Last Updated on July 5, 2023 by Michael Morten Sonne
Table of Contents
- Intoduction
- Security in the days
- Principles for Protecting your Microsoft 365 from on-premises compromise
- Isolate your privileged identities in Microsoft 365 and Azure AD
- Use cloud authentication
- What is the benefits of moving to Cloud only Administrative Accounts
- Exclutive features for Cloud-only Administrative Accounts vs On-prem classic Accounts
- Best Practices for Cloud-only Administrative Accounts
- Conditional Access Policies – use it!
- Monitoring
- Log Management
- Conclusion
Intoduction
Frist – sorry for the size og this, but I think it was difficult to omit some of it – and optimally there would probably have been 2 parts 🥹
In this post, I will write about why use Cloud Only Administrative/normal user accounts in Azure AD, and not a synced account from your On-prem Active Directory (AD).
Many customers connect their private corporate networks to Microsoft 365 to benefit their users, devices, and applications. However, there are many well-documented ways these private networks can be compromised. As we have seen in recent events related to the SolarWinds compromise, on-premises compromise can propagate to the cloud. Because Microsoft 365 acts as the “nervous system” for many organizations, it is critical to protect it from compromised on-premises infrastructure.
Azure Active Directory (Azure AD) is a cloud-based identity and access management service provided by Microsoft that helps you manage user identities and create access policies to protect your resources, in the Cloud (Azure) or Microsoft 365 etc. Administrative accounts in Azure AD allow you to manage and secure resources in the cloud. Whether you have one resource or one hundred, Azure AD simplifies administration and enhances your security posture in one central place! 😁
Azure AD offers a seamless way to manage and secure administrative accounts. It solves the problems of on-premises administration by providing simplified management and enhanced security through features such as Azure AD Roles and Permissions, Privileged Identity Management, Conditional Access Policies, and Multi-factor Authentication – this exists NOT in an On-prem Active Directoy setup default if supported 😅
This post is also related to the setup and use of Cloud Only “break the glass” accounts in Azure AD – see more about this in the post here: Break Glass account – and how to get notified when a Break Glass account is used
Here is some basic topics to look at for you – keep up the good work! 👷
Security in the days
A good cloud environment has strict security policies – as most of it can be accessed on the public internet. Well-known policies there is setup are conditional access policies in Azure AD. Policies that require a compliant device before login for example or forcing MFA. Configuring conditional access is good but there is always a risk of lockout yourself if setup the wrong way. To not lock yourself out, you must create an emergency account! 😲
Principles for Protecting your Microsoft 365 from on-premises compromise
To address the threat vectors here, its recommend to follow the principles below here:
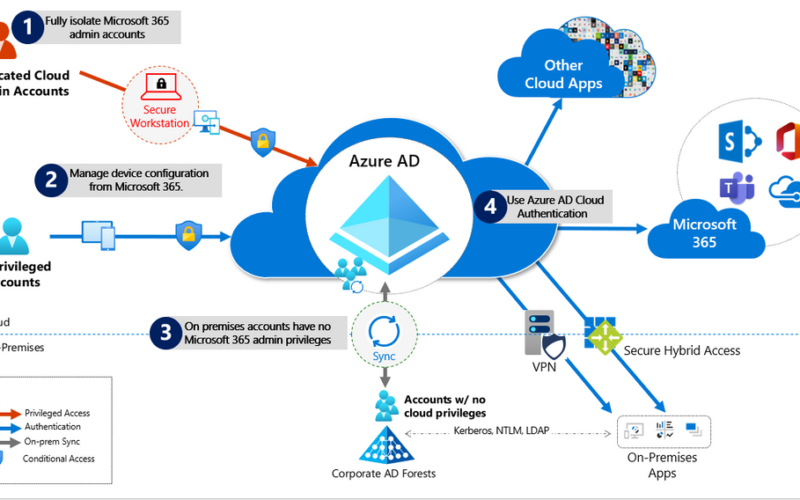
- Fully Isolate your Microsoft 365 administrator accounts. They should be:
- Mastered in Azure AD.
- Authenticated with Multi-factor authentication (MFA) – if possibel via hardware tokens > FIDO2 security keys like I do personal (and normal non-admin account to)!
- Secured by Azure AD conditional access
- Accessed only by using Privileged Access Workstation
These are restricted use accounts. There should be no on-premises accounts with administrative privileges in Microsoft 365. For more information see this overview of Microsoft 365 administrator roles. Also see Roles for Microsoft 365 in Azure Active Directory.
