Last Updated on April 27, 2024 by Michael Morten Sonne
Table of Contents
- Intoduction
- Permissions Management and Defender for Cloud – the different capabilities
- Requirements
- Setup Permissions Management in Microsoft Defender for Cloud
- See the recommendations there is discovered
- Supported recommendations (Azure)
- How to use it
- Create a custom role based on data from the export
- Read more
- Conclusion
Intoduction
In Public Preview as this post is written
In the ever-evolving landscape of cloud-based infrastructures, safeguarding sensitive data and ensuring controlled access to resources stands as a paramount concern for many organizations today.
Throughout my time in IT, I’ve etc. encountered numerous instances where excessive rights were assigned to users and service accounts, particularly in platforms like Azure as I have been working with (yes, sorry GCP, AWS, Alibaba users and so on 🤣).
This often includes granting Owner access on hole Azure subscriptions (now you should look at Azure landing zones….) or even Global Administrator privileges on service accounts – why, don´t aske me as I not know the answer – but it´s not good! 🙈
Please take a look at the Azure roles and related aspects at Azure built-in roles – Azure RBAC | Microsoft Learn and Azure custom roles – Azure RBAC | Microsoft Learn to see what permissions/roles there is and how much power they give individual.
The lists contain a variety of options, ensuring there’s one suited to your needs without granting access to the entire kingdom. Alternatively, you can utilize a custom role, as demonstrated later in my post, for these roles used for identityes exported from the Cloud Infrastructure Entitlement Management (CIEM) Defender for Cloud recommendation!
However Entra ID/Microsoft 365 role is NOT addressed by this feature.
By adhering to the principle of least privilege (PoLP), CIEM ensures that users possess only the minimum access necessary for their designated tasks – and this is a need! 🔐
Cloud Infrastructure Entitlement Management (CIEM) stands as a pivotal security model in managing user access and entitlements within cloud infrastructures. Microsoft offers two key components – Microsoft Defender for Cloud and Microsoft Entra Permissions Management – each addressing distinct facets of cloud security.
While Defender for Cloud focuses on securing cloud-native applications, Permissions Management specializes in fine-grained access control across multicloud environments. This explores how integrating Permissions Management capabilities into Defender for Cloud enhances security measures by proactively managing and monitoring cloud entitlements. This combined approach becomes essential for mitigating security risks, minimizing attack surfaces, and ensuring regulatory compliance in today’s dynamic cloud landscape.
There was send some ideers back to the teams too, and lets see if some of them comming in the future or not.
This is the stuff and features we can start to play around with – lets do that!
Permissions Management and Defender for Cloud – the different capabilities
So that you can see a bit more of what it’s about, here’s a bit in short term 😁
| Category | Capabilities | Defender for Cloud | Permissions Management |
|---|---|---|---|
| Discover | Permissions discovery for risky identities (including unused identities, overprovisioned active identities, super identities) in Azure, AWS, GCP | ✓ | ✓ |
| Discover | Permissions Creep Index (PCI) for multicloud environments (Azure, AWS, GCP) and all identities | ✓ | ✓ |
| Discover | Permissions discovery for all identities, groups in Azure, AWS, GCP | ❌ | ✓ |
| Discover | Permissions usage analytics, role / policy assignments in Azure, AWS, GCP | ❌ | ✓ |
| Discover | Support for Identity Providers (including AWS IAM Identity Center, Okta, GSuite) | ❌ | ✓ |
| Remediate | Automated deletion of permissions | ❌ | ✓ |
| Remediate | Remediate identities by attaching / detaching the permissions | ❌ | ✓ |
| Remediate | Custom role / AWS Policy generation based on activities of identities, groups, etc. | ❌ | ✓ |
| Remediate | Permissions on demand (time-bound access) for human and workload identities via Microsoft Entra admin center, APIs, ServiceNow app. | ❌ | ✓ |
| Monitor | Machine Learning-powered anomaly detections | ❌ | ✓ |
| Monitor | Activity based, rule-based alerts | ❌ | ✓ |
| Monitor | Context-rich forensic reports (for example PCI history report, user entitlement & usage report, etc.) | ❌ | ✓ |
What can you use it for
In general, with this added capabilities for Permissions Management, you can track permissions analytics, unused permissions for active identities, and over-permissioned identities then act to mitigate to support the best practice of least privilege (PoLP) in Defender for Cloud.
If you or others are following or utilizing the CIS Framework (Center for Internet Security), here is why it matters: Election Security Spotlight – Principle of Least Privilege (cisecurity.org).
Common use cases and scenarios
You will now have the ability to track inactive identities and identify unused permissions associated with active identities, allowing you to mitigate them in support of the “least privilege” best practice – yes, thats right!
Here are additional common use cases and scenarios where integrating Permissions Management capabilities into Defender for Cloud can be beneficial:
- Access Reviews and Recertification: Conduct regular access reviews to ensure that permissions granted to identities align with current job roles and responsibilities. Implement recertification processes to periodically validate and adjust access rights, minimizing the risk of unauthorized access due to outdated permissions.
- Risk Assessment and Prioritization: Employ Permissions Management to assess and prioritize risks associated with over-permissioned identities or unused access rights. This helps in focusing efforts on high-risk areas and effectively managing security vulnerabilities.
- Role-Based Access Control (RBAC) Optimization: Analyze and refine Role-Based Access Control (RBAC) models by identifying gaps or inconsistencies in access permissions. Optimize RBAC structures to ensure that roles accurately reflect organizational needs while maintaining the principle of least privilege.
- Security Policy Compliance Monitoring: Continuously monitor cloud environments to ensure compliance with internal security policies, industry regulations, and standards. Permissions Management assists in identifying deviations from these policies and enables swift actions to enforce compliance.
- Mitigation of Super Identities: CIEM helps identify and mitigate super identities, which may have excessive permissions. Super identities with broad access can pose a significant security risk, and CIEM supports the identification and correction of such issues.
Integrating Permissions Management into Defender for Cloud empowers organizations to tackle a broad spectrum of security challenges, enabling proactive risk mitigation, compliance enforcement, and optimization of access controls across their cloud infrastructures.
