Last Updated on March 23, 2024 by Michael Morten Sonne
Intoduction
In Public Preview as this post is written
This is part 3 and is about how to Microsoft 365 Access with the Global Secure Access clients – see the next parts for more.
This is the next part – if you not have seen Entra ID – Global Secure Access Client – Part 1 or Entra ID – Global Secure Access Client – Part 2, check them out!
In an era defined by the dynamic nature of work, where teams operate across diverse locations, the need for secure and efficient connectivity has become paramount. Microsoft’s Global Secure Access emerges as a game-changer, revolutionizing the landscape of secure connectivity. In this introduction, we’ll explore what sets Global Secure Access apart from traditional VPNs and how it seamlessly integrates with Microsoft Entra ID to elevate the standards of network security and controll access to resources.

Prerequisites
The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses. To use the Microsoft 365 traffic forwarding profile, a *Microsoft 365 E3 license is recommended. After general availability, Microsoft Entra Private Access and Microsoft Entra Internet Access might require different licenses.
*I’m unclear about the the information behind this suggestion, but we can speculate that it might be a feature exclusive to Microsoft 365 Apps for enterprise or so in the future?
I hope it remains inclusive of the Business Premium license to for many SMBér! 🤞
Administrators who interact with Global Secure Access preview features must have the Global Secure Access Administrator role. Some features might also require other roles.
To follow the Zero Trust principle of least privilege, consider using Privileged Identity Management (PIM) to activate just-in-time privileged role assignments.
Windows client device with the following configuration:
- Windows 10/11 64-bit version.
- Microsoft Entra ID joined or hybrid joined.
- Internet connected and no corpnet access or VPN.
Microsoft Entra admin center
Discover the power of Global Secure Access, your centralized hub within the Microsoft Entra admin center for configuring and managing Microsoft Entra Internet Access and Microsoft Entra Private Access.
Go to https://entra.microsoft.com and exploring the features and capabilities that Global Secure Access has to offer. Elevate your network management experience with Microsoft Entra – your key to a secure and efficient digital workspace.

Types of profiles
Distinct treatment can be applied to the traffic from three app/resource channels:
- Microsoft 365 – encompassing all traffic directed to Microsoft network endpoints (covered in this post).
- Private Access – covering traffic to on-premises hosted apps (yes, like the old app proxys!)
- Internet Access – including traffic to any other network or the internet.
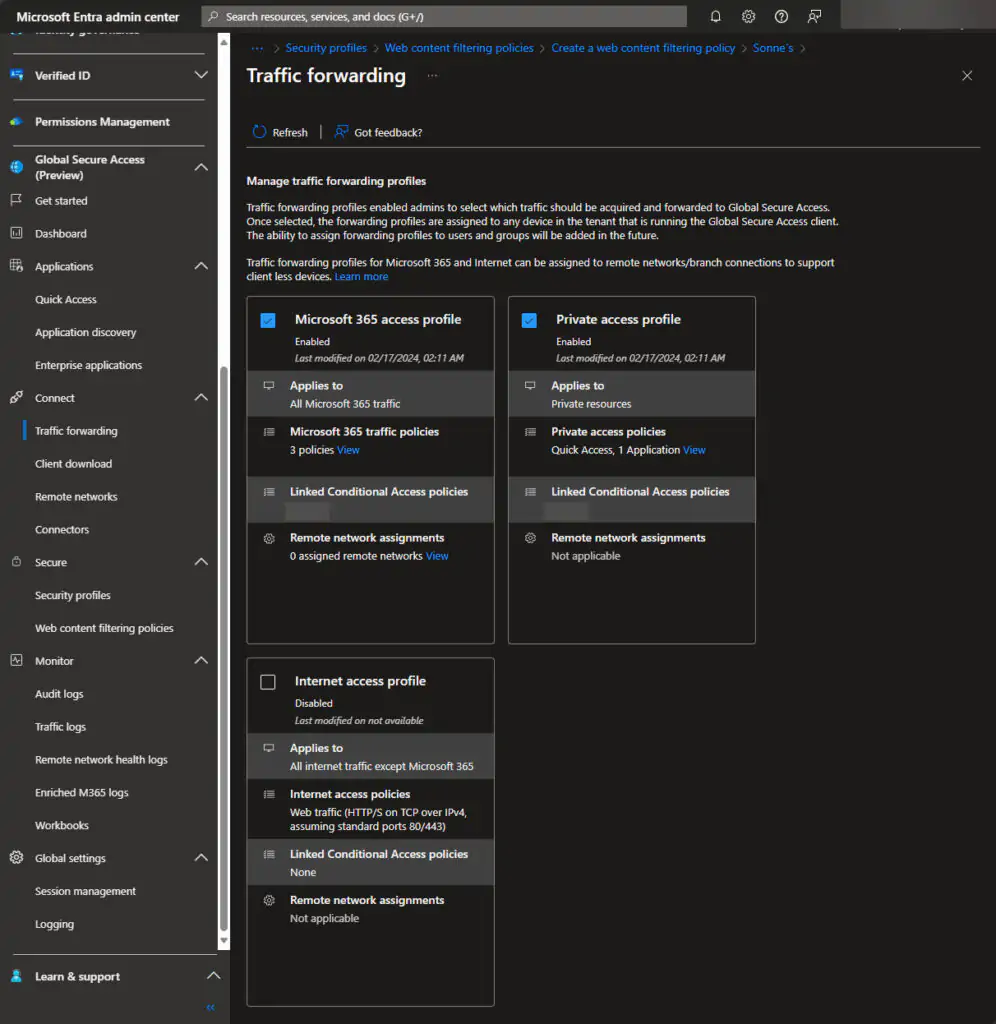
Microsoft 365 forwarding profile
If you enable and setup the Microsoft 365 profile, Microsoft Entra Internet Access takes control of the traffic directed towards your various Microsoft 365 services. The Microsoft 365 profile oversees the following policy groups:
- Exchange Online
- SharePoint Online and OneDrive for Business
- Microsoft 365 Common and Office Online (limited to Microsoft Entra ID and Microsoft Graph)
As you see here, it support the basic for now – but again as you read above, it´s still in preview and more features and supported services will come over time – we hope 😉
Etc. now Teams is currently not supported as part of the Microsoft 365 endpoints. Only Microsoft Entra ID and Microsoft Graph are supported.
Setup the Microsoft 365 traffic profile
To setup the profile, we need to perform some tasks – but not many! 👌
- Sig into your Microsoft Entra admin center and go to Global Secure Access (preview) > Connect > Traffic forwarding.
- Set a mark in the checkbox for Microsoft 365 access profile.

