Last Updated on April 3, 2024 by Michael Morten Sonne
Table of Contents
- Intoduction
- The attacks out there in the wild
- How to start and use it
- Prerequisites
- How to hunt and respond to QR code-based attacks
- Hunt for the QR codes in your tenant
- Mitigations to help you against this
- Conclusion
- References
Intoduction
Now you can strengthening your defense against QR Code phishing attacks with Defender for Office 365 and Advanced Hunting (KQL)! 😎
The team behind Defender for Office 365 has implemented significant enhancements over the time to its investigation, hunting, and response capabilities to response to the threat landscape today. These updates are specifically designed to empower security teams in identifying and addressing QR code phishing threats.
Additionally, this will assist in assessing the frequency of QR code-based attacks within your organization. This will enable you to establish a secure posture and educate users about potential risks associated with such attack patterns.
In recent months, QR Code phishing has surged, with attackers employing innovative methods to circumvent established safeguards. This tactic is frequently utilized to evade defenses and illicitly acquire user credentials or tokens through Advanced In-the-Middle (AiTM) techniques.
While QR code phishing is not a new threat and a bit old, its prevalence has notably increased since the onset of the good “old” COVID-19 pandemic… To address this growing risk, Microsoft has recently introduced enhanced protections, including default security measures and supplementary controls, aimed at fortifying defenses against QR code-based attacks.
What is a QR Code?
A QR code, short for “Quick Response code” is a type of two-dimensional barcode that can be scanned using a smartphone or any other mobile device equipped with a camera. These codes are capable of storing diverse types of information, including website URLs, contact details, product specifics, and beyond. Primarily, QR codes serve as convenient shortcuts, often directing users to websites, files, or applications. In essence, you can consider a QR code as similar to a URL in function and purpose.
There is much data about what an OR-code is and how old it is here: QR code – Wikipedia

For example when you can this QR code it will redirect you to the Defender for Office 365 product page – it´s fun to read!
There is many generators to do this online and so – test it! 🤘
Ways to distribute QR codes
QR codes can be disseminated through various channels such as email, Teams, chat, or messaging apps in any kind. The following methods are commonly utilized (all there can send pictures…):
- Embedded directly as images within the email body.
- Integrated within an image within the email body.
- Presented as an image within a message like SMS/iMessage or other messeng services like Signal.
- As an image within an attachment.
QR codes are typically scanned using smartphones or tablets, whether they’re personal or work devices – and the feature here is build in in all new phones, so it´s wildy used all over the world 🫢
The attacks out there in the wild
Phishing is a common and highly effective cyberattack method, is frequently used by threat actors to compromise email accounts, pilfer sensitive data, and distribute malware. A recent trend in phishing campaigns involves the use of QR codes embedded in emails to bypass detection and deceive users into accessing malicious links (etc. Defender for Office Safe Links).
Enhancing Defender protection against QR code threats
Microsoft has recently introduced enhanced controls within the Defender for Office protection suite to more effectively detect QR codes. Previously, detecting QR codes with phishing links, especially when embedded within email bodies or attached as images, posed significant challenges due to limited scanning capabilities.
Given the hight use of personal smartphones today, which may lack robust corporate security and setup, it’s advisable to bolster defense strategies across your entire protection suite. This includes configuring products appropriately, implementing additional layers of security for both personal and company-owned devices, and incorporating QR phishing awareness into your training programs – as myny miss…
The recent updates include:
- Image Detection: Leveraging image extraction technologies, Microsoft now detects QR codes during the mail flow using Defender for Office 365 and Exchange Online Protection. URL metadata extracted from QR codes undergoes thorough URL checks, including detonation and sandboxing to identify potential threats like we know from Safe Links.
- URL Analysis: URLs extracted from QR codes undergo analysis by machine learning models and are checked against internal and external sources for reputation using Threat Intelligence data. This feature requires Defender for Office 365 Plan 1 or Plan 2.
- Threat Signals: Multiple signals, including message headers, recipient details, content filtering, and machine learning algorithms, are utilized to identify potential malicious emails.
- Heuristic-Based Rules: Microsoft has deployed heuristic rules within Defender for Office 365 and Exchange Online Protection to intelligently assess and block malicious messages.
These enhancements offer improved protection against QR code-based threats, reinforcing your organization’s security posture within the Microsoft ecosystem.
And the nice is to that all this happening in the sandboxing environment at Microsoft – not accessible by customers to check URLs or QR codes manually! – Remember this! 🤪
The sandboxing functionality operates automatically in the background, leveraging intelligence sharing with the products themselves. This collaboration enables the products to determine appropriate actions and assess URL reputation! 😎
How to start and use it
Prerequisites
Roles and licenses needed to use this feature:
- You must have EOP and Microsoft Defender for Office 365 Plan 1 or Plan 2 licenses. Good to know is that the detonation and sandboxing featres is only available for Office 365 Plan 1 and Plan 2 licenses!
- Must have administrator role of Security Administrator, Global Reader, Exchange Administrator or Global Administrator to hunt and see data in Advanced Hunting.
- Must have administrator role of Security Administrator, Global Administrator, Attack Simulation Administrators or Attack Payload Author to run simulations and view reports or explore data.
How to hunt and respond to QR code-based attacks
When URLs are extracted from the QR codes send to your tenant, they will be tagged with the source or location identifier as QR code so you can find it. This distinct labeling ensures easy identification within the system.
Lets send a test email with a QR-code into it, so we can see the collected data in Defender for Office 365 about it:

