Last Updated on March 14, 2024 by Michael Morten Sonne
Table of Contents
- Tip 1 – Block the legacy authentication protocols!
- Tip 2 – Do not expire passwords
- Tip 3 – Turn on user risk/sign-in risk policy
- Tip 4 – Enable password hash sync
- Tip 5 – Pink thumb extension (a nice free browser extension!)
- Tip 6 – Defender for Cloud Apps
- Tip 7 – Azure MFA additional context & Sign-in frequency
- Tip 8 – Conditional Access authentication strength (preview)
- Tip 9 – Defender for Office 365
- Tip 10 – Privileged Identity Management (PIM)
- Tip 11 – Go Passwordless!
- Tip 12 – Limit administrative access
In the post here, I will share 10 tips on how to strengthen your security posture in Microsoft 365, where we specifically look at identity protection. This is a littel “repost” from my old blog, but a bit updated on some parts👍
Tip 1 – Block the legacy authentication protocols!
The most important step is to take the move towards modern authentication. This will allow you to add more layers and really help you to implement the Zero Trust principles.
Now, with the front door locked , we should also take care of the backdoor: legacy authentication. With legacy authentication, we are talking about old protocols that can be used to authenticate against Microsoft 365 apps and data, such as IMAP, POP3, and SMTP. These protocols are not capable of enforcing modern authentication such as Multi-factor Authentication. Therefore, they should be blocked.
Effective October 1, 2022, we will begin to permanently disable Basic Authentication for Exchange Online in all Microsoft 365 tenants regardless of usage, except for SMTP Authentication.
MICROSOFT
Now, if you don’t want to wait until Microsoft disables legacy authentication for you (is was mayby disabled for you, if you not had enabled it again by yourself), you can simply use the new Conditional access templates to Block legacy authentication in your tenant.
Using these templates, you can quickly block legacy authentication requests for all users, and therefore reduce the risk of password attacks.
There is a lot of templates in the portal now (preview),
How to
- In the Azure portal, go to Azure Active Directory -> Security -> Conditional Access -> + New policy -> Create new policy from templates (preview)
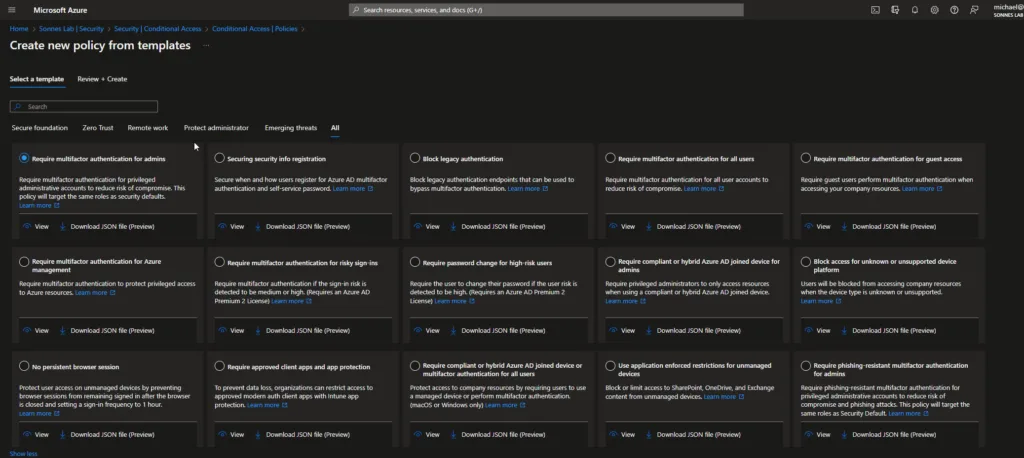
- Next, select the Block legacy authentication template, and configure the policy to your needs. It’s recommended to always start the policy in “report-only” mode to start with, to measure the potential impact – we will not break any importent stuff 😉
- Click Next to save it.
If you want to find out if legacy authentication is still used within your environment, the “Sign-ins using legacy authentication” workbook is a good starting point (if you have Log Analytics integration enabled).
There is a list for more information about templates here: Conditional Access templates – Microsoft Entra | Microsoft Learn
Tip 2 – Do not expire passwords
This tip will be around password policies. I had see a lot of organizations that force their users to reset their passwords every 30 or 90 days etc. Now, initially, this seems like a good thing to do, but based on research, each time the password is being reset, they become a little weaker.
Human beings are not very good at making up and remembering complex passwords, and therefore we use “tricks” like adding numbers or characters at the end of the password. So, a user who used MySecurePassword for 90 days, and is forced to pick a new one, is more likely to pick MySecurePassword1, other than making up a completely new password – that is NOT good for anyone!