Requirements
- An Azure subscription with Cloud Security Posture Management (Defender CSPM) enabled on – and the best part is that it’s included in the exitsing edition – no special top on add-ons – free stuff added to exising services is always nice right? 😉😎
- Required Roles & Permissions
- AWS \ GCP (not covered in this post):
- Security Admin
- Application.ReadWrite.All
- Azure
- Security Admin
- Microsoft.Authorization/roleAssignments/write
- AWS \ GCP (not covered in this post):
Setup Permissions Management in Microsoft Defender for Cloud
To setup this, you need to do some steps and you need the right permissions (see abow).
In this post, I demonstrate how to set it up for Azure, as it’s the public cloud platform currently accessible to me.
It´s easy so you can just do it right away 😉
- Sign in to the Azure portal with your admin account with the right permissions for the subscriptions you will enable this on.
- In the search bar in the Azure Portal, search for Microsoft Defender for Cloud and click on this.
- In the left menu bar in Microsoft Defender for Cloud, select Environment settings. (here is a direct link: Microsoft Defender for Cloud – Microsoft Azure)
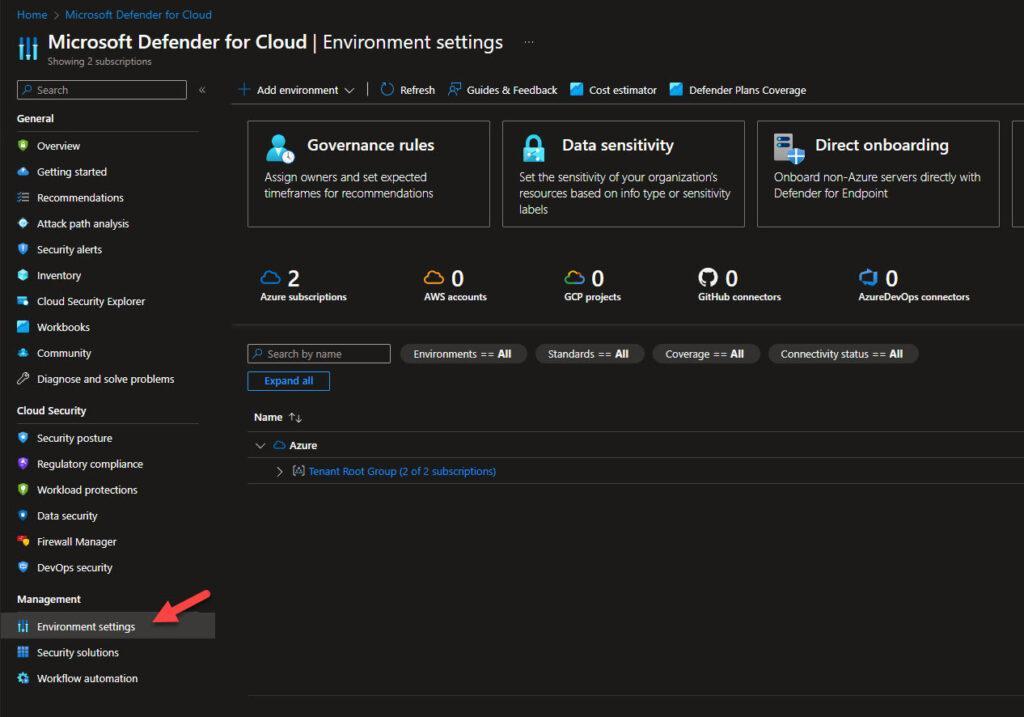
- Now select the Azure subscription that you’d like to turn on the DCSPM CIEM plan on
- On the Defender plans page, make sure that the Defender CSPM plan is turned on. For more information about priceing – check out this page: Pricing—Microsoft Defender | Microsoft Azure)
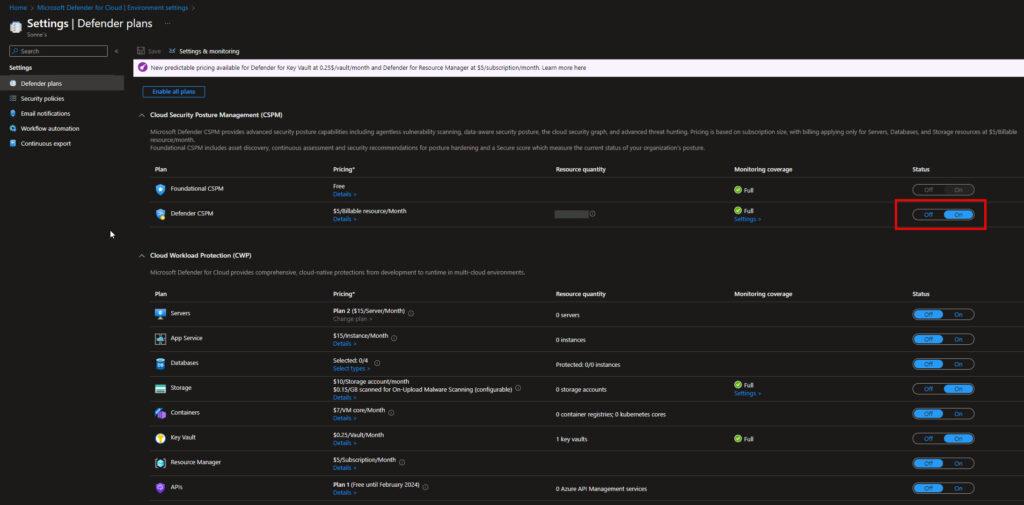
- Now select the Defender CSPM plan settings
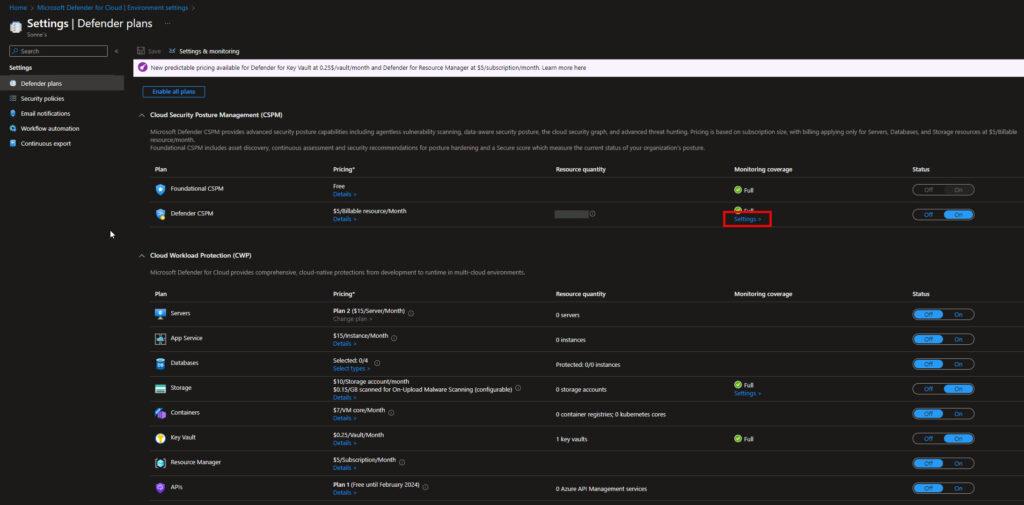
- On the Settings & monitoring page, make sure that the Permissions Management (Preview) extension is turned on.