- Manage devices from Microsoft 365. Use Azure AD Join and cloud-based mobile device management (MDM) to eliminate dependencies on your on-premises device management infrastructure, which can compromise device and security controls.
- No on-premises account has elevated privileges to Microsoft 365. Accounts accessing on-premises applications that require NTLM, LDAP, or Kerberos authentication need an account in the organization’s on-premises identity infrastructure. Ensure that these accounts, including service accounts, are not included in privileged cloud roles or groups and that changes to these accounts cannot impact the integrity of your cloud environment. Privileged on-premises software must not be capable of impacting Microsoft 365 privileged accounts or roles.
To find use of unsecure protocols, check this post out too: Find Active Directory accounts configured to use DES and RC4 Kerberos encryption (is insecure!)
- Use Azure AD cloud authentication to eliminate dependencies on your on-premises credentials. Always use strong authentication, such as Windows Hello, FIDO, the Microsoft Authenticator, or Azure AD MFA.
Understanding the primary threat vectors from compromised on-premises environments to the cloud
Your Microsoft 365 cloud environment benefits from an extensive monitoring and security infrastructure. Using machine learning and human intelligence that looks across worldwide traffic can rapidly detect attacks and allow you to reconfigure in near-real-time. In hybrid deployments that connect on-premises infrastructure to Microsoft 365, many organizations delegate trust to on-premises components for critical authentication and directory object state management decisions. Unfortunately, if the on-premises environment is compromised, these trust relationships result in attackers’ opportunities to compromise your Microsoft 365 environment 🫢
The two primary threat vectors are federation trust relationships and account synchronization. Both vectors can grant an attacker administrative access to your cloud.
- Federated trust relationships, such as SAML authentication, are used to authenticate to Microsoft 365 via your on-premises Identity Infrastructure (aka ADFS, Active Directory Federation Services). If a SAML token signing certificate is compromised, federation would allow anyone with that certificate to impersonate any user in your cloud 😲
Its now recommend you disable federation trust relationships for authentication to Microsoft 365 when possible, and migrate to Azure AD authentication.
Read more here: New capabilities that empower you to migrate more of your apps on AD FS to Azure AD – Microsoft Community Hub
- Account synchronization can be used to modify privileged users (including their credentials) or groups granted administrative privileges in Microsoft 365. Its now these days recommend you ensure that synchronized objects hold no privileges beyond a user in Microsoft 365, either directly or via inclusion in trusted roles or groups. Ensure these objects have no direct or nested assignment in trusted cloud roles or groups.
Get rid of ADFS?
ADFS is a Windows server role that’s used to federate applications using a local Active Directory infrastructure with the Azure AD service. The benefit of using ADFS is that it enables single sign-on access for app users, so that they don’t have to sign in for every app.
Possibly, though, ADFS isn’t easy to secure. It was said to have been exploited last year by the “Nobelium” advanced persistent threat group to tap Exchange Online e-mails. Alex Weinert, director of identity security at Microsoft, has advised using Azure AD as a best practice. However, if organizations do use ADFS, then they should also use a hardware security module with it.
Deciding whether to get rid of Active Directory Federation Services (ADFS) depends on your specific requirements and organizational needs. ADFS is a technology that allows for single sign-on (SSO) authentication across multiple systems or applications using a federated identity model. While ADFS has been widely used in the past, there are alternative identity and access management (IAM) solutions available today that may offer additional benefits.
Here are a few factors to consider when evaluating whether to get rid of ADFS:
- Cloud-first strategy: If your organization is adopting a cloud-first strategy or moving towards a hybrid or fully cloud-based infrastructure, you may find that cloud-native IAM solutions provide better integration and support for cloud services. Services like Azure AD, which offers native SSO capabilities and integration with various cloud applications, can simplify authentication and provide a seamless user experience.
- Complexity and maintenance: ADFS deployments can be complex to set up, configure, and maintain. They require dedicated infrastructure and expertise, which may involve additional costs and resources. Cloud-based IAM solutions often offer simplified management, automatic updates, and reduced maintenance overhead, allowing your IT team to focus on other critical tasks.
- Security and scalability: Modern IAM solutions offer robust security features, such as multi-factor authentication (MFA), conditional access policies, and risk-based authentication. They are designed to handle large-scale user populations and provide scalability and performance advantages over on-premises solutions like ADFS.
- User experience and productivity: Cloud-based IAM solutions often provide a better user experience, enabling seamless SSO across various devices and platforms. Users can access applications with a single set of credentials, improving productivity and reducing password fatigue.