So, there is a lot of discussion about password policies, and the question of what “a good password” is. Now, take this scenario as an example: You are working for a company that is using Microsoft 365. The company provided a managed Windows device that is joined to Azure AD, and Single Sign-On is enabled. So, at the start of your workday, you are prompted to enter your password in order to sign in to Windows. Once you signed in, SSO is taking care of the rest so you can use Microsoft 365 without using your credentials. The problem however, is the fact that you still need to type in your password every day (at least once), and therefore you should remember that password. I have never seen a frontline worker, reach out to their password manager (if they even have one hehe 🤣) and type over their password for day-to-day use.
Instead, they use a password that they can remember easily. So, that’s why you should focus on the places where users need to type a password and offer passwordless options if possible, like Windows Hello for Business, Authenticator App, or FIDO2 keys. Forcing them to frequently change that password, won’t make any sense, since they still pick easy-to-remember passwords.
My personal tip to create “good” passwords is to create a passphrase with 3 to 5 random words. These types of passwords are fairly easy to remember, hard(er) to guess, and still more secure than any other password that contains personal information, dates, or names of relatives (seen a lot of this!).
Keep in mind that, if you fall for phishing or if your password is being stolen during a breach, your password does not matter, since it’s already known by the attacker. Multi-factor authentication would protect you from worse – etc.:

Next to that, you can prevent users from picking easy-to-guess passwords, by implementing Azure AD Password Protection. You can even extend this to your on-premises Active Directory!
This is nice, and go to the setting right here in the portal and read more about this feature here: Azure AD Password Protection – Microsoft Entra | Microsoft Learn!
Tip 3 – Turn on user risk/sign-in risk policy
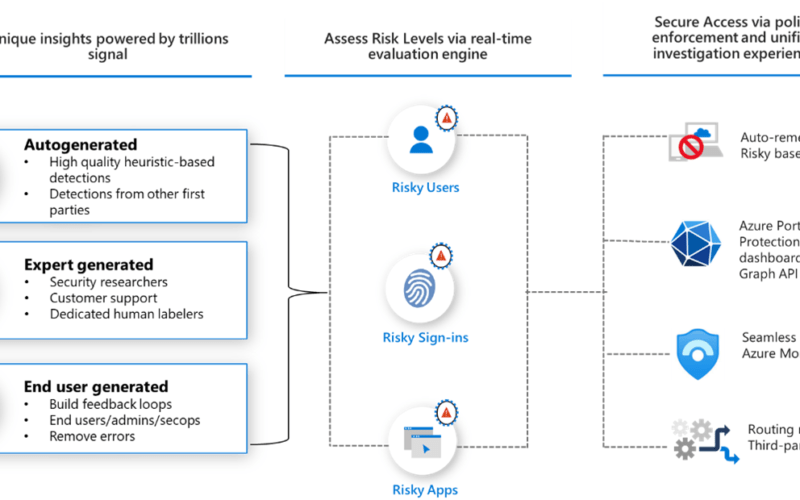
The next tip would be around Azure AD Identity Protection. This is an Azure AD Premium P2 feature, but it brings great insight into your identity events, logins etc. Using the Microsoft intelligence engine, all sign-ins will be measured against a baseline, and if something unusual happens, an automated response takes place – nice right? 😉
So when a user signs in from an unknown location or device etc., this will trigger a risk event, that can trigger an MFA prompt, block, or even password reset, depending on your policies. This is sometimes referred to as “risk-based MFA”, and only prompts users when necessary. This will prevent users from accepting numerous MFA prompts, without knowing where it comes from (MFA fatigue).
You can integrate this feature with Conditional Access so that you have granular control of your policies. In short, you can use these policies in three ways:
- Using the Azure AD Identity Protection policies (not able to define conditions and exclusions)
- Using the Conditional Access sign-in and user-risk conditions (more flexibility)
- By enabling Security Defaults (no P2 license required, but also no flexibility)
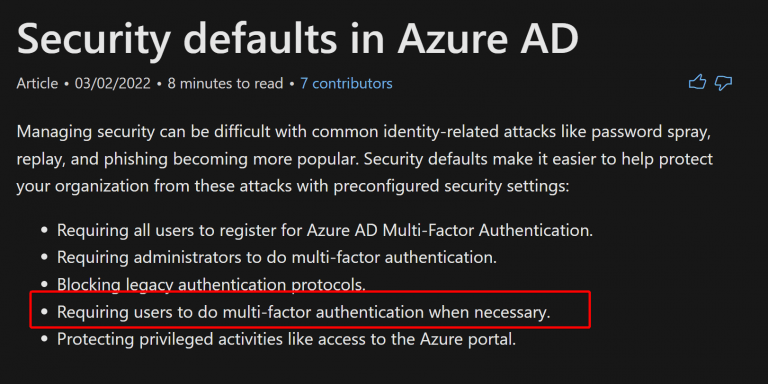
With Security Defaults, you basically get “free P2 features” – but you can´t modify many nice features!