Below, see an example on how you can can effectively filter for URLs extracted from QR codes in diffrent ways there is possibel to explorer the data in:
- Email Entity view
- Threat Explorer
- Advanced Hunting
By incorporating these filtering techniques into their security operations, you can effectively monitor, detect, and respond to threats originating from QR code-based attacks, bolstering their overall security posture. URL´s and so in generel are to find.
To a start, go to your Defender portal under Email & collaboration > Explorer to start seartching for OR codes:

Now you have a complete list of emails and so with links in based on QR-codes 👌
Now lets explorer the parts in more details – and lets take a deeper look on the data from the QR-codes.
Email Entity View: In the Email Entity view, you can navigate to the URL tab. URLs originating from QR codes will be tagged with the QR code source as identifier. By applying filters within this tab you can isolate and analyze QR code-derived URLs specifically.
- Select the e-mail you wont to look info and when you have selected to look at it, and the menu here opens:

- You’ll find the Take actions button too located at the top-right corner of both the Email Entity and Email Summary panel. Clicking on this button will launch the Action wizard, offering step-by-step instructions on selecting individual or multiple actions simultaneously.
- Please note that the actions available here to any given user are still subject to the same permissions requirements based on their membership/role in the organization.
- Here you can etc. support tenant level block URLs and files (New addition to Take Actions) from the same panel.
- Multi selection of following action types:
- Submit to Microsoft for feedback.
- Tenant level allow/block rules.
- Triger Auto-investigations
- Email purge action/two-step approval (propose remediation)
- Here click on Open email entity and then click on the URL in the top bar to show the details about URL´s inside the mail – or in this case, a QR code:


Threat Explorer Tool: Utilizing the Threat Explorer tool, you can refine their search by applying the URL Source filter. Within this filter, selecting the “QR code” value will enable users to focus solely on URLs extracted from QR codes.
This targeted approach streamlines threat detection and response efforts. Admins have the option to refine their search criteria and undertake necessary remedial actions. Alternatively, they can proceed to the Email Entity page for a more thorough investigation and to implement suitable remediation measures.

