsoft Defender, enhancing productivity and improving the quality of investigations. This integrated approach enables effective correlation of information, streamlining the hunting process.
- Analyzing data from various tables in Microsoft Sentinel becomes more straightforward with Advanced Hunting. Accessing all tables from Sentinel within the Microsoft Defender portal simplifies the querying process and saves valuable time. This centralized access enhances user-friendliness and efficiency, making it easier to navigate and analyze large datasets.
- By leveraging this unified platform, security teams gain access to comprehensive features that transcend traditional security tool silos. The platform offers a seamless and intuitive workflow for SOC analysts, providing unified views of incidents, exposure, threat intelligence, assets, and security reporting—all within a single pane of glass.
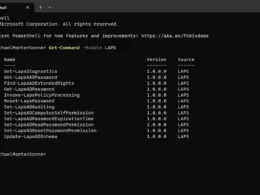
- Enhanced data visualization features in Advanced Hunting are appreciated. The appearance of data types in schemas, even for older tables, provides greater clarity and insight into the structure of the data, facilitating more informed decision-making and analysis.
- Advanced Hunting in Microsoft Defender Portal:
- Scenario: Exploring the capabilities of Advanced Hunting in the Microsoft Defender portal reveals the ability to cross-query tables within a single user interface. This functionality represents a significant advancement towards a unified portal, simplifying operations and enhancing efficiency for managing multiple environments.
- Scenario: Recognizing the value of cross-hunting and detection capabilities offered by Advanced Hunting, it becomes possible to reduce the duplication of data across platforms and expand detection coverage. This capability allows for optimization of resource utilization and enhanced security services.
This consolidation of features not only streamlines operations but also enhances capabilities across the entire cyberattack lifecycle. With the ability to run custom security orchestration, automation, and response (SOAR) playbooks and hunt across data sources in one place, organizations can significantly improve their incident response times and overall security posture.
Furthermore, the integration of Microsoft Sentinel and Microsoft Defender XDR products further enhances the value proposition. XDR customers benefit from increased flexibility in reporting, deployment automations, and deeper insights across data sources. Similarly, SIEM customers can extract more out-of-the-box value, enabling them to focus on proactive threat mitigation and novel threat detection.
Known limitations (for now)
To highlight some of the current gaps, I’ve listed them here – and some may be addressed in the future, so stay tuned!
- Queries for Microsoft Defender XDR tables are limited to a maximum lookback period of 30 days.
- Sentinel queries and functions are view-only: editing is not permitted.
- Microsoft Defender only supports custom detections, incident linking, and action-taking capabilities.
- Advanced hunting lacks support for bookmarks.
- Full equivalence in capabilities between the Log Analytics grid and advanced hunting is still in progress.
Setup
Required roles and permissions
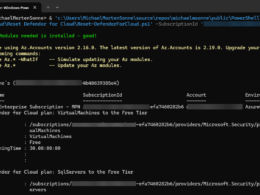
To query across your Microsoft Sentinel and Microsoft Defender XDR data in the unified advanced hunting page, you must have access to Microsoft Defender XDR advanced hunting (see Required roles and permissions) and at least the role Microsoft Sentinel Reader (see: Microsoft Sentinel-specific roles) for access Sentinel data.
But in overall, the list looks like this:
To onboard and use Microsoft Sentinel in the Microsoft Defender portal, you must have the following resources and access:
- A Log Analytics workspace that have Microsoft Sentinel enabled and setup
- Data connector for Microsoft Defender XDR (formerly known as Microsoft 365 Defender) enabled in Microsoft Sentinel for incidents and alerts
- Microsoft Defender XDR onboarded in your Microsoft Entra tenant
- And an Azure account with the appropriate roles to onboard, use, and create support requests for Microsoft Sentinel in the Defender portal.