Tip 4 – Enable password hash sync
Password hash synchronization is one of the sign-in methods used to accomplish a hybrid identity. Azure AD Connect synchronizes a hash, of the hash, of the user’s password from an on-premises Active Directory instance to a cloud-based Azure AD instance. Password hash synchronization helps by reducing the number of passwords your users need to maintain to just one. Enabling password hash synchronization also allows for leaked credential reporting.
You can read more about how this works here: Implement password hash synchronization with Azure AD Connect sync – Microsoft Entra | Microsoft Learn
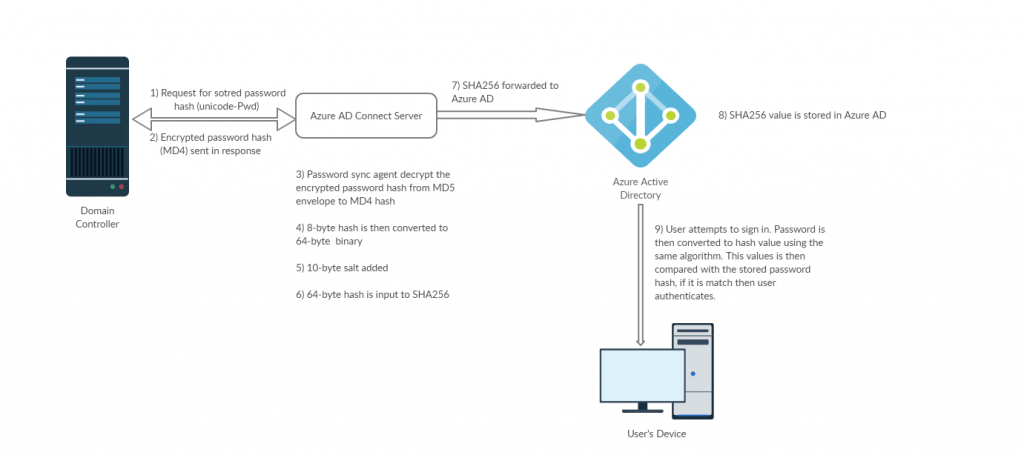
In the previous tip, we talked about Identity Protection which can discover various risks in your environment. One of those risk detections is “leaked credentials”.
If you use cloud identities, no further action is needed, but if you use hybrid identities (most of us do that right?), you need to sync your password hashed in order to benefit from this feature.
This risk detection type indicates that the user’s valid credentials have been leaked. When cybercriminals compromise valid passwords of legitimate users, they often share those credentials. This sharing is typically done by posting publicly on the dark web, paste sites, or by trading and selling the credentials on the black market.
When the Microsoft leaked credentials service acquires user credentials from the dark web, paste sites, or other sources, they are checked against Azure AD users’ current valid credentials to find valid matches – if mathed, take action!
You can read more about how it works in depth here: How password hash synchronization works
Tip 5 – Pink thumb extension (a nice free browser extension!)
Now, as we stated before, most breaches start with phishing. A nifty way to prevent this is by using this Edge/Chrome extension and teaching your users to pay attention when entering credentials.
How does this work? When a phishing link is clicked and asks for credentials, the thumb icon will be greyed out. When the page is legit, the pink thumb will show up. So, the users will only provide credentials when the icon is pink.
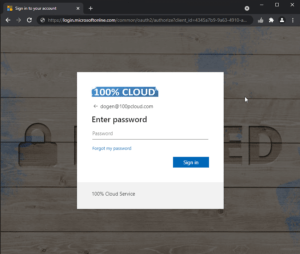
Link is invalid
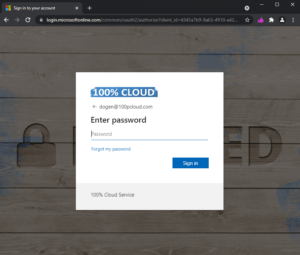
Link is valid
This will of course not prevent you from all phishing attacks, but it’s a very user-friendly (and free!) feature to add to your companies’ cyber security toolkit and training sessions.
“o”, “0”, “1”, “l” or “i” can easy look like the same in a address bar in your browser, so it was nice to get a heads-up of someone try to do phishing attacks on you!
More info can be found here: Pink Thumb | (emptydc.com)
Please read the Twitter thread to learn the downside of Visual Security Indicators, or read this article from the master himself. Troy Hunt: The Decreasing Usefulness of Positive Visual Security Indicators (and the Importance of Negative Ones)
Tip 6 – Defender for Cloud Apps
In order to take the full advantage of Azure AD Identity Protection, you should enable the integration with Defender for Cloud Apps (previously known as Microsoft Cloud App Security). A lot of risk signals can only be detected by Defender for Cloud Apps:
- Suspicious inbox manipulation rules
- Impossible travel
- New country
- Activity from anonymous IP address
- Suspicious inbox forwarding
- Mass Access to Sensitive Files
Defender for Cloud Apps has an integrated automated response module, where you can etc. trigger Power Automate flows to take automated actions, send emails, or even text messages.