- Integration capabilities: Consider the integration capabilities of alternative IAM solutions. Evaluate whether they can seamlessly integrate with your existing systems and applications, both on-premises and in the cloud. Look for compatibility with popular protocols and standards, such as SAML, OAuth, and OpenID Connect.
It’s important to note that migrating away from ADFS requires careful planning, including assessing your organization’s specific requirements, conducting a thorough impact analysis, and designing a comprehensive migration strategy. It’s recommended to involve your IT team, security experts, and stakeholders to evaluate alternatives and make an informed decision that aligns with your business goals and priorities so nothing is left broken and cant be used! 🏝️🔒
Here is a great post about miss use of ADFS from Nestori Syynimaa: Unnoticed sidekick: Getting access to cloud as an on-prem admin (aadinternals.com) – check it out – I think you will be surprised! 😲🫢
To see the current best practices from Microsoft about this read this: Best Practices for securing AD FS and Web Application Proxy
Isolate your privileged identities in Microsoft 365 and Azure AD
In Azure AD, users with privileged roles such as administrators (Global, Exchange and Security Administrator) are the root of trust to build and manage the rest of the environment. Implement the following practices to minimize the impact of a compromise:
- Use cloud-only accounts for Azure AD and Microsoft 365 privileged roles.
- Deploy Privileged Access Workstation for privileged access to manage Microsoft 365 and Azure AD to control the setup and complience for this devices.
- Deploy Azure AD Privileged Identity Management (PIM) for just in time (JIT) access to all human accounts that have privileged roles, and require strong authentication to activate the roles.
- Provide administrative roles the least privilege possible to perform their tasks – importent! 🔐
- To enable a richer role assignment experience that includes delegation and multiple roles at the same time, consider using Azure AD security groups or Microsoft 365 Groups (collectively “cloud groups”) and enable role-based access control. You can also use Administrative Units to restrict the scope of roles to a portion of the organization.
- Deploy Emergency Access Accounts and do NOT use on-premises password vaults to store the credentials.
Regarding use of this accounts, check out my post about Break Glass account – and how to get notified when a Break Glass account is used out!
Use cloud authentication

Credentials are a primary attack vector, as they can be shared and reused. Implement the following practices to make credentials more secure.
- Deploy passwordless authentication: Reduce the use of passwords as much as possible by deploying passwordless credentials. These credentials are managed and validated natively in the cloud. Choose from:
- Deploy Multi-Factor Authentication: Provision multiple strong credentials using Azure AD MFA. That way, access to cloud resources will require a credential that is managed in Azure AD in addition to an on-premises password that can be manipulated.
- For more information, see Create a resilient access control management strategy with Azure active Directory.
Limitations and tradeoffs
- Hybrid account password management requires hybrid components such as password protection agents and password writeback agents. If your on-premises infrastructure is compromised, attackers can control the machines on which these agents reside. While this will not compromise your cloud infrastructure, your cloud accounts will not protect these components from on-premises compromise.
I think I need to create a post about Azure Active Directory Password Protection 🤔😉
- On-premises accounts synced from Active Directory are marked to never expire in Azure AD, based on the assumption that on-premises AD password policies will mitigate for this. If your on-premises AD is compromised and synchronization from AD connect needs to be disabled, you must set the option EnforceCloudPasswordPolicyForPasswordSyncedUsers to control it.
What is the benefits of moving to Cloud only Administrative Accounts
Administrative accounts or aka “admins” are essential for managing user accounts, systems and protecting against various cyber threats for the organization. They provide almost access to sensitive information and systems that require heightened security. Therefore, it is essential to have secure administrative accounts to maintain the safety and integrity of company data! 😲
In the past (or for many still), on-premises administration was the norm. However, it has been proven to be challenging to manage, secure, and scale as organizations continue to grow and need the newest seccurity setups/features. The on-premises infrastructure requires large investments in hardware, software and operations, which increases costs. Managing on-premises infrastructure is time-consuming and demanding, taking away valuable time from critical business operations.
And furture more – there has NOT been so many “breaking” new features in Active Directory the last years 🥺🤯
- Increased Security: With cloud-only Administrative accounts, businesses gain access to Microsoft’s global enterprise-grade security infrastructure. Azure AD provides identity and access management, and role-based access control, which gives administrators granular access control over the company’s resources, thus ensuring that only authorized personnel access sensitive information
- Reduced Costs: Cloud-only administrative accounts offer cost advantages by reducing the dependence on physical hardware infrastructure while giving businesses greater flexibility to scale their operations. The reduced infrastructure investments enable businesses to redirect resources to their core competencies.