The overview of permissions as this post is written is listed here so you can get a nice overview:
| Azure built-in role | Scope | Reason |
|---|---|---|
| Owner or User Access Administrator and Microsoft Sentinel Contributor | – Subscription for Owner or User Access Administrator roles – Subscription, resource group, or workspace resource for Microsoft Sentinel Contributor | To connect or disconnect a workspace with Microsoft Sentinel enabled |
| Microsoft Sentinel Reader or a role with the following actions: – Microsoft.OperationalInsights/workspaces/read – Microsoft.OperationalInsights/workspaces/query/read – Microsoft.SecurityInsights/Incidents/read – Microsoft.SecurityInsights/incidents/comments/read – Microsoft.SecurityInsights/incidents/relations/read – Microsoft.SecurityInsights/incidents/tasks/read | Subscription, resource group, or workspace resource | Query Sentinel data tables or view incidents |
| Microsoft Sentinel Contributor or a role with the following actions: – Microsoft.OperationalInsights/workspaces/read – Microsoft.OperationalInsights/workspaces/query/read – Microsoft.SecurityInsights/incidents/read – Microsoft.SecurityInsights/incidents/write – Microsoft.SecurityInsights/incidents/delete – Microsoft.SecurityInsights/incidents/comments/read – Microsoft.SecurityInsights/incidents/comments/write – Microsoft.SecurityInsights/incidents/comments/delete – Microsoft.SecurityInsights/incidents/relations/read – Microsoft.SecurityInsights/incidents/relations/write – Microsoft.SecurityInsights/incidents/relations/delete – Microsoft.SecurityInsights/incidents/tasks/read – Microsoft.SecurityInsights/incidents/tasks/write – Microsoft.SecurityInsights/incidents/tasks/delete | Subscription, resource group, or workspace resource | Take investigative actions on incidents |
Within the unified portal, you have the ability to query data from any workload accessible to you, determined by your roles and permissions! 😎
Go hunt! 👌🧐
How to connect them together
Connecting to Microsoft Defender XDR from Microsoft Sentinel
Now we need the last part – the connector setup in Microsoft Sentinel.
To integrate with Microsoft Defender XDR make sure you have:
- Workspace: read and write permissions.
- Connector Access Control: the user applying changes to the connector must be a member of the Microsoft Entra ID associated with the tenant that the workspace belongs to.
- Tenant Permissions: ‘Global Administrator’ or ‘Security Administrator’ on the workspace’s tenant.
- License: M365 E5, M365 A5 or any other Microsoft Defender XDR eligible license.
Review and comprehend the product modifications linked to connecting your workspace. These alterations encompass:
- Defender XDR incidents are displayed in Sentinel under the product name Microsoft Defender XDR – offering functionality akin to other Sentinel incidents.
- Each incident have a link directing back to the corresponding incident in the Microsoft Defender Portal.
- Any alterations in status, closure rationale, or assignment are mirrored across both platforms.
- Incident data and details synchronize bidirectionally between platforms with minimal delay, ensuring near-real-time updates.
- Additionally, merging incidents in XDR reflects in Sentinel, consolidating all alerts into one incident while automatically closing the other.
Set it up:
- Go to portal.azure.com > Microsoft Sentinal and find your Workspace.
- Find Data Connectors under your Sentinal Workspace under the section for Data connectors.
- Find the Microsoft Defender XDR data connector from the gallery and click Open connector page to access the configuration settings we need! Here you find this settings:
- Connect incidents and alerts: This enables basic integration, synchronizing of your incidents and their alerts between the connected platforms.
- Connect entities: This integrates on-premises Active Directory user identities into Microsoft Sentinel through Microsoft Defender for Identity – how to deploy this, take a look in my blog here: Microsoft Defender for Identity – What is it, how to install it and setup requirements – Blog – Sonne´s Cloud (sonnes.cloud).
- Connect events: This enables the collection of raw advanced hunting events from Defender components for in-depth analysis.