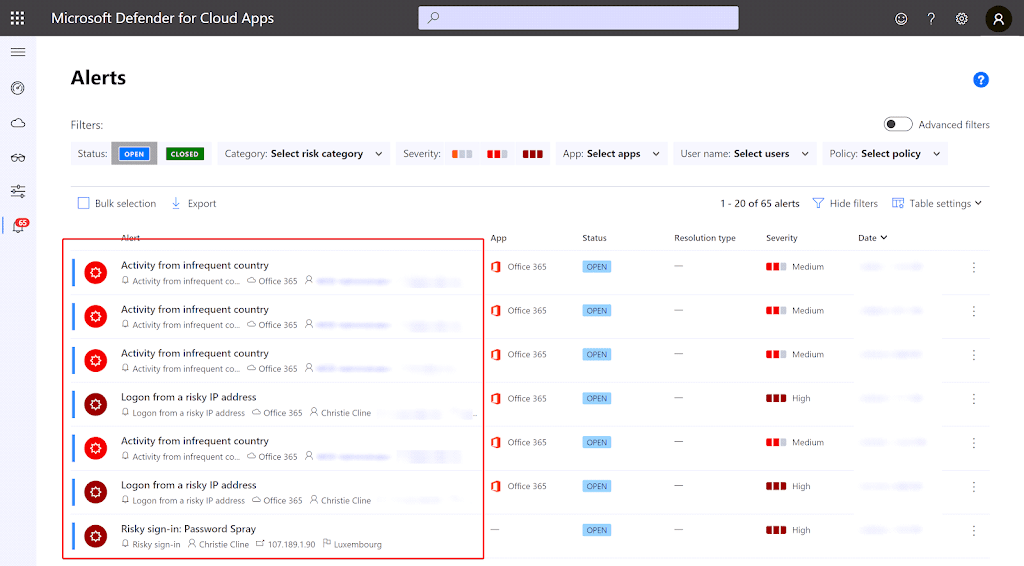
To enable Azure AD Identity Protection alert integration, go to your Defender for Cloud Apps portal (https://aka.ms/mcasportal) and go to Settings.

Under the Threat Protection section, you will find the Azure AD Identity Protection setting:
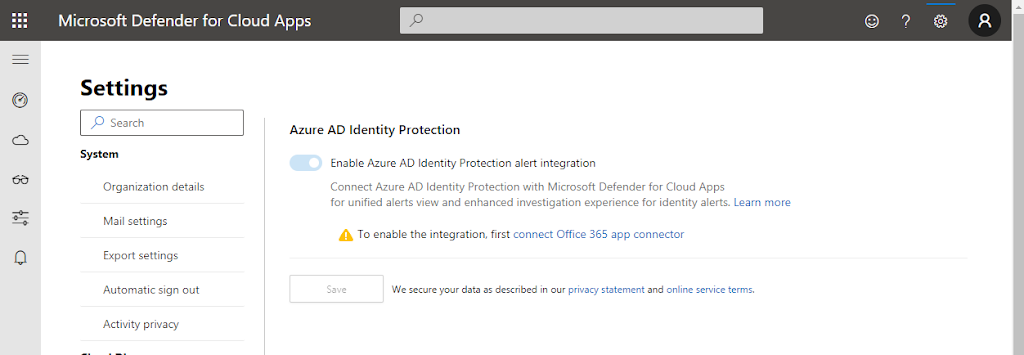
Learn more here: Integrate Azure Active Directory Identity Protection with Defender for Cloud Apps | Microsoft Docs
Tip 7 – Azure MFA additional context & Sign-in frequency
I’m a big fan of the Microsoft Authenticator app for its simplicity and user-friendly design. Users can simply approve sign-in requests that are protected with Azure MFA. However, there lurks danger behind this feature. Many companies are “over-prompting” their users so it is not always clear where these prompts come from.
In general, you should only be prompted once per user, per device, and per password reset, but this really depends on the configuration of your Azure MFA settings. This goes hand in hand with the settings around the persistent browser, sign-in frequency, and Keep Me Signed In feature.
Now, there is a very nice article on the Microsoft docs that gives best practices around this topic. In short, this is the take-away:
If you have an Azure AD Premium license:
- Enable single sign-on (SSO) across applications using managed devices or Seamless SSO.
- If reauthentication is required, use a Conditional Access sign-in frequency policy.
- For users that sign in from non-managed devices or mobile device scenarios, persistent browser sessions may not be preferable, or you might use Conditional Access to enable persistent browser sessions with sign-in frequency policies. Limit the duration to an appropriate time based on the sign-in risk, where a user with less risk has a longer session duration.
If you have Microsoft 365 apps licenses or the free Azure AD tier:
- Enable single sign-on (SSO) across applications using managed devices or Seamless SSO.
- Keep the Remain signed-in option enabled and guide your users to accept it.
“Our research shows that these settings are right for most tenants. Some combinations of these settings, such as Remember MFA and Remain signed-in, can result in prompts for your users to authenticate too often. Regular reauthentication prompts are bad for user productivity and can make them more vulnerable to attacks.”