- Simplified Management: Administration is simplified with Azure AD since it provides a single console for managing administrative accounts, applications, and policies across cloud only or hybrid environments. It ensures that businesses have better visibility and control over their resources, which helps with regulatory compliance.
- Improved User Experience: Azure AD provides businesses with a straightforward and streamlined process, which makes it easier for users to access company resources. The simplified registration, sign-in, and password reset process ensures that users do not experience unnecessary delays or complications while accessing their accounts
- Integration with Other Azure Services: Moving to cloud-only administrative accounts facilitates seamless integration with other Azure services and features. Azure AD integrates with services like Azure Monitor and Azure Sentinel, enabling administrators to leverage the power of these services to gain insights, detect anomalies, and respond to security incidents effectively and fast.
- Compliance and Auditing: Azure AD provides features for compliance and auditing requirements. It offers granular controls and auditing capabilities to monitor administrative activities, ensuring that organizations can track and review administrative actions for compliance purposes. This helps meet regulatory requirements and internal governance policies.
Exclutive features for Cloud-only Administrative Accounts vs On-prem classic Accounts
Cloud-only administrative accounts provide several benefits to organizations, including increased security, reduced costs, simplified management, and improved user experience. The features of Azure AD make it easier for administrators to manage their administrative accounts, increase visibility and control over resources while maintaining regulatory compliance.
When it comes to cloud-only administrative accounts in Azure AD, there are various features that set it apart from on-premises administration. These features include Azure AD Roles and Permissions, Privileged Identity Management, Conditional Access Policies, and Multi-factor Authentication – with support for hardware tokens as well! 🥳
- Azure AD Roles and Permissions: Azure AD roles and permissions give administrators fine-grained access control over Azure resources and other cloud services.
- Auditing: Azure Active Directory monitors the sign-ins and with some alerts you can be aware of what is happening with those accounts.
- Conditional Access: Azure AD provides advanced Conditional Access policies that allow organizations to enforce specific access controls based on various conditions such as user location, device health, or user behavior. This feature is not available with on-premises classic accounts and provides an additional layer of security for cloud-only administrative accounts.
- Multi-Factor Authentication (MFA): Azure AD offers built-in support for MFA, which adds an extra layer of security by requiring users to provide multiple forms of authentication. This feature enhances the security of cloud-only administrative accounts and helps prevent unauthorized access in case of stolen or compromised credentials.
- Identity Protection: Azure AD Identity Protection helps detect and remediate potential identity vulnerabilities and risky sign-in behavior. It uses machine learning algorithms to analyze user activity and detect anomalies, such as sign-ins from unfamiliar locations or suspicious patterns. This feature provides proactive protection for cloud-only administrative accounts, reducing the risk of account compromise.
- Privileged Identity Management (PIM): Azure AD Privileged Identity Management enables organizations to manage and control administrative access to Azure resources. It allows administrators to assign just-in-time (JIT) access to specific administrative roles, providing temporary elevated access when needed. This feature offers fine-grained control over administrative privileges, reducing the attack surface and increasing security.
- Azure AD Identity Governance: Azure AD Identity Governance provides capabilities for managing and governing identities and access within an organization. It includes features like access reviews, entitlement management, and access policies. These features help organizations maintain control over cloud-only administrative accounts and ensure that the right level of access is granted to the right individuals.
- Azure AD Application Proxy: Azure AD Application Proxy enables organizations to securely publish on-premises applications to the cloud and provide remote access to these applications without the need for a VPN. This feature allows administrators to access on-premises tools and resources securely using cloud-only administrative accounts.
- Azure AD Privileged Access Management (PAM): Azure AD Privileged Access Management offers a comprehensive solution for managing and monitoring privileged access across Azure resources. It provides just-in-time access, session recording, and auditing capabilities for cloud-only administrative accounts, reducing the risk of unauthorized access and ensuring accountability.
These exclusive features in Azure AD for cloud-only administrative accounts provide enhanced security, granular control, and improved governance compared to traditional on-premises “classic accounts”. However, it’s important to assess the specific requirements, compliance needs, and security considerations of the organization before deciding on the appropriate approach 🙃
Best Practices for Cloud-only Administrative Accounts
When it comes to managing administrative accounts in Azure AD, some best practices can make all the difference. Regularly reviewing assigned access can help ensure that permissions are only given to those who need them, while applying the principle of least privilege can limit potential damage if those permissions are ever abused. These practices may seem like common sense, but many organizations fail to implement them properly 🙃🫢
More reading about this nice topic?- check this post From on-prem to Global Admin without password reset out and this one: Secure access practices for administrators in Azure AD! 😉
Conditional Access Policies – use it!