- Advanced Hunting Queries: For advanced users, createing custom queries using the EmailUrlInfo table can provide deeper insights and automatisation too. This table contains data related to URLs extracted from emails, including those sourced from QR codes. By querying for URLs with the source location identified as “QR code,” customers can conduct in-depth analyses and proactive threat hunting activities.
Here is a sample:
EmailUrlInfo
| where UrlLocation == "QRCode"
Alongside the KQL-based interface, analysts can utilize the query builder to filter and hunt for QR code-based attacks. This can be achieved by employing the UrlLocation filter.
Fore more information about Advanced Hunting and KQL – take a look here: Overview – Advanced hunting | Microsoft Learn
Hunt for the QR codes in your tenant
Some queries on how to hunt for QR code-based attacks
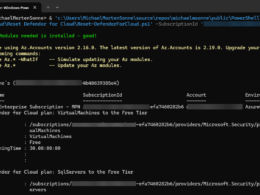
Volume of inbound emails with QR code in last 30 days:
EmailEvents
| where Timestamp > ago(30d)
| where EmailDirection == "Inbound"
| join EmailUrlInfo on NetworkMessageId
| where UrlLocation == "QRCode"
| summarize dcount(NetworkMessageId) by bin(Timestamp, 1d)
| render timechartGet the number of QR code based on domains and count them in total:
EmailEvents
| where Timestamp > ago(30d)
//| where EmailDirection == "Inbound"
| join EmailUrlInfo on NetworkMessageId
| where UrlLocation == "QRCode"
| summarize Count=count() by UrlDomain
| sort by Count descSo here, if you see a large number of domains, block it!👌
If unsure what the domains is, test it etc. at VirusTotal!
Emails delivered having URLs in the form of QR codes:
EmailEvents
| where Timestamp > ago(7d)
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| join EmailUrlInfo on NetworkMessageId
| where UrlLocation == "QRCode"
| project Timestamp, NetworkMessageId, SenderFromAddress, SenderIPv4, Subject, Url, UrlDomain, UrlLocationEmails delivered having URLs in the form of QR codes shorted on number of emails from the domains:
EmailEvents
| where Timestamp > ago(7d) // Filter events from the last 7 days (adjust as needed)
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| join EmailUrlInfo on NetworkMessageId
| where UrlLocation == "QRCode"
| summarize count() by SenderFromAddress // Count emails by sender
| order by count_ desc // Order the results by count in descending orderEmails with suspicious keywords in subject:
let SubjectKeywords = ()
{
pack_array("authenticate","authorize", "account", "confirmation", "QR", "login", "password", "reset", "payment", "urgent", "verify");
};
EmailEvents
| where Timestamp > ago(7d)
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| where Subject has_any (SubjectKeywords)
| join EmailUrlInfo on NetworkMessageId
| where UrlLocation == "QRCode"Post-delivery events like ZAP can effectively eliminate malicious emails containing QR codes. Security teams can monitor email ZAP alerts (indicating the removal of emails with malicious URLs after delivery), M365 incidents associated with ZAP alerts, and the automated investigations that follow.
Alternatively, security teams can initiate investigations from the actions workflow or create custom detection rules to generate personalized alerts.
Hunting for Adversary-in-the-Middle (AiTM) phishing and user compromise
The inability of users to decode QR codes poses a significant risk, leading to attacks like AiTM phishing. Attackers use QR codes to redirect users to fake websites, steal session tokens, and even download malware onto devices. These attacks can result in identity theft, financial loss, and data breaches.
User behavior monitoring
This detection method is crucial to identify suspicious sign-in attempts got from QR code phishing campaigns. Despite users scanning QR codes on their personal mobile devices, most phishing emails accessed are logged through mailbox auditing (remember to set it up if not..).
The majority of QR code campaigns feature image or document attachments, including Office files embedding QR codes. These campaigns often include legitimate URLs redirecting to phishing pages with malicious QR codes.
A malicious sign-in attempt, accompanied by session token compromise post-QR code scan, typically originates from non-trusted devices with a medium/high risk score for the session.
This detection strategy connects user access to emails with image/document attachments and risky sign-in attempts from non-trusted devices. It scrutinizes whether the email access location differs from the sign-in attempt location, providing valuable insights.
let successfulRiskySignIn = materialize(AADSignInEventsBeta
| where Timestamp > ago(1d)
| where isempty(DeviceTrustType)
| where IsManaged != 1
| where IsCompliant != 1
| where RiskLevelDuringSignIn in (50, 100)
| project Timestamp, ReportId, IPAddress, AccountUpn, AccountObjectId, SessionId, Country, State, City
);
let suspiciousSignInUsers = successfulRiskySignIn
| distinct AccountObjectId;
let suspiciousSignInCities = successfulRiskySignIn
| distinct City;
let suspiciousSignInIPs = successfulRiskySignIn
| distinct IPAddress;
CloudAppEvents
| where Timestamp > ago(1d)
| where ActionType == "MailItemsAccessed"
| where IPAddress !in (suspiciousSignInIPs)
| where AccountObjectId in (suspiciousSignInUsers)
| where City !in (suspiciousSignInCities)
| join kind=inner successfulRiskySignIn on AccountObjectId
| where AccountObjectId in (suspiciousSignInUsers)
| where (Timestamp - Timestamp1) between (-5min .. 5min)
| extend folders = RawEventData.Folders
| mv-expand folders
| extend items = folders.FolderItems
| mv-expand items
| extend InternetMessageId = tostring(items.InternetMessageId)
| project Timestamp, AccountDisplayName, ReportId, IPAddress, InternetMessageId, AccountObjectId, SessionId, Country, State, CitySender pattern analysis