MICROSOFT
Now that we know how to configure the optimal policies (for most organizations), there are two very interesting features that can help to tighten the security around the Microsoft Authenticator App.
Additional Context
This feature will add additional context to the MFA prompt in the Authenticator App, such as the name of the application, and the sign-in location based on IP address. If those details seem unfamiliar to the users, they are more likely to deny the request.

Number matching
Instead of prompting your users to approve or deny, it is also possible to require number matching. The sign-in screen will show a number, that needs to be typed within the Authenticator app on the phone. If those numbers match, the sign-in is approved. In case of an attack, the user would not be able to approve the MFA request, since it does not know the number to type.
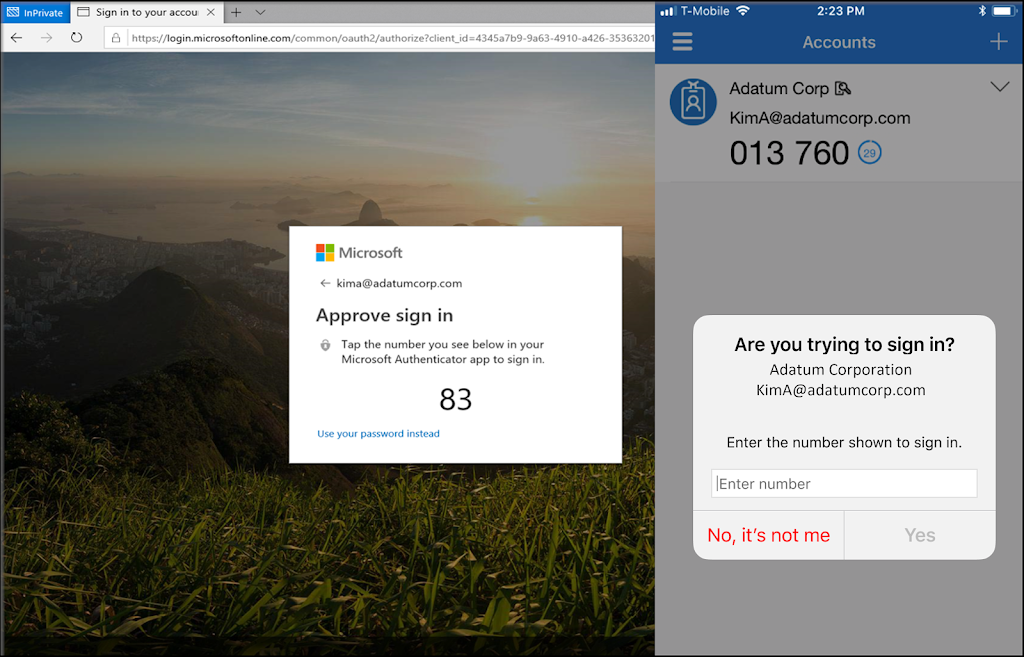
Both features can be enabled rather simply, and is easy to use for the end user.
Tip 8 – Conditional Access authentication strength (preview)
Authentication strength is a Conditional Access control that allows administrators to specify which combination of authentication methods can be used to access a resource. For example, they can make only phishing-resistant authentication methods available to access a sensitive resource. But to access a nonsensitive resource, they can allow less secure multifactor authentication (MFA) combinations, such as password + SMS.
Authentication strength is based on the Authentication methods policy, where administrators can scope authentication methods for specific users and groups to be used across Azure Active Directory (Azure AD) federated applications. Authentication strength allows further control over the usage of these methods based upon specific scenarios such as sensitive resource access, user risk, location, and more.
An authentication strength can include a combination of authentication methods. Users can satisfy the strength requirements by authenticating with any of the allowed combinations. For example, the built-in Phishing-resistant MFA strength allows the following combinations:
- Windows Hello for Business
- FIDO2 security key
- Azure AD Certificate-Based Authentication (Multi-Factor)
You can see default Authentication strengths policyes here where you can setup your own to.