To deactivate a particular component’s connector, it is necessary to first detach the primary Microsoft Defender XDR connector.
After your workspace is connected, the banner on the Overview page confirms that your unified SIEM and XDR setup is ready and ready to hunt.
Now we can do the connection in Defeder XDR 👌
Connecting to Microsoft Sentinel from Microsoft Defender XDR
To configure this feature for your tenant and verify its ready for you, you will notice a banner on the homepage of your Defender Portal like this:

To connect a workspace that has Microsoft Sentinel enabled to Defender XDR, complete the following steps:
- Go to the Microsoft Defender portal and sign in if not allready that.
- In Microsoft Defender XDR, select Overview.
- To start onboarding, click on Connect a workspace – and then this wizard shows up
- Search for the workspace you will add – and click on Next

- If you see this error, you have not the needed permissions to connect:


- Review and comprehend the product modifications linked to connecting your workspace. These alterations encompass:
- The log tables, queries, and functions present in the Microsoft Sentinel workspace are accessible in the advanced hunting feature within Defender XDR.
- Active creation rules for Microsoft security incidents are disabled to prevent redundant incidents. This modification solely affects incident creation rules associated with Microsoft alerts and not other analytics rules.
- The Microsoft Sentinel Contributor role is designated to the Microsoft Threat Protection and WindowsDefenderATP applications within the subscription.
- All alerts linked to Defender XDR products are directly streamed from the primary Defender XDR data connector to ensure uniformity. Ensure that incidents and alerts from this connector are activated in the workspace.
- If everything is in order and you’re prepared to connect, simply click Connect and the remainder will proceed automatically.



Now this part is done!
To deactivate a particular component’s connector, it is necessary to first detach the primary Microsoft Defender XDR connector.
After your workspace is connected, the banner on the Overview page confirms that your unified SIEM and XDR setup is ready and ready to hunt.
Find Microsoft Sentinel settings in the Defender portal under System > Settings > Microsoft Sentinel.
Offboard Microsoft Sentinel workspace
Only one workspace can be connected to the Defender portal simultaneously. If you wish to connect to a different workspace with Microsoft Sentinel enabled, disconnect the current workspace and connect the new one.
- Go to the Microsoft Defender portal and sign in.
- In the Defender portal, under System, select Settings > Microsoft Sentinel.
- On the Workspaces page, select the connected workspace and Disconnect workspace.
- Confirm your selection. When your workspace is disconnected, the Microsoft Sentinel section is removed from the left-hand side navigation of the Defender portal. Data from Microsoft Sentinel is no longer included on the Overview page.
If you want to connect to a different workspace, from the Workspaces page, select the workspace and Connect a workspace and you are good to go again! 🤘
What to expect when the workspace is connected
- Log tables, queries, and functions in the Microsoft Sentinel workspace will also be available in advanced hunting within Microsoft Defender XDR.
- The Microsoft Sentinel Contributor role will be assigned to the ‘Microsoft Threat Protection’ and ‘WindowsDefenderATP’ apps within the subscription.
- Active Microsoft Security incident creation rules will be deactivated to avoid duplicate incidents. This change will only apply to incident creation rules for Microsoft alerts and not to other analytics rules.
- All alerts related to Microsoft Defender XDR products will be streamed directly from the main Microsoft Defender XDR data connector to ensure consistency. Make sure you have incidents and alerts from this connector turned on in the workspace.
Discover the Microsoft Sentinel features within the Defender portal
After connecting your workspace to the Defender portal, Microsoft Sentinel appears on the left navigation pane. Key pages like Overview, Incidents, and Advanced Hunting offer unified data from Microsoft Sentinel and Defender XDR.
Many existing Microsoft Sentinel features are integrated into the Defender portal, providing a familiar experience. Explore these articles to begin using Microsoft Sentinel in the Defender portal.
Locating your Sentinel Data
You can utilize advanced hunting KQL queries to sift through data from both Microsoft Defender XDR and Microsoft Sentinel. Upon accessing the advanced hunting page for the first time post workspace connection, you’ll discover your Sentinel tables categorized by solution beneath the Microsoft Defender XDR tables within the Schema tab.