Now you have the capability to assign the profile to users and so – but if you need to adjust it to your needs, we can do that ass well.
Manage your Microsoft 365 traffic policies
To do this, you need to perform the steps here to manage the specific options for URL´s and so in the Microsoft 365 traffic forwarding policy:
- Click on the View link under Microsoft 365 traffic policies.

Here, you will find a list of policy groups, each accompanied by a checkbox indicating its enabled status. Expand a policy group to observe all the IPs and FQDNs contained within the group.

The policy groups include the following details for the rules:
- Policy: The target services or rule group
- Destination type: FQDN or IP subnet
- Destination: The details of the FQDN or IP subnet
- Ports: TCP or UDP ports that are combined with the IP addresses to form the network endpoint
- Protocol: TCP (Transmission Control Protocol) or UDP (User Datagram Protocol)
- Action: Forward or Bypass
You have the option to exclude specific traffic, allowing users to access the site without the service processing the traffic. This bypass can be applied to a particular FQDN or IP address, an entire policy group within the profile, or the entire Microsoft 365 profile. If you only want to forward specific Microsoft 365 resources within a policy group, enable the group and adjust the Action in the details accordingly.
For instance, the following example demonstrates setting the *.sharepoint.com FQDN to Bypass, preventing the traffic from being forwarded to the service (it´s the most easy service to test with).

Should the Global Secure Access client encounter issues with connecting to the service, such as an authorization or Conditional Access failure, the service will automatically bypass the traffic. Instead of being blocked, the traffic is directed locally.
In this situation, you have the option to establish a Conditional Access policy specifically for the compliant network check, preventing the traffic if the client fails to establish a connection with the service. Only here if that is the case, the user can still access SharePoint – but the reason why and not to do this, is up to your self.
Forwarding profile updates
There is a auto refresh for profile updates in an interval of 5 min. from the client side – and ofc. some service side processing involved too 😉
That is more offen that I first think about, so that is a nice small fun fact! 🤘
Recall from the initial post (Entra ID – Global Secure Access Client – What it is about – Part 1 – Blog) that within the Global Secure Access Client, there is a menu in the Advanced Diagnostic section where you can view the applied profiles and the last update timestamp. In this section, you also have the option to refresh details to obtain the latest updates for your profiles as you need to have them updated! 😉
If you need to force an update:
- Find the Global Secure Access Client tary icon behind the clock in the processbar

- Then click on Advanced diagnostics when you right click on the icon

- Go to the Forwaring profile tab – here you will see the last update, profile information and the Refresh details option to force an update.

- When updated, your changes should reflect on your clients when assigned when you fold out the rules 😉
Conditional Access policies
There will come more in a blog post in the serie for the options regarding Conditional Access policies later – but here is a bit when we take the Microsoft 365 profile in use for accessing your applications.
Conditional Access policies are generated and implemented within the Conditional Access section of Microsoft Entra ID’s traffic forwarding profile. As an illustration, you can establish a policy mandating the use of compliant devices for accessing Microsoft 365 services and a need for use of MFA and so on.
After activating these settings, your subsequent action involves setting up your Conditional Access policies to utilize the traffic policies. Alternatively, you can configure them to enforce connection to the secure network (the SSE) before gaining access to Microsoft 365 services, by the automatic creation of a new Named Location for the service backend.