Detection of QR code campaigns heavily relies on sender attributes. Typically, these campaigns involve emails from newly-created or uncommon domains within the organization, as opposed to compromised trusted vendors.
Attackers induce urgency by impersonating various roles like IT support, HR support, payroll, or administrators or even your CEO and so. Sometimes, the display name may suggest the email is sent on behalf of a high-value target in the organization.
This detection method correlates emails from uncommon senders with impersonation characteristics, aiding in the identification of suspicious QR code campaigns.
let PhishingSenderDisplayNames = ()
{
pack_array("administrator", "administration", "IT", "support", "Payroll", "HR", "admin", "2FA", "notification", "sign", "reminder", "consent", "workplace",
"benefits", "employee", "update", "on behalf");
};
let suspiciousEmails = EmailEvents
| where Timestamp > ago(1d)
| where isnotempty(RecipientObjectId)
| where isnotempty(SenderFromAddress)
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| join kind=inner (EmailAttachmentInfo
| where Timestamp > ago(1d)
| where isempty(SenderObjectId)
| where FileType has_any ("jpg", "jpeg", "png", "bmp", "gif")
) on NetworkMessageId
| where SenderDisplayName has_any (PhishingSenderDisplayNames())
| project Timestamp, Subject, FileName, SenderFromDomain, RecipientObjectId, NetworkMessageId;
let suspiciousSenders = suspiciousEmails | distinct SenderFromDomain;
let prevalentSenders = materialize(EmailEvents
| where Timestamp between (ago(7d) .. ago(1d))
| where isnotempty(RecipientObjectId)
| where isnotempty(SenderFromAddress)
| where SenderFromDomain in (suspiciousSenders)
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| distinct SenderFromDomain);
suspiciousEmails
| where SenderFromDomain !in (prevalentSenders)
| project Timestamp, AccountDisplayName, Subject, FileName, SenderFromDomain, RecipientObjectId, NetworkMessageIdPotential phishing campaign
This query identifies potential phishing campaigns by searching for emails with the same EmailClusterId but different senders, suggesting multiple email addresses are involved. It also filters for emails containing URLs. Adjust thresholds for rare domains and total senders as needed for your environment.
let RareDomainThreshold = 20;
let TotalSenderThreshold = 1;
let RareDomains = EmailEvents
| summarize TotalDomainMails = count() by SenderFromDomain
| where TotalDomainMails <= RareDomainThreshold
| project SenderFromDomain;
EmailEvents
| where EmailDirection == "Inbound"
| where SenderFromDomain in (RareDomains)
| where isnotempty(EmailClusterId)
| join kind=inner EmailUrlInfo on NetworkMessageId
| summarize Subjects = make_set(Subject), Senders = make_set(SenderFromAddress) by EmailClusterId
| extend TotalSenders = array_length(Senders)
| where TotalSenders >= TotalSenderThresholdAttachment name analysis
In QR code campaign investigations, experts have observed attackers often randomize attachment names. This means each email includes a QR code attachment with a unique and highly randomized name. Emails featuring randomly named attachments from the same sender sent to numerous recipients, usually exceeding 50, may signify a QR code phishing campaign.
Campaign with randomly named attachments:
EmailAttachmentInfo
| where Timestamp > ago(7d)
| where FileType in ("jpg", "jpeg", "png", "gif", "svg")
| where isnotempty(FileName)
| extend firstFourFileName = substring(FileName, 0, 4)
| summarize RecipientsCount = dcount(RecipientEmailAddress), FirstFourFilesCount = dcount(firstFourFileName), suspiciousEmails = make_set(NetworkMessageId, 10) by SenderFromAddress
| where FirstFourFilesCount >= 10Identifying compromised Identities
Alongside detecting campaigns, it’s vital to pinpoint compromised identities. We can achieve this through the following methods.
Risky sign-in attempts from unmanaged devices
Any sign-in attempt from an unmanaged, non-compliant, or untrusted device warrants attention. Increased risk scores for such attempts highlight anomalous activities, aiding in the identification of compromised identities.
AADSignInEventsBeta
| where Timestamp > ago(7d)
| where IsManaged != 1
| where IsCompliant != 1
//Filtering only for medium and high risk sign-in
| where RiskLevelDuringSignIn in (50, 100)
| where ClientAppUsed == "Browser"
| where isempty(DeviceTrustType)
| where isnotempty(State) or isnotempty(Country) or isnotempty(City)
| where isnotempty(IPAddress)
| where isnotempty(AccountObjectId)
| where isempty(DeviceName)
| where isempty(AadDeviceId)
| project Timestamp,IPAddress, AccountObjectId, ApplicationId, SessionId, RiskLevelDuringSignInUser signal and cluster analysis
Attackers gather user data from social media to tailor large-scale QR code phishing attacks, targeting thousands of users within organizations. Alerts triggered by vigilant users reporting suspicious emails serve as starting points for hunting activities, revealing campaign scope and compromised accounts. Traditional scoping methods may prove ineffective due to personalized campaigns. Microsoft Defender for Office offers a heuristic approach, clustering emails with similar content. These clusters consolidate phishing attempts, aiding in uncovering persistent phishing techniques. Below is a sample query for scoping a campaign using reported emails.
let suspiciousClusters = EmailEvents
| where Timestamp > ago(7d)
| where EmailDirection == "Inbound"
| where NetworkMessageId in (<List of suspicious Network Message Ids from Alerts>)
| distinct EmailClusterId;
EmailEvents
| where Timestamp > ago(7d)
| where EmailDirection == "Inbound"
| where EmailClusterId in (suspiciousClusters)
| summarize make_set(Subject), make_set(SenderFromDomain), dcount(RecipientObjectId),dcount(SenderDisplayName) by EmailClusterIdMitigations to help you against this