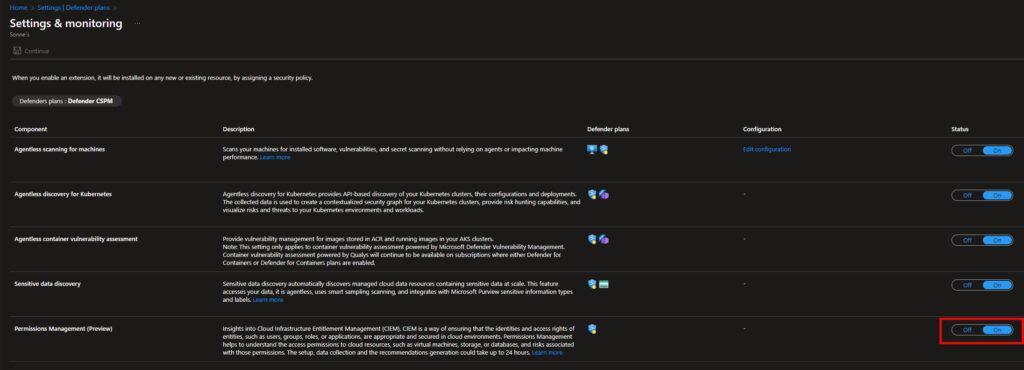
- Select Continue to the top left.
- Select Save on the Defender plans page you are redirected to.
After a few seconds, you wil notice that:
- Your subscription you selected to enabled this is on, now has a new Reader role assignment for the Cloud Infrastructure Entitlement Management application.
- The new Azure CSPM (Preview) standard is assigned to your subscription under Security policies.
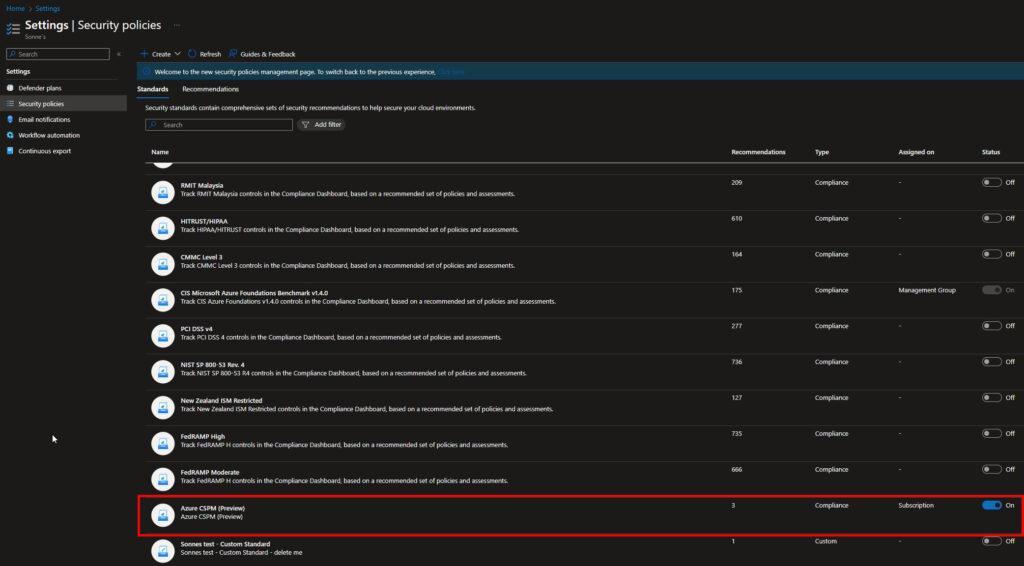
You have now completed the configuration, and now all that’s left is to await the backend to display the new recommendations – it can take some hours! 🎉
That was easy right? 😎
See the recommendations there is discovered
Go to the All recommendations page in Microsoft Defender for Cloud under Recommendations and make sure that the relevant environments filters are checked.
Filter by Initiative= “Azure CSPM (Preview)” which filters the following recommendations (if applicable for your tenant ofc.) as that is faster to see them – as there can be a long list:
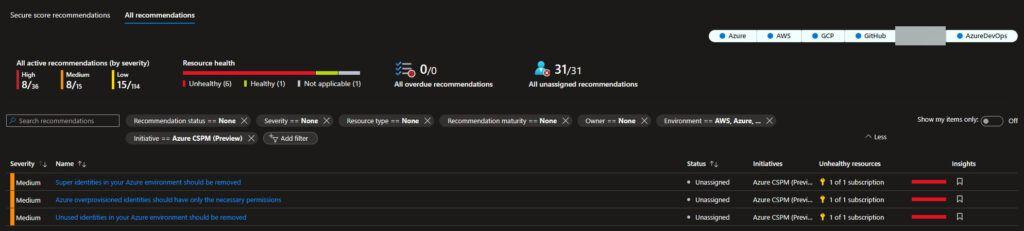
Supported recommendations (Azure)
Here is the current list of supported recommendations for Azure.
- Azure overprovisioned identities should have only the necessary permissions
- Super Identities in your Azure environment should be removed
- Unused identities in your Azure environment should be removed
How to use it
You can now find the new recommendations in the Manage Access and Permissions Security Control overview under the Recommendations tab in the Defender for Cloud dashboard – smart! 😎
Details on the type of information provided
Here are the details if you navigate to the Unused identities in your Azure environment should be removed recommendation (if applicable).