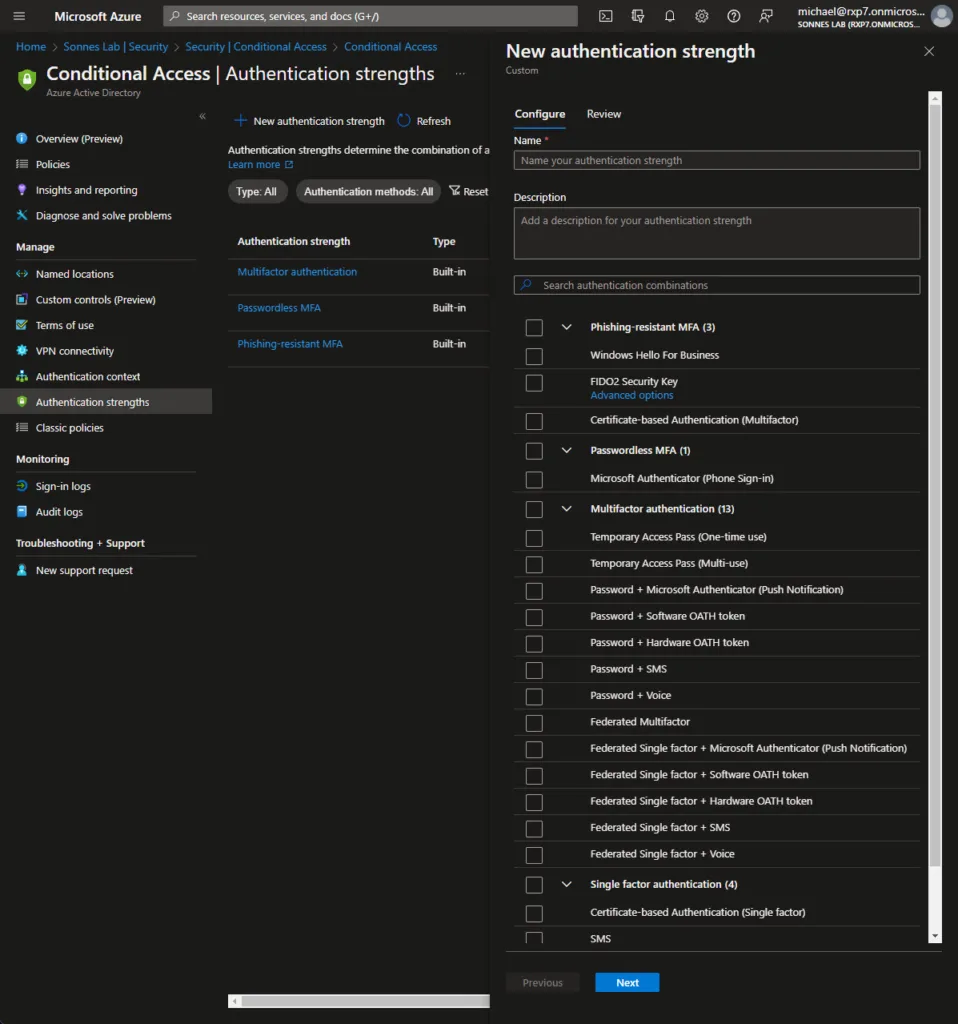
Prerequisites
- Azure AD Premium P1 – Your tenant needs to have Azure AD Premium P1 license to use Conditional Access. If needed, you can enable a free trial.
- Enable combined registration – Authentication strengths are supported when using combined MFA and SSPR registration. Using the legacy registration will result in poor user experience as the user may register methods that aren’t required by the authentication method policy.
Read more about this feature here: Overview of Azure Active Directory authentication strength (preview) – Microsoft Entra | Microsoft Learn
Tip 9 – Defender for Office 365
As stated in the intro, most attacks start with phishing. There is a lot that you can do on the prevention side here, and it is all built-in in Defender for Office 365.
I want to point out three features that are key in protecting your users from unwanted content.
- Attack Simulator
- Safe Links/Safe attachments
- Anti phishing policies
The best way to see an overview of the products and their license requirements is to get an overview from Home | M365 Maps
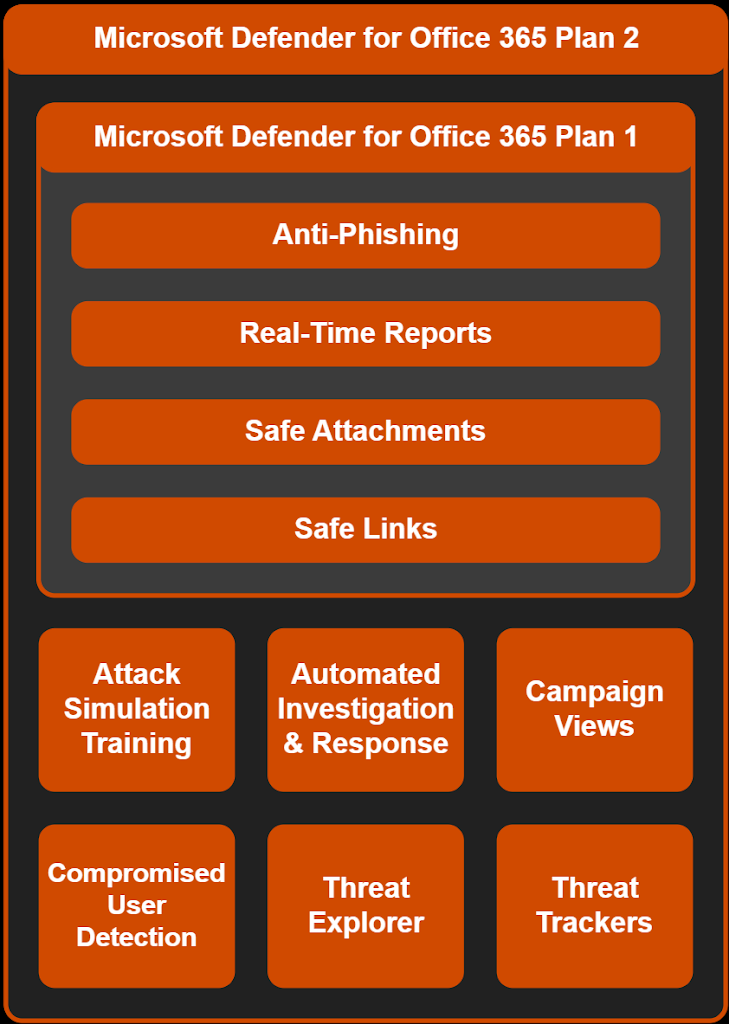
Attack simulator
This tool can be used to train your users in identifying phishing and get them educated on that subject. Administrators can send out phishing emails that look very tempting to check if users will take the bait, or report them. Based on the outcome, you can provide a follow-up, like an e-learning module.