Apply these mitigations to reduce the impact of this threat for your tenant:
- Educate and make awareness to users about the risks of QR code phishing emails – this is a must and a place to start.
- Implement Microsoft Defender for Endpoint – Mobile Threat Defense for Configure Network Protection/Web Protection on mobile devices used to access enterprise assets – I use it on my personal devices, as I have my own Microsoft 365 setup with it all private 🤪
- Microsoft Defender for Mobile is accessible on Android and iOS devices, offering anti-phishing features that prevent access to phishing sites. This includes safeguarding against malware potentially downloaded through malicious URLs.
- Remember that this feature applies the following licenses only:
- Make sure to configure anti-spam, anti-malware, anti-phishing, safe attachments, and other essential security measures in your organization.
- Monitor suspicious or anomalous activities in Microsoft Entra ID Protection. Investigate sign-in attempts with suspicious characteristics (etc. location, user agent, and use of anonymizer services).
- Enable Conditional Access policies in Microsoft Entra ID, especially the risk-based access policies. Conditional access policies evaluate sign-in requests using additional identity-driven signals like user or group memberships, location information and IP address, device status and many more, used to protect suspicious sign-ins. You can protect stolen credentials by enabling policies such as compliant devices or risk-based policies with proper access control.
- Implement continuous access evaluation.
- Implement Microsoft Entra passwordless sign-in with FIDO2 security keys or soon device keys!
- Turn on network protection in Microsoft Defender for Endpoint to block connections to malicious domains or IP addresses.
Create a custom detection rules
Custom detection rules are advanced hunting queries enabling proactive surveillance of suspicious events. They provide proactive monitoring of the threat landscape, generating incidents/alerts and triggering automatic email remediation actions. Learn more about creating and managing them at Create and manage custom detection rules in Microsoft Defender XDR | Microsoft Learn.
To tackle emerging QR code-based attacks, security teams can create a custom detection rule to monitor sender prevalence in the past 14 days. This helps identify malicious activity in emails with QR codes. Below is a sample rule:
let QRCode_emails = EmailUrlInfo
| where Timestamp > ago (2d)
| where UrlLocation == "QRCode"
| distinct Url,NetworkMessageId;
let nMIDs = QRCode_emails | distinct NetworkMessageId;
// Extracting the sender of the email with QRCode
let senders_NMIDs = EmailEvents
| where Timestamp > ago (2d)
| where DeliveryLocation != "Blocked" // Only delivered or Junked emails are interesting...
| where isnotempty(NetworkMessageId)
| where NetworkMessageId in (nMIDs)
| distinct Timestamp, NetworkMessageId, RecipientEmailAddress, SenderFromAddress, InternetMessageId, RecipientObjectId, ReportId;
let senders = senders_NMIDs
| distinct SenderFromAddress;
// Checking sender prevalence in the organization
let senderprevalence = EmailEvents
| where Timestamp between (ago(14d)..(now()-24h))
| where isnotempty(SenderFromAddress)
| where SenderFromAddress in (senders)
| summarize TotalEmailCount = count() by SenderFromAddress
| where TotalEmailCount > 1;
let prevalent_Sender = senderprevalence
| where isnotempty (SenderFromAddress)
| distinct SenderFromAddress;
// Checking if in clicked emails sender was not prevalent
let nMIDs_from_non_prevalent_Senders = senders_NMIDs
| where SenderFromAddress !in (prevalent_Sender)
| distinct NetworkMessageId;
let QRCode_emails_from_non_prevalent_senders = QRCode_emails
| where NetworkMessageId in (nMIDs_from_non_prevalent_Senders)
| join kind=inner senders_NMIDs on NetworkMessageId
| project Timestamp,Url, NetworkMessageId, InternetMessageId, RecipientObjectId, ReportId;
QRCode_emails_from_non_prevalent_sendersAnd finally – user awareness!
Educating end-users about the potential risks associated with QR codes is crucial. Defender for Office 365 offers Attack Simulation Training to raise awareness about QR code phishing.
It can the basic stuff, and it´s a good start to try to see and “hunt” in your organization! 🤘
Moreover, there have been numerous occasions when colleagues or clients have reached out to me for assistance, asking whether a mail they received is safe or potentially malicious. This highlights the importance of not only educating individuals about the risks but also providing them with the tools and knowledge to make informed decisions when interacting with etc. QR codes.
By getting a proactive approach within organizations and empowering individuals to discern the legitimacy of this, we can significantly mitigate the risks associated with QR code phishing attacks. It’s not just about reacting to threats but also about fostering a culture of vigilance and digital safety! 🔒
Requirements
This training includes simulations specifically designed to educate users about QR code-based phishing attacks. Accessible with Microsoft 365 E5 or Microsoft Defender for Office 365 P2.
You need membership in one of the following roles:
- Global Administrator
- Security Administrator
- Attack Simulation Administrators: Create and manage all aspects of attack simulation campaigns.
- Attack Payload Author: Create attack payloads that an admin can initiate later.
Setup a new end user training
- Open Microsoft Defender portal at https://security.microsoft.com. Attack simulation training is available at Email and collaboration > Attack simulation training. To go directly to Attack simulation training use https://security.microsoft.com/attacksimulator.
- Go to the Simulations tab – here you can create a simulation in your tenant