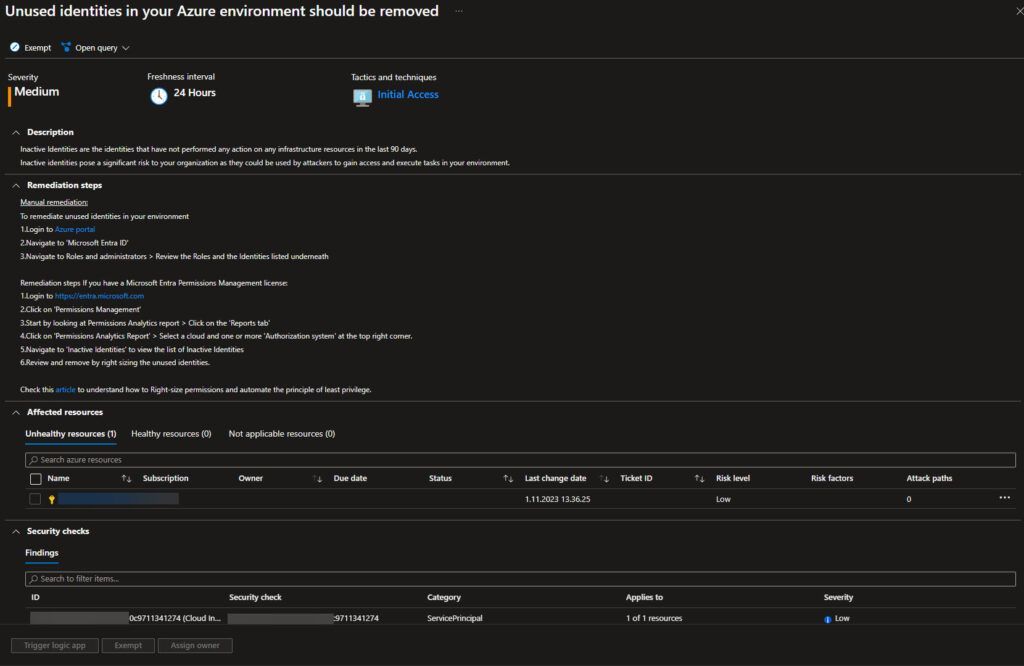
Here, you can click on different sections such as affected resources or identity.
You can etc. trigger a logic app, exempt or assign an owner and set a remediation timeframe and assinement type, just like in other Defender for Cloud recommendations.
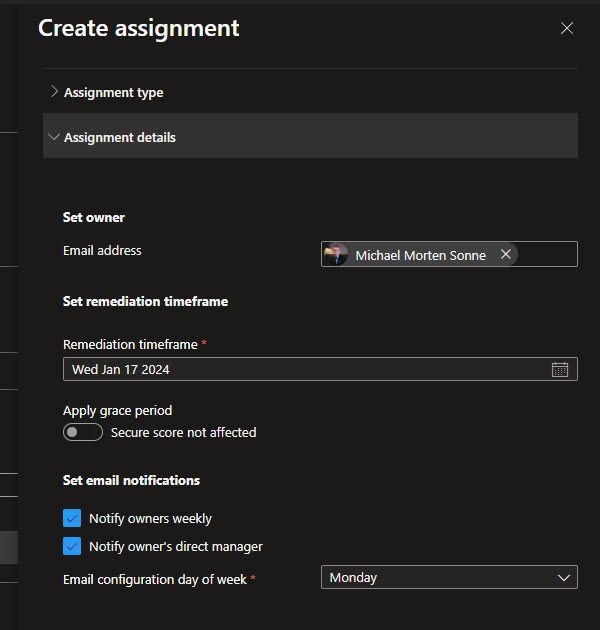
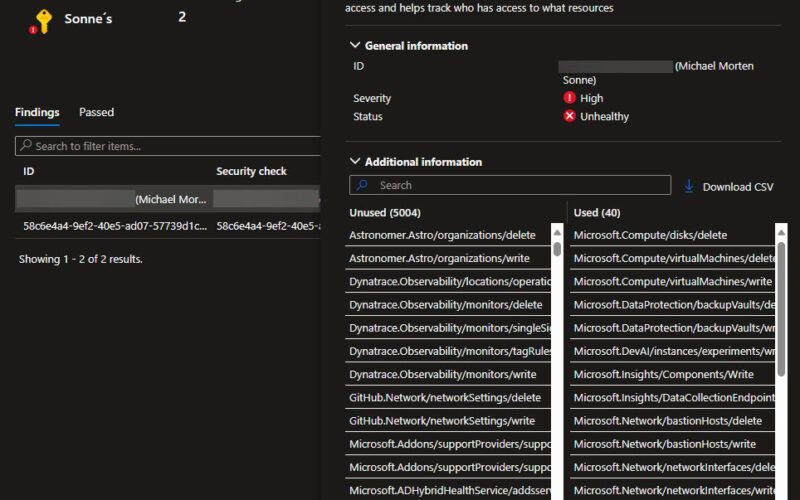
The permissions used vs not used for identities
This is only valid for the recommendation: Azure overprovisioned identities should have only the necessary permissions
This highlights the significance of the recommendation: Azure overprovisioned identities should be allocated only the necessary permissions to operate effectively while mitigating potential risks associated with excessive access rights.
Mitigating the risks linked to overprovisioned identities in Azure is a crucial aspect of maintaining a robust and secure cloud infrastructure. When identities are assigned more permissions than they actually need, it creates an environment open for potential security vulnerabilities and unauthorized access.
By use the the principle of allocating only the necessary permissions to identities within Azure, organizations can significantly reduce the attack surface and potential points of exploitation. This practice aligns with the concept of least privilege, ensuring that each identity—whether it’s a user account, service account, or application—only possesses the minimum privileges essential for its intended tasks! 🫡🔐
Implementing fine-grained access controls based on the principle of least privilege not only enhances security but also streamlines the management of permissions. It allows for a more granular approach to access management, ensuring that identities have precisely the permissions required to carry out their designated functions, without unnecessarily elevating their access levels.