Safe Links
Safe Links is a feature that is able to do time-of-click verification of URLs and links in email messages and other locations. Safe Links protection for Office 365 apps is available in supported desktop, mobile, and web apps. So, when a user did not pay attention and clicks a malformed link, Safe Links is able to block that action.
Anti-phishing policies
This feature is very good in detecting phishing attacks and can be used to give guidance to your users by providing safety tips, like this example:
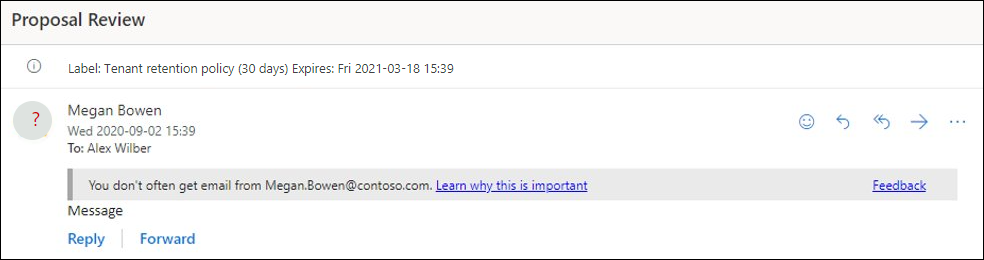
It can also be used to detect impersonation. Impersonation is where the sender or the sender’s email domain in a message looks similar to a real sender or domain. It is very common to impersonate managers, board members, or chiefs within an organization, so those policies can be scoped to specific users as well.
Etc. “0” and “o” can look like the same, and not easy to spot in the allways!
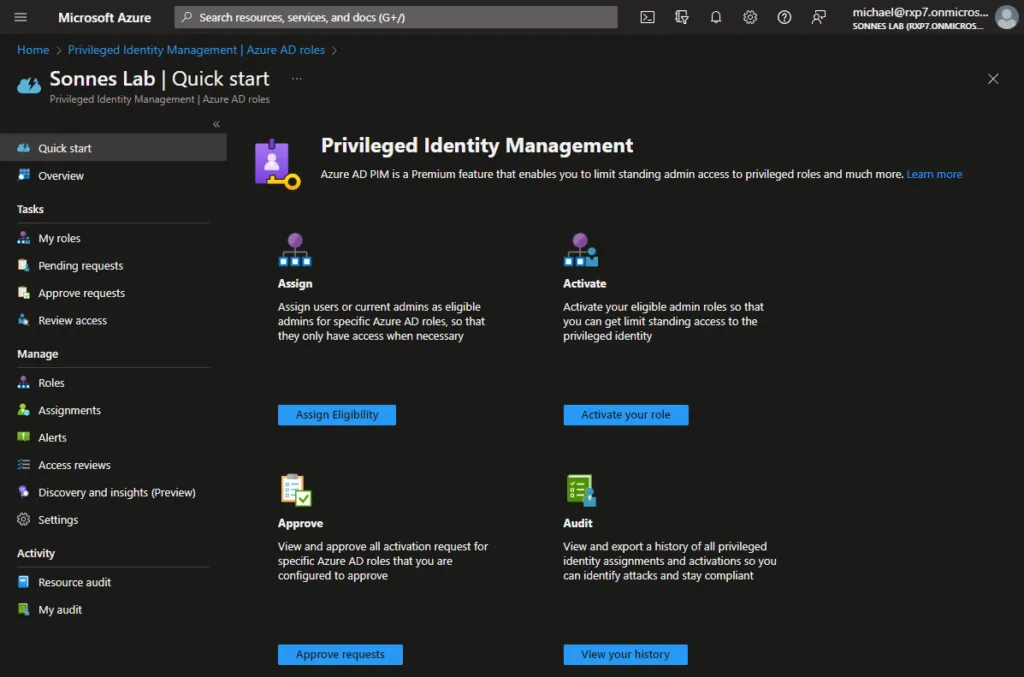
Tip 10 – Privileged Identity Management (PIM)
Zero Trust is based on the principles of ‘least privilege‘ and ‘always verify’. Azure AD resources and roles are often accessible with standing access by IT staff, or sometimes even office workers. In most situations, this access is never been reviewed, even when users switch jobs, or leave the company. Those who read my blog posts more often, do know that I’m a big fan of the Identity Governance features in Azure AD. It is a really powerful feature to keep in control of your role and resource access.