If the Linked Conditional Access policies section displays None, it indicates the assignment of a Conditional Access policy associated with the traffic forwarding profile is not set.
If there is an associated Conditional Access policy linked to the traffic forwarding profile, you have the capability to both view and modify that policy.
To see the name of the linked Conditional Access policies, click on the View link for associated Conditional Access policies.
Bonus – Conditional Access network traffic profiles
Besides utilizing the All Compliant Network location, we can specifically focus on the Global Secure Access traffic profiles affected by the policy. This allows us to enforce additional criteria, such as Multi-Factor Authentication (MFA), MFA strength requirements, the need for a compliant or hybrid joined device, or even the acceptance of Terms of Use before granting access.
To make the below configuration effective, it is essential to set up the Grant controls first. Interestingly, once the Global Secure Access target resource is selected, the Terms of Use options become grayed out. While I’m uncertain if this is intentional, it functions as intended and is suitable for testing purposes.

However, let’s delve into those details in one of the upcoming sections when we explore the Conditional Access options 😎🤘
Lets test it
In this small test, we setup this to block a user from SharePoint (OneDrive also) to access this if not running (connected) to the secure network of Global Secure Access.
From the administrator side
- Go to the Entra ID portal > Protection > Conditional Access > Policies and create a new.
(Here is the direct link: Conditional Access – Microsoft Entra admin center) - Target your users or groups for this policy, and assign your applications in this sample you will block access to if not connected over the Global Secure Access network

- Now setup the conditions for locations, and set Include to All and Exclude to exclude the All Complient Network location – now this is set and you can set the other paramenters too

- Now in the next step, set the Access controls > Grant to Block access
You can set other options to, but we use this only for our small test 😊
From the user side
If we here with my test user Adele Vance, and we try to connect to SharePoint Online from any location other than through the Secure Service Edge, access should be denied.
She can still access etc. the Office Home and Exchange Online. This configuration guarantees that access to these resources is strictly restricted, requiring authentication through the GSA client and connection to the SSE network before access is granted. Let’s observe this setup on the client side 😎
Let’s sign into the Office Home site at portal.office.com – as you see here, we can sign in with no issues! 🤘

Now lets try to access Exchange Online – and as you see here we can access that fine also – aligning with our expectations at this point from what se setup before 😉

Now, let’s observe the outcome when attempting to navigate to SharePoint Online.

Success – Access to SharePoint is restricted, aligning with our expectations at this point! 🎉
Now lets try etc. the Word Online application – as you see here we can successfully access the Word online application itselft at https://www.office.com/launch/Word/. However, what happens when we normaly try to access or create a new file that is automatically saved in your OneDrive? Since OneDrive is integrated with SharePoint Online, we anticipate that there will be no access in this scenario.

When we try to open the document, you will get this message that the access it blocked:

In this scenario, you see that the user is unable to access or carry out actions on content that relies on the SharePoint Online service.
Conclusion
In summary, the Microsoft 365 traffic forwarding profile in Microsoft Entra Internet Access streamlines the management of traffic to Microsoft 365 services. This feature allows users to control policy groups, selectively bypass traffic, and customize actions. The blog post outlines the setup process, prerequisites, and known limitations, offering a user-friendly guide.
I looking forward to more supported applications and devices – Windows and so is currently the only supported OSés beside Android. For the moment of this post is written, support for iOS and MacOS is not out (yes, for them with some special private access 😂) so we need to wait a bit more here.
Some points overall for about this form me is:
- Modern security infrastructure is essential for safeguarding cloud-based applications and data.
- Traditional VPNs, connecting users to network segments instead of specific applications, pose security risks and potential issues.
- Client authentication is facilitated through Entra ID and Conditional Access, enhancing security measures.
- Entra ID joined or Hybrid joined devices are prerequisites for using the GSA client – here we have a nice way to control the devices too!
- Entra Internet Access isolates Microsoft 365 applications and resources, bolstering security for users.
Key points include enabling the profile, configuring Microsoft 365 traffic policies, and understanding the relationship with Conditional Access policies. Visual aids enhance comprehension, and the post emphasizes the flexibility to selectively bypass traffic and manage policies.
The integrated approach allows users to link and edit Conditional Access policies directly from the traffic forwarding profile, ensuring a cohesive and secure experience for Microsoft 365 users. In essence, the blog post serves as a comprehensive guide for optimizing and securing access to Microsoft 365 services through the traffic forwarding profile.
Stay tuned for Part 4, where we’ll explore Private Access, focusing on traffic directed towards on-premises hosted apps!
It’s important to note that while the Global Secure Access feature is currently in preview, and its licensing requirements may evolve as it progresses towards General Availability (GA)!
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