Furthermore, adopting this approach minimizes the impact of a potential security breach. If a compromised identity with limited permissions is used maliciously, the potential damage and lateral movement within the system are significantly reduced compared to an identity with elevated privileges.
This recommendation also resonates with compliance requirements and best practices, emphasizing the importance of maintaining a secure and well-governed environment. It’s a proactive measure that supports regulatory compliance frameworks by demonstrating a deliberate and controlled approach to access management, which is often a critical aspect of audits and assessments.
How to see access scopes used and not used
- Within Microsoft Defender for Cloud under the Recommendations section, locate and choose the recommendation stating, Azure overprovisioned identities should have only the necessary permissions. Upon selecting this recommendation, you will find an overview presented in a format similar to this:
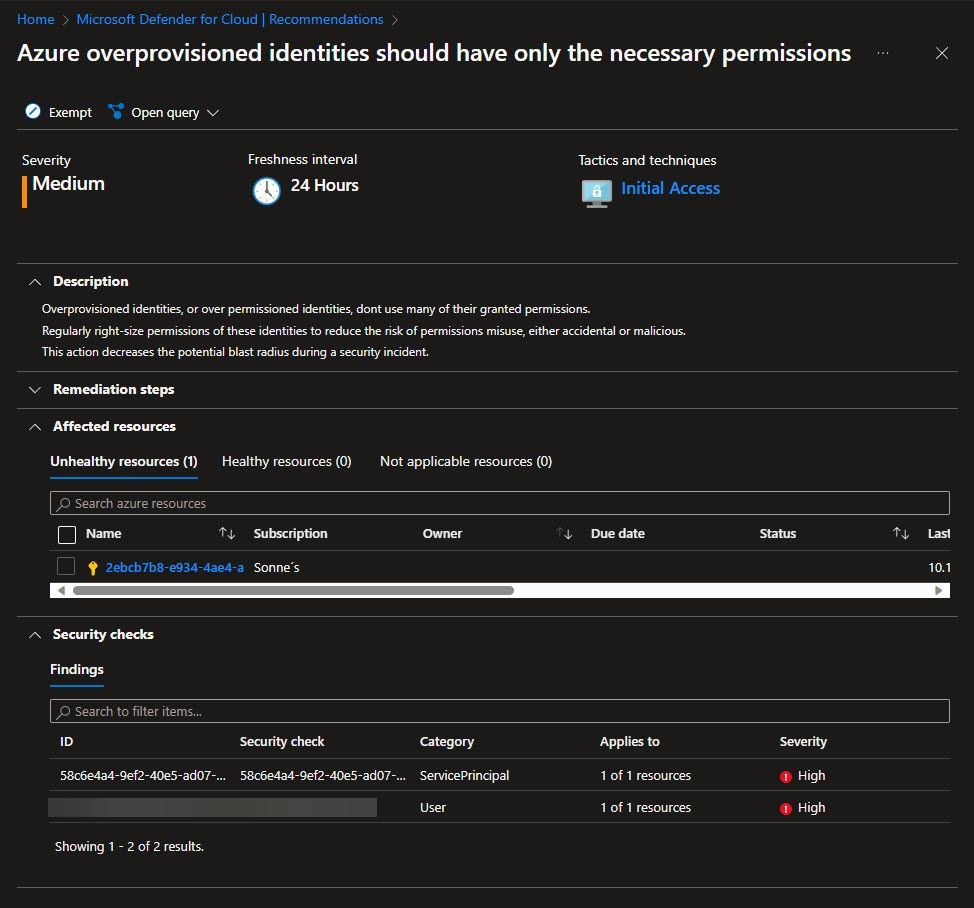
- Navigate to the section titled Unhealthy resources within the category of Affected resources, you will now find an overview presented in a format similar to this:
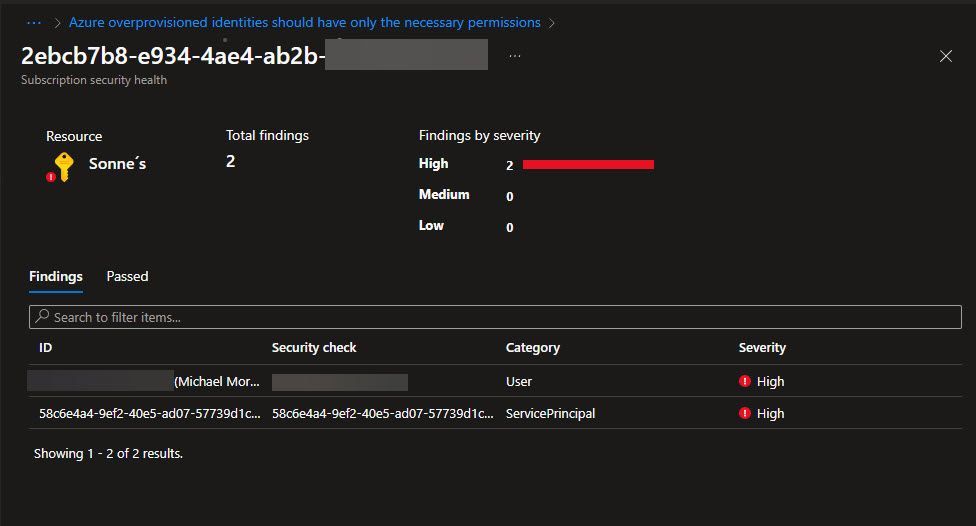
- Let’s proceed by selecting the user to review the permissions or “Scopes” utilized and those that haven’t been used. Following this step, you will discover an overview presented in a format like this.
Here, you’ll notice numerous unused access scopes, suggesting access that hasn’t been utilized yet – if not used, we can (should) remove it! 🔐
For a more detailed perspective, you have the option to download it in .csv format, which is a considerable improvement compared to its previous state during the private preview when it was solely available in raw JSON format – so the columns here is a bit better!
