Last Updated on February 19, 2024 by Michael Morten Sonne
Intoduction
Background
Companies that do not implement Multi-Factor Authentication (MFA) in their Microsoft 365 (M365) tenants are potentially exposing themselves to increased cybersecurity risks. MFA is a crucial security measure that adds an extra layer of protection by requiring users to verify their identity through multiple methods, such as a password and a one-time code sent to their mobile device or use of a phishing resistent device like a FIDO2 key – aka hardware token!
Here you need to control what types of MFA method you allow in your tenant – you can read more about this here: Authentication methods and features | Microsoft Learn – I can cover this in another post 😁
Without MFA, Microsoft 365 accounts (Entra ID accounts) are more susceptible to unauthorized access, data breaches, and other security threats. Hackers can exploit weak or stolen passwords/tokes to gain unauthorized entry, potentially compromising sensitive information and causing significant damage to a company’s reputation! 🫢
Implementing MFA is a simple and effective way to enhance the security of Microsoft 365/Entra ID tenants, and it should be considered a fundamental practice for any organization. It helps ensure that only authorized individuals can access company resources, reducing the risk of data breaches and cyberattacks.
You can read more about the corrent cyber threats here in Microsofts Digital Defense Report 2023 (MDDR) – etc. the use of MFA is here, and can take a lot of the most!
Important stuff to read
Added 06-11-2023:
Studies shows that multifactor authentication reduces the risk of account takeover by over 99 percent! 😮
In 2017, MFA usage was 0.7% of MAU (Monthly Active Users) and in 2023, Microsoft has driven it up to 37%
To get to 37% Microsoft has:
- Run promotional campaigns
- Made MFA available for free on all license tiers, including trial licenses
- Introduced Security Defaults where MFA was turned on by default on all new tenants
- and later, Security Defaults was deployed to all existing tenants
But 37% is not enough, and Microsoft’s goal is 100% multifactor authentication!
Can´t agree more!
The next step will be the automatic roll-out of Microsoft-managed Conditional Access policies 👌🥳
Microsoft will start with three conditional access policies as you can read more about in this post.
The policies will begin rolling out in read-only mode to ‘eligible’ tenants starting next week (as of 06-11-2023)
- Tenants that will get these policies will be informed in advance
- After 90 days (3 months), these policies in report-only mode will be automatically enabled
Within the 90-days window admins can:
- Customise the policy by excluding users, groups, or roles
- Disable policy if required
Finally on the roadmap!
Here is a small quick post, to hightligt something new I had missed to long: And yes – finaly its here – as from my time in IT and work with Microsoft 365 tenants, I have seen to many not protect there identityes in Entra ID (before Azure AD) to “a bare minimum” too many times – and it´s so bad! 😭😟
There is so many tenants there not have MFA “mandatory”, have admin roles assigned to identityes not covered by MFA – Entra ID roles AND Azure admin roles for Subcriptions!!!
Now, finally – Microsoft is underway to introducing new Conditional Access policies there are automatically generated to establish fundamental security measures on your Entra ID tenant! 🥳
🌐 Public roadmap entry for this is here: Microsoft 365 Roadmap ID 183905 | Microsoft 365

Yes – that´s right! 🙌
Whats is this about – and that will it setup in my tenant?
Starting in November/ 2023 (or when it hits Public Preview), Microsoft will begin to automatically protecting customers with Microsoft managed Conditional Access policies.
These are some policies that Microsoft creates and enables in customer tenants worldwide as it stands out for now where.
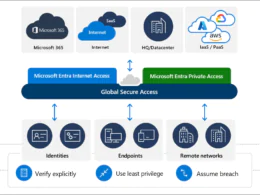
This will protect your resources based on risk signals, usage patterns, and your licensing options. These policies will help you to enhance your security posture and reduce the complexity of managing conditional access is not realy used that today.
This applies to tenants with EntraID P1/P2 licenses as that is needed to use Conditional Access policies in a tenant.
The following policies will be rolled out to all eligible tenants:
- MFA for admin portals: This policy covers privileged admin roles and require MFA when an admin sign-in into a Microsoft admin portal – Who it’s for: All customers
- Here there was a new “App” called “Admin Portals” under Conditional Policies now GA!
This rule applies to admin roles and force the use of multi-factor authentication (MFA) when accessing the Microsoft admin portals. The admin portal app contains many Microsoft 365 administration portal/tools and it will continue to grow in functionality/covering apps over time – for now as this post is written its covering:- Azure portal
- Exchange admin center
- Microsoft 365 admin center
- Microsoft 365 Defender portal
- Microsoft Entra admin center
- Microsoft Intune admin center
- Microsoft Purview compliance portal
Read more here about the new Admin Portals App: Cloud apps, actions, and authentication context in Conditional Access policy | Microsoft Learn
- Here there was a new “App” called “Admin Portals” under Conditional Policies now GA!
- MFA for per-user MFA users: This policy covers users with per-user MFA and require MFA for all cloud apps – Who it´s for: Existing per-user multifactor authentication customers
- MFA for high-risk sign-ins: This policy covers all users and requires MFA and reauthentication for high-risk sign-ins – Who it´s for: Microsoft Entra ID Premium Plan 2 customers
What if I not will use MFA?!
You can still customize policies by etc. excluding users, groups, or roles that you do not want to apply the policies to, such as emergency and break glass accounts. Microsoft cant still not “force” MFA on all tenantes worldwide on that way, as some setups/companyes can have some need/senarios where its needed to exclude stuff (but I hope NOT some stuff is setup like that! 🤣)
But we see whats is comming out of this – im exited to see the final product live out there!
But hey – you have been implemented MFA for long time right – no issues right haha? 😁😉🔒
Administer you corrent Conditional Access policies – or better, create them if not using them today!
To create, manage or change Conditional Access policies, you need to go to the Conditional Access – Microsoft Entra admin center portal – here you can see all the needed settings, manage exitsing Canditional Access policyes and there targets. And if needed, you can read more about deployment of policies here: Plan a Microsoft Entra Conditional Access deployment | Microsoft Learn – it can a lot, so for now I will not cover it in this post 😉
Some Common Conditional Access policy can be:
- Require MFA for Azure management with Conditional Access | Microsoft Learn
- Require multifactor authentication for Microsoft admin portals | Microsoft Learn
- Sign-in risk-based multifactor authentication | Microsoft Learn
- Require MFA for administrators with Conditional Access | Microsoft Learn
- Require phishing-resistant multifactor authentication for Microsoft Entra administrator roles | Microsoft Learn
- Control security information registration with Conditional Access | Microsoft Learn
- Conditional Access – Require approved app or app protection policy | Microsoft Learn
- Require reauthentication with Conditional Access | Microsoft Learn
- and many more…
Check it you – you will be surprised what it can do! 🥳😍🙌🔒
Conclusion
So please Admins, customers, vendors, Partnars and all that in between – please take this into consideration as this will change in your exitsing Conditional Access design and your Entra ID enterprise teanant/setup.
And again – if you are NOT using this today, start doing it and stay more secure then yesterday!
This will gradually happen on worldwide tenants soon 🥷🔒
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳
Secure your resources with Microsoft-managed Conditional Access policies | Microsoft Learn