Run functions
To utilize a Sentinel function, navigate to the Functions tab and locate your desired function by scrolling. Double-click the function name to insert it into the query editor. Alternatively, click the three stacked dots (⋮) next to the function and choose “Insert to query” to insert it into a query.
For editable Microsoft Defender XDR functions, more options become available when selected:
- Edit details opens the function side pane for editing details.
- Delete removes the function.
Run saved queries
To use a saved query from Sentinel, visit the Queries tab and locate your desired query by scrolling. Double-click the query name to load it into the query editor. For more options, click the three stacked dots (⋮) next to the query. Here, you can:
- Run query automatically loads and executes the query in the query editor.
- Open in query editor loads the query in the query editor.
- View details opens the query details side pane for inspection, running, or opening the query in the editor.


For editable Microsoft Defender XDR queries, additional options are available when selected:
- Delete removes the query.
- Rename allows you to modify the query name.
Create custom analytics and detection rules
To enhance threat detection in your environment, create custom detection policies. Access Manage rules > Create analytics rule for rules applying to data ingested through the connected Sentinel workspace.

The Analytics rule wizard will guide you through the process. For custom detection rules on Microsoft Defender XDR data, select Manage rules > Create custom detection.
Read more about this here: Create and manage custom detection rules in Microsoft Defender XDR | Microsoft Learn
Explore found results
Query results you’ve executed are displayed in the Results tab:

To export these results to a .CSV file, simply click on Export.

Explore the results using the following features:
- Expand a result by clicking the dropdown arrow on the left of each entry.
- For JSON array format results, expand details by clicking the dropdown arrow beside applicable column names for better readability.
- Open the side pane to view a record’s details (in conjunction with expanded rows).
Additionally, right-click on any result value to add more filters to the current query or copy the value for further investigation.
For Microsoft Defender XDR data, you can take further action by selecting the checkboxes to the left of each result row. Select Link to incident to link the selected results to an incident (read Link query results to an incident) or Take actions to open the Take actions wizard (read Take action on advanced hunting query results).
Rerun queries from query history
In the Query history tab, you can access previous queries for both Defender and Sentinel. Choose to run selected queries by clicking Run query or add them to the query editor area using Use in editor.

You can see more of the new features added here too: Microsoft Defender XDR – Experience Improvements for Advanced Hunting – Blog – Sonne´s Cloud (sonnes.cloud)
Unified incidents
Explore the incident investigation process within the Microsoft Defender portal, mirroring the experience found in Defender XDR. Discover effective navigation of the Investigate incidents in Microsoft Defender XDR | Microsoft Learn.
Customers can leverage the incident features available in the Microsoft Defender portal by connecting a workspace, streamlining the process of conducting comprehensive incident investigations without the necessity of switching between multiple portals – like when useing the Defender XDR timeline or an Defender for Office email investigation!
There is still some parts like for MSSP´s and looking into multiple tenants this way, there is not there yey – but let´s see what is comming over the time to this new feature! 😎
Avoid duplicate incidents
How it is now, Defender XDR and Sentinel create incidents from the same alerts using different logic, there can lead to duplicates.
Suggestion: Turn off Microsoft Sentinel’s incident creation rules for XDR-integrated products such as Defender for Endpoint to avoid redundant entries. This adjustment can be made within the connector page.
Please be aware that disabling these rules will also remove any filters they may have applied previously.
Anticipated changes in your environment
Outlined below are the forthcoming alterations to anticipate in the investigation process within Microsoft Sentinel and Microsoft Defender XDR:
Microsoft Defender XDR:
- Incidents from Sentinel are visible in the incidents queue.
- You can filter incidents by selecting Microsoft Sentinel as a service source.
- Alerts sourced from Microsoft Sentinel are visible in the alerts queue.
- Filtering options include selecting Microsoft Sentinel as a service or detection source.
- If you close incidents in Defender XDR, its closed in Sentinel as well
Microsoft Sentinel:
- Ingestion of data shifts to the XDR connector.
- Incident creation rules are automatically disabled.
- Custom incident titles are generated for merged alerts.
- Default incident provider becomes Microsoft Defender.
- Editing comments, adding/removing alerts, and tasks are not supported.
- Automation rules now include detailed information on updates.
- If you close incidents in Sentinel, its closed in Defender XDR as well
So, the follwoing tasks can only be performed in Sentinel (for now):
- Tasks and related to this
- Added a new entity to a theat indicator
- Automation
- Workspace Manager
But hey – we have a lot, but lets see what´s comming over the time 👌
This is written out of the best way of what I see and could find – can not be 100%correct!
Note: Some features, such as editing comments and reopening resolved incidents, are not supported in the unified portal.
And again: This is now in Public Preview so changes can happen and will over time!
Alert limit
Within Sentinel, incidents can accommodate up to 150 alerts. Should an Defender XDR incident surpass the threshold of 150 alerts, Sentinel will display 150+ and furnish a link to access the complete array of alerts in Defender XDR.
Unified entity pages
The Unified platform now features redesigned User, Device, Cloud resource and IP entity pages too, that seamlessly integrate data from both Microsoft Defender XDR and Microsoft Sentinel. This integration streamlines investigation processes, eliminating the need to switch between portals when responding to incidents or just explore the data from your tenant!
Notably, pertinent information from Sentinel is conveniently accessible within a dedicated tab labeled Sentinel Events. The process for accessing the entity page within the Defender Portal remains unchanged, ensuring continuity in workflows. Whether navigating through incident details or analyzing advanced hunting query results, users can effortlessly access entity pages as before! 👌