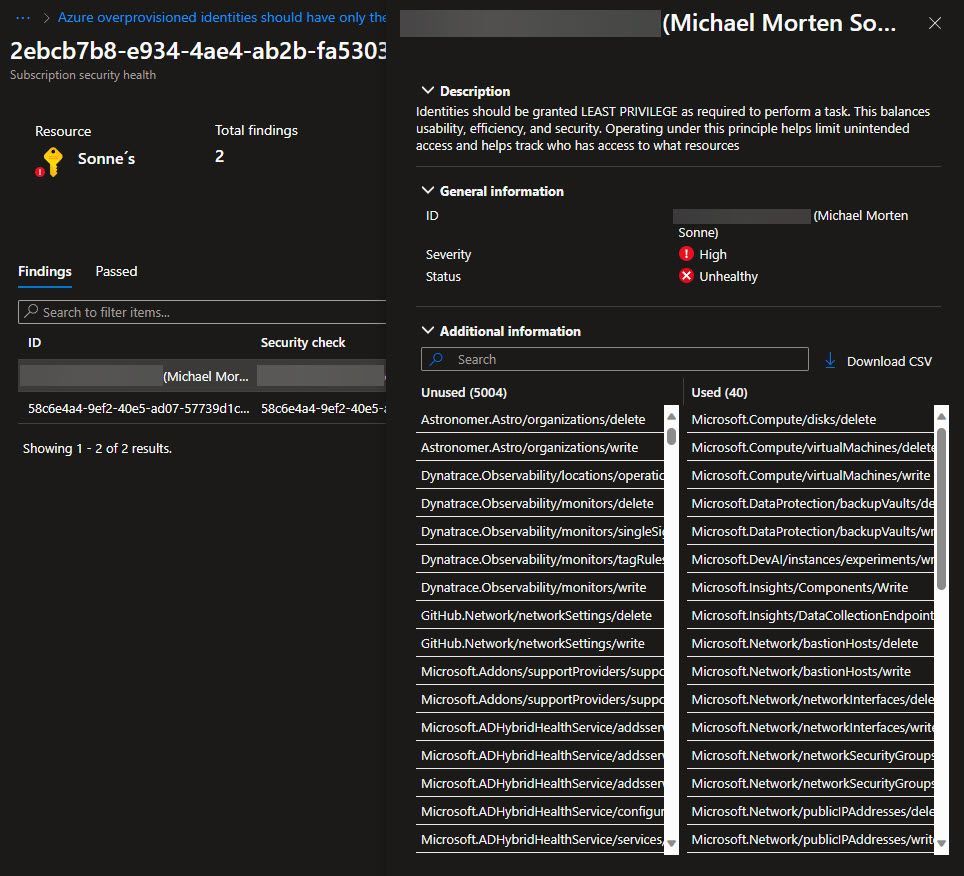
Create a custom Azure RBAC role based on this output, and you can use and assign the the needed user account, service account, or application.
On this way, you get into control of the permissions 🫡
Create a custom role based on data from the export
As you’ve observed, the overview could be improved if you will create a custom Azure RBAC Role or edit an existing if you use that today 😁
To help you I have then developed a small PowerShell script to generate a custom Azure RBAC role for you – yes thats right!
This is based on the permission scopes there is used and not the permissions scopes there not was used in the exported Actions.csv file you downloaded from Microsoft Defender for Cloud portal!
This allows you to create a custom role based on the report (downloaded .csv file from export in the recommendation). This feature is not built-in, and creating it manually can take some time ⌛
See the script on The PowerShell Script tab – it´s hosted on my public repo on my GitHub account here: https://github.com/michaelmsonne/public
You use the script like this in PowerShell:
.\'Create Azure RBAC Role based on CIEM access report.ps1' -CsvFilePath "C:\Users\MichaelMortenSonne\Downloads\Actions.csv"This will produce the following output within your console if you are logged into Azure. If you are not logged in, it will prompt you to do so.
(I can’t promise it will look like this all the time, as I can improve it over time 😁)
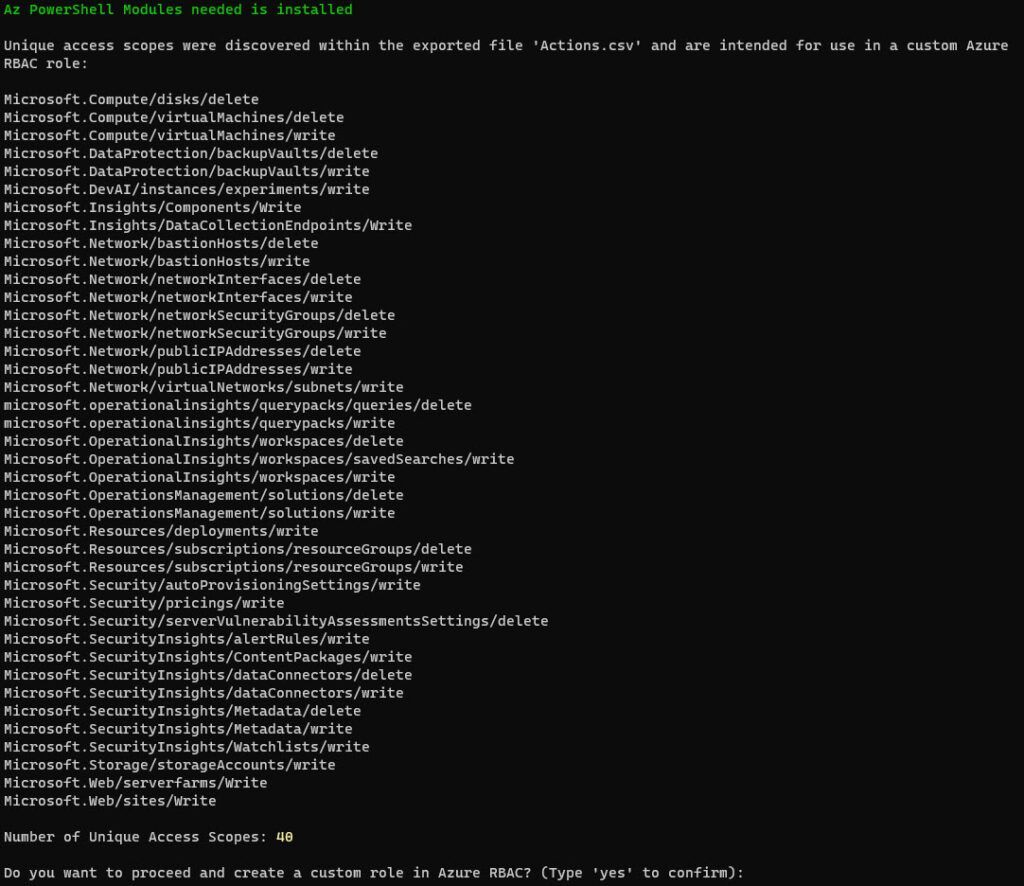
There is also a Grid view there pop-up if you have a large dataset – use the argument -GridView
You use the script like this in PowerShell:
.\'Create Azure RBAC Role based on CIEM access report.ps1' -GridView -CsvFilePath "C:\Users\MichaelMortenSonne\Downloads\Actions.csv"When the data is readed and ready to be used in the new custom Azure RBAC Role, the output will look like this and ask you for a name and a description:
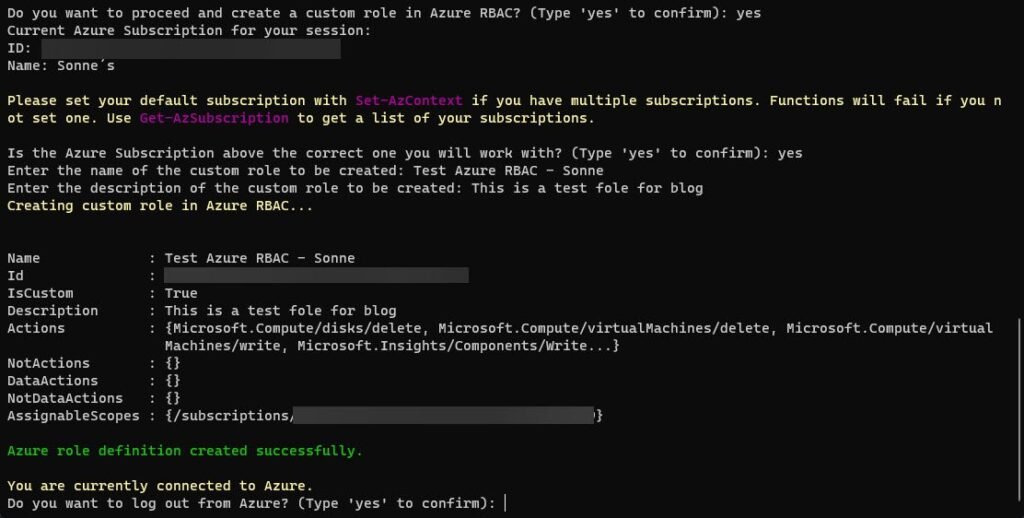
The custom Azure RBAC role has now been created in my Azure Subscription, and you should now be able to see it in your Azure Portal if is has been successful for you like for me here under Access control (IAM) > Roles and Type = Custom 😉
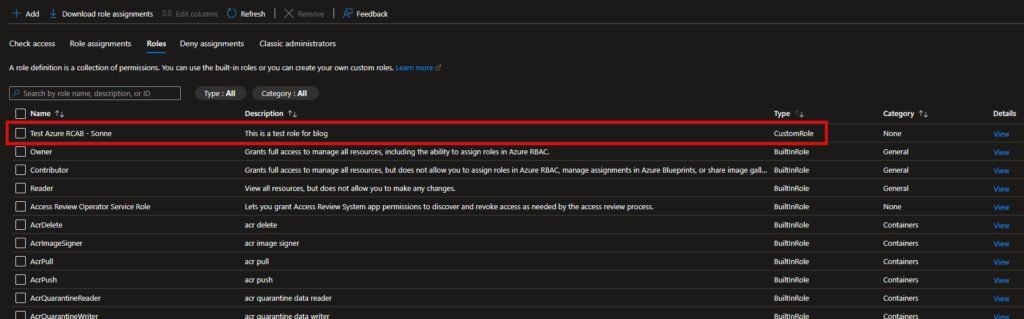