You should use Azure AD Conditional Access to interpret signals and make authentication decisions based on them. For more information, see the Conditional Access deployment plan.
- Legacy Authentication Protocols: Use Conditional Access to block legacy authentication protocols whenever possible. Additionally, disable legacy authentication protocols at the application level using application-specific configuration.
- See specific details for Exchange Online and SharePoint Online etc.
- Implement the recommended Identity and device access configurations.
- If you are using a version of Azure AD that does not include Conditional Access, ensure that you are using the Azure AD security defaults.
- For more information on Azure AD feature licensing, see the Azure AD pricing guide.
Implement the recommended Identity and device access configurations.
Monitoring
Once you have configured your environment to protect your Microsoft 365 from an on-premises compromise, proactively monitor the environment.
Basic scenarios you needed to monitor
Monitor as minimum the following key scenarios, in addition to any scenarios specific to your organization. For example, you should proactively monitor access to your business-critical applications and resources to say in front to detect if any unormal activiti is going on.
- Suspicious activity: All Azure AD risk events should be monitored for suspicious activity. Azure AD Identity Protection is natively integrated with Azure Security.
- Define the network named locations to avoid noisy detections on location-based signals.
- User Entity Behavioral Analytics (UEBA) alerts: Use UEBA to get insights on anomaly detection.
- Microsoft Defender for Cloud Apps provides UEBA in the cloud.
- You can integrate on-prem UEBA from Microsoft Defender for Identity. Microsoft Defender for Cloud Apps reads signals from Azure AD Identity Protection.
- Emergency access accounts activity: Any access using emergency access accounts should be monitored and alerts created for investigations. This monitoring must include:
- Read more about this in this post: Break Glass account – and how to get notified when a Break Glass account is used
- Privileged role activity: Configure and review security alerts generated by Azure AD PIM. Monitor direct assignment of privileged roles outside PIM by generating alerts whenever a user is assigned directly.
- Here read more about this in this post: Break Glass account – and how to get notified when a Break Glass account is used
- Azure AD tenant-wide configurations: Any change to tenant-wide configurations should generate alerts in the system. These include but are not limited to
- Application and service principal objects:
- New applications or service principals that might require Conditional Access policies
- Additional credentials added to service principals
- Application consent activity
- Custom roles:
- Updates of the custom role definitions
- New custom roles created
Log Management
Define a log storage and retention strategy, design, and implementation to facilitate a consistent toolset such as SIEM systems like Azure Sentinel, common queries, and investigation and forensics playbooks.
- Azure AD Logs Ingest logs and signal produced following consistent best practices (e.g., diagnostics settings, log retention, SIEM ingestion, etc.). The log strategy must include the following Azure AD logs:
- Sign-in activity
- Audit logs
- Risk events
Azure AD provides Azure Monitor integration for the sign-in activity log and audit logs. Risk events can be ingested through Microsoft Graph API. You can stream Azure AD logs to Azure monitor logs.
- Hybrid Infrastructure OS Security Logs. All hybrid identity infrastructure OS logs should be archived and carefully monitored as a Tier 0 system, given the surface area implications. This includes:
- Azure AD Connect. Azure AD Connect Health must be deployed to monitor identity synchronization.
- Application Proxy Agents
- Password write-back agents
- Password Protection Gateway machines
- NPS that have the Azure MFA RADIUS extension
There is a cool blog I think you should read here: Use UEBA in Microsoft Sentinel to your advantage
Conclusion
Take the time to set up and follow best practices for managing your administrative accounts in Azure AD to stay more secure then today!
Utilizing cloud-only administrative and normal accounts in Azure AD brings several advantages, including enhanced security, flexibility, and streamlined management. By eliminating the reliance on on-premises infrastructure, organizations can leverage the full power and scalability of the cloud while mitigating potential risks associated with on-premises attacks.
When it comes to protecting these cloud-only accounts from on-premises attacks, implementing robust security measures is crucial.
By following these best practices, organizations can significantly strengthen the security posture of their cloud-only accounts in Azure AD and safeguard against on-premises attacks.With a comprehensive approach to security, organizations can fully embrace the benefits of the cloud while maintaining the highest level of protection for their digital assets.
More about topics from this post will/may get more posts at my blog over time.
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