Experience the new unified pages
To fully utilize the unified entity pages, you need to establish an analytics rule that correlates a Defender XDR user or device with the corresponding inventory entry, ideally within an existing Defender XDR alert. If dealing with an IP address, ensure it’s referenced within an existing alert, as there’s no separate IP inventory. If an entity is already linked to both a Defender XDR and Sentinel alert, you may omit this step.
- To create one, go to Microsoft Defender > Microsoft Sentinel > Configuration > Analytics.
- Now you can see a list of your rules used, and you can create a new one via the Create button – a wizard will now show up. In the General tab, fill is the rule name, Severity and a description. Click Next : Set rule logic>.
- You can use the following synthetic rule to map stuff:
- Use AADID or SID for a user (where x is the SID of your selected identifier)
- HostName or NetBiosname alongside DnsDomain or NtDomain for a device
- IP address.

- Now go back to Microsoft Defender > Investigation & response > Incidents & alerts> Incidents. Under here find queue and select the entity from either the graph or entity lists on the right-side pane.
- Open the entity page – etc. a device.

- Open the entity page.

Now under here you should be able to see Sentinel specific information in the Sentinel Events tab of the entity page.
And here is a sample for a user:

Conclusion
In conclusion, the unveiling of our unified security operations platform marks a significant milestone in the realm of cybersecurity. By seamlessly integrating the capabilities of SIEM, XDR, exposure management, generative AI, and threat intelligence, we’ve revolutionized the way security teams combat cyber threats.
Nice to see Microsoft really making an effort on Unifying the different portals. For some time ago it was for Microsoft Defender for Identity and Cloud Apps into the Defender portal and now you can connect Sentinel workspace as well! 🥳
This platform not only addresses the pressing need to streamline security operations but also empowers analysts with intuitive workflows and comprehensive insights across their digital estate. With a single pane of glass view and automatic attack disruption technology, security professionals can now respond to threats with unprecedented speed and efficacy.
Moreover, our commitment to continuous innovation is evident through features like Microsoft Copilot for Security, which serves as an intelligent assistant, aiding analysts in accelerating triage and enhancing incident response.
As we move forward into this new era of cybersecurity, we invite organizations to join us in our public preview and experience firsthand the transformative power of our unified security operations platform. Together, we can fortify defenses, mitigate risks, and safeguard the digital landscape against evolving threats.
And as always, it has been super nice to work together with the Product Team at Microsoft on this new exciting feature – and to see it all take shape! 🥳
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