In the collum Details click on View to see the details for the Azure RBAC role you now have created based on the input from the export from Defender for Cloud, the role should have the same permissions.
You can verify it here for the GUI view for the Azure RBAC role:
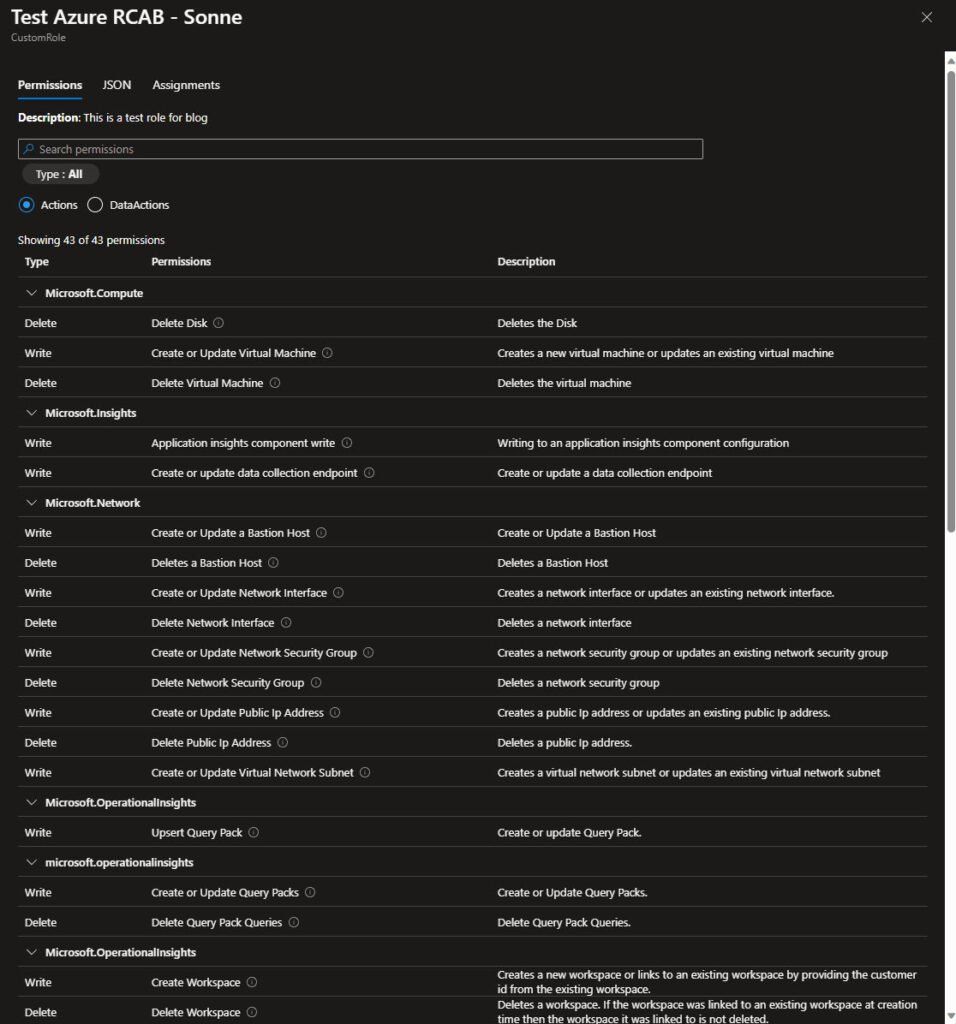
And here is the JSON view for the Azure RBAC role:
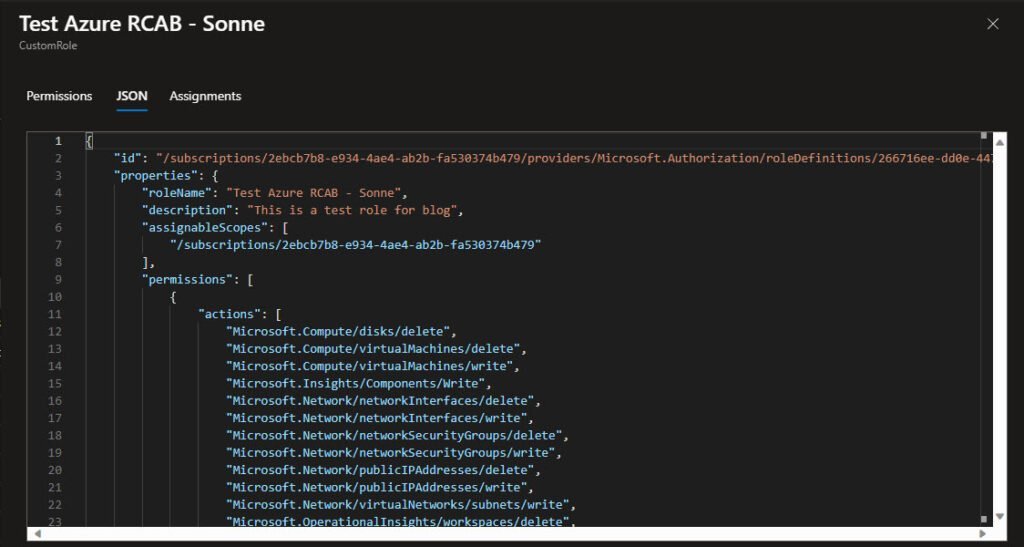
Now that you have a custom Azure RBAC role ready to use, you can take control with this and rock! 😎
In our quest for enhanced cybersecurity, we’ve crafted a custom Azure RBAC role meticulously designed to adhere to the principle of least privilege (PoLP). This role empowers organizations to assign users and service identities with precisely the permissions they need, minimizing potential security risks.
Prior to deployment in production, extensive testing and validation in controlled environments validate the role’s effectiveness. Comprehensive documentation detailing the role’s purpose and permissions serves as a crucial reference point for auditing, compliance, and collaborative efforts within the team.
Aligning with Azure RBAC best practices, our strategy emphasizes the use of groups over direct user assignments, regular role reviews, and close monitoring of role assignments. Integration with Azure Policy further strengthens our organization’s standards and compliance.
Check out this regarding Steps to assign an Azure role – Azure RBAC | Microsoft Learn
The PowerShell script:
Read more
Read more about Microsoft Entra Permissions Management itself, take a look here: What’s Microsoft Entra Permissions Management? – Microsoft Entra Permissions Management | Microsoft Learn
What is Microsoft Defender for Cloud? – Microsoft Defender for Cloud | Microsoft Learn
Conclusion
Ensuring proper management of permissions within Azure is paramount for maintaining a secure and optimized cloud environment. By adhering to the principle of etc. least privilege and regularly reviewing and refining access scopes, organizations can significantly reduce security risks associated with overprovisioned identities.
The integration of Cloud Infrastructure Entitlement Management (CIEM) can provide unparalleled visibility into user access and entitlements within the cloud infrastructure. I’ve observed that many tenants tend to grant excessive permissions, and CIEM can be a game-changer in such scenarios, as it provides an overview of what is “needed” versus what is “used.”