Again, check out information from Home | M365 Maps – it´s a very nice website!
N.B: it´s not an officel Microsoft website!
Using Azure AD Privileged Identity Management, administrators are able to access roles and resources, just in time, and with just enough privileges. Access can be protected with MFA or approval from a manager and can be reviewed on a recurring base. Together with Conditional Access, high privileged roles can be protected in such a way that they are only usable from managed devices (Privileged Access Workstations) or locations.
Prerequisites
- Azure AD Premium P2 – Your tenant needs to have Azure AD Premium P2 license to use Privileged Identity Management. If needed, you can enable a free trial in your Azure AD portal.
Read more about this feature here: What is Privileged Identity Management? – Microsoft Entra | Microsoft Learn
Tip 11 – Go Passwordless!
Last but not least: the best tip against phishing is related to the source of all evil: passwords. We need to get rid of them. Simply put: you cannot steal a password if there ain’t any, smart! 😉
Microsoft is really determined to play a big role in that mission and offers the following three passwordless authentication options that integrate with Azure Active Directory (Azure AD):
- Windows Hello for Business
- Microsoft Authenticator app
- FIDO2 security keys
Windows Hello for Business
Windows Hello for Business is ideal for information workers that have their own designated Windows PC. The biometric and PIN credentials are directly tied to the user’s PC, which prevents access from anyone other than the owner. With public key infrastructure (PKI) integration and built-in support for single sign-on (SSO), Windows Hello for Business provides a convenient method for seamlessly accessing corporate resources on-premises and in the cloud.
Read more about this feature here: Windows Hello for Business Overview (Windows) | Microsoft Learn
Microsoft Authenticator app
You can also allow your employee’s phone to become a passwordless authentication method. You may already be using the Microsoft Authenticator App as a convenient multi-factor authentication option in addition to a password. You can also use the Authenticator App as a passwordless option.
The Authenticator App turns any iOS or Android phone into a strong, passwordless credential. Users can sign in to any platform or browser by getting a notification to their phone, matching a number displayed on the screen to the one on their phone, and then using their biometric (touch or face) or PIN to confirm.
FIDO2 security keys
FIDO2 security keys are an unphishable standards-based passwordless authentication method that can come in any form factor like USB keys, or even wearables. Users can register and then select a FIDO2 security key at the sign-in interface as their main means of authentication. These FIDO2 security keys are typically USB devices, but could also use Bluetooth or NFC technology.
FIDO2 security keys can be used to sign in to their Azure AD or hybrid Azure AD joined Windows 10/11 devices and get single-sign on to their cloud and on-premises resources. Users can also sign in to supported browsers. FIDO2 security keys are a great option for enterprises who are very security-sensitive or have scenarios or employees who aren’t willing or able to use their phones as a second factor. FIDO2 keys are perfect for shared-PC scenarios like call centers, schools, or universities.
Passwordless starts with the user onboarding. New hires or students can register their passwordless credentials using a temporary access pass, without even knowing their real password.
Read more here about this feature: Azure Active Directory passwordless sign-in | Microsoft Docs
Tip 12 – Limit administrative access
Limiting administrative access to your Microsoft 365 environment is a critical step in securing your identities and data. By restricting administrative access to only the users who need it, you can minimize the risk of a security breach or unauthorized access to sensitive information.
To achieve this, you can use the principle of least privilege. This means that you should grant administrative access only to those users who need it to perform their job responsibilities. For example, if an employee only needs to manage user accounts, there’s no need to give them access to the entire Microsoft 365 environment.
To view an overview of build-in roles in Azure AD, check all the roles here: Azure AD built-in roles – Microsoft Entra | Microsoft Learn
To implement this principle effectively, you should also ensure that administrative access is time-limited. Once the task is complete, the access should be revoked. You can also use audit logs to track administrative activities, making it easier to identify suspicious behavior.
Here, you can use tip 10 – Privileged Identity Management (PIM) to secure it more, so the roles is not permanent assigned AND active for an user/administrator!
Another important aspect of limiting administrative access is to ensure that administrative accounts are secured with strong passwords and strong multi-factor authentication. These accounts should not be shared, and the passwords should be changed regularly! See also tip 8 – Conditional Access authentication strength (preview) to use a secure MFA method!
By limiting administrative access in your Microsoft 365 environment, you can reduce the risk of a security breach and help keep your identities and data safe. Be sure to review your administrative access policies regularly to ensure they continue to meet your organization’s needs.