- Now select the type How-to Guide and click Next

- Set a name and a description for the new simulation you will create like this – and press Next

- Under Select payload and login page, select Teaching guide: How to report phishing messages. As a part of the payloads is the following payload available we need: Teaching Guide: How to recognize and report QR phishing messages

- Click on Next and assign users to target for the new training.
- Set the mode for end user notifications (you have the option to create your own if needed)

- New setup the Launch details and click on Next

- Review simulation and if all is okay, press Submit – now it is ready to start 😎👌
Remember that targeted users there is not allowed to signin cant get the simulation emails:

Read more here: Get started using Attack simulation training | Microsoft Learn
Conclusion
In the face of evolving cyber threats, it’s crucial for organizations to stay vigilant and continually strengthen their defense mechanisms. With the rise of QR code phishing attacks, particularly amid the COVID-19 pandemic, it’s evident that attackers are becoming increasingly sophisticated in their tactics.
However, with the enhanced capabilities of Defender for Office 365, organizations can effectively combat QR code-based threats. By leveraging advanced detection methods, such as image detection, threat signals analysis, URL analysis, heuristic-based rules, and utilizing KQL (Kusto Query Language) queries in Advanced Hunting, Defender offers comprehensive protection against malicious QR codes embedded in emails.
Furthermore, the integration of sandboxing technology ensures that threats are detected and mitigated swiftly, bolstering the overall security posture of organizations.
Through proactive monitoring, user awareness training, and robust security configurations, organizations can mitigate the risks posed by QR code phishing attacks and safeguard their sensitive data and assets.
By adopting a multi-layered approach to cybersecurity and leveraging the capabilities of Defender for Office 365, organizations can stay ahead of emerging threats and protect their digital environments effectively.
What do you think about this? 🤔🤘
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳
References
Advanced hunting example for Microsoft Defender for Office 365 | Microsoft Learn
Data tables in the Microsoft Defender XDR advanced hunting schema | Microsoft Learn
Create and manage custom detection rules in Microsoft Defender XDR | Microsoft Learn
Get started using Attack simulation training | Microsoft Learn
Choose between guided and advanced modes for hunting in Microsoft Defender XDR | Microsoft Learn