I have a list of Suggestions for Improvement there is shared with the Product team – so lets see what is happening there, as I could understand that the team was very happy about that and my feedback in general! My answer back on all that was: “wow this is mindblowing” 🙈
N.B: I can´t shere my list – so you know that now.
Microsoft Defender for Cloud offers valuable insights and tools to identify unused access scopes with this add-on of features, and it enabling administrators to fine-tune permissions effectively. Embracing these practices not only enhances security posture but also streamlines operations, contributing to a more robust and efficiently managed Azure infrastructure. Here my script can help you a good way to, so you not have to create it by hand 😉
It was also for me fun to test this with the product team under the development as a member of Microsoft Customer Connection Program – www.aka.ms/JoinCCP.
I had quite a fun dialogue about this the Microsoft Defender for Cloud team doing the Private Preview time and after!
Here in Feb. 2024 I got more feedback on this from more people in the Defender for Cloud team – I got startements back like “That’s awesome, thanks for sharing @Michael!” and “Got it. That’s awesome. Thanks for creating it and sharing!!”.
And from one of the Software Developers I got even this: “This is a great remediation script! Thanks @Michael for sharing.”
So my script can you find here too: Defender for Cloud’s GitHub repository (they will have it, so I got it approved!)
(I know the names, but is not stated here with names as requested)
This is then shared now as the announcing is public – as else, under NDA with information I cant share.
Continuous improvement remains at the forefront of our security approach. Regular reviews and refinements ensure that our RBAC strategy evolves alongside changes in organizational needs, applications, and Azure services.
Our custom Azure RBAC role with least privilege is not just a security measure; it’s a proactive step towards creating a robust, adaptive, and secure cloud environment.
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