Last Updated on October 31, 2023 by Michael Morten Sonne
Table of Contents
- Intoduction
- Reducing the URL set
- Overview of the old domains MDE use
- Expanding network configuration options
- Remaining services required for connectivity
- Prerequisites
- Onboarding and migration from the “Standard” to new “Streamlined” connection
- Migration recommendations
- Check the connectivity to the new endpoints
- Learn more
- Conclusion
Feature is in public preview as this is written
Intoduction
Update – 31/10/2023 – MacOS and Linux support is now available in public preview for devices running version 101.2309+ on Insider Fast (Beta) ring!
The introduction of the new security services deployment method for devices onboarded to Microsoft Defender for Endpoint is a welcomed development – but sometimes being complex too 😟
Historically, the process of setting up connectivity between endpoints and Defender for Endpoint services was a challenging endeavor. This involved the intricate configuration of firewalls and proxies, often necessitating a detailed list of specific URLs. Additionally, some network devices even required the use of static IPs to achieve the same goal, which added more complexity to the process. After deployment, the maintenance of these configured URLs was an ongoing concern, especially when new services were introduced 🫢
The announcement of this new method in the public preview for Windows OS is excitement! 😍
It promises to simplify the device connectivity and onboarding experience for Microsoft Defender for Endpoint, which is a significant improvement. By streamlining these operations, it not only reduces the complexity and potential for errors during deployment but also offers a more efficient and manageable approach to maintaining these connections. This development will likely be well-received by engineering teams and IT professionals tasked with enhancing security services.
There is so many “fun” endpoints of URL´s this refering to today – etc. a dependency on *.blob.core.windows.net – this needs to be eliminated, as customer services is located befind here too 🫢
Can you remeber what service that is? 😉
MacOS and Linux support will come soon with the next Insider Fast (Beta) release version 2309 for so. Microsoft will update the docs page once it becomes available and you will be able to see the new onboarding experience in your portal.
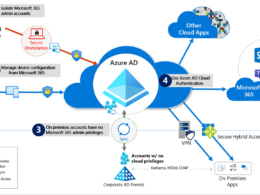
The new experience makes it easier for security teams and network admins to configure and manage Microsoft Defender for Endpoint services by reducing the number of URLs required to connect to cloud services during onboarding, expanding network configuration options to support IPs and simplifying post-deployment network management under a new single Microsoft Defender for Endpoint domain. This removing public blob storage URLs under this new domain, and providing the additional option to use static dedicated IPsfor Microsoft Defender for Endpoint – this helps a lot if you etc. use proxies in your network!
What is the change
The major changes to all this is:
Defender for Endpoint wont to streamlines the device connectivity for security teams and network admins by:
- Reducing the Defender for Endpoint URL set by more than 60%
- Offering the option to use static Defender for Endpoint-dedicated IP ranges instead of URLs when configuring their network environments
- Adding support for Defender for Endpoint Azure service tags – that´s nice!
There is a smart webpage here to for lookups (based on the official lists): Azure IP Ranges (not official), official is here: Azure service tags overview | Microsoft Learn - Extending Defender for Endpoint client analyzer to support testing this new connectivity method in both pre & post-onboarding scenarios
This is a big change on a new direction! I love it 🥳
To use the new streamlined connectivity method, devices will need to onboard or migrate to Defender for Endpoint using an updated onboarding package. Learn more about onboarding and configuring your network environment.
Reducing the URL set
Before, security teams needed to separately configure and manage each of the following services in their networks. This would include updating their network for any new services. Under this solution, any future Defender for Endpoint services will be consolidated under the simplified domain – eliminating the need for security admin to make adjustments.
Under the new streamlined onboarding experience, the Defender for Endpoint-recognized simplified domain *.endpoint.security.microsoft.com will consolidate and replace URLs for the following core Defender for Endpoint services:
- Cloud-delivered protection (MAPS)
- Malware sample submission storage
- Automated investigation and remediation sample storage
- Defender for Endpoint command and control
- Endpoint detection and response cyber data
Domain lists – new and the old one to see the differences
All of the regional URLs listed in the mde-urls-commercial.xlsx (live.com) list from Microsoft Old).
All of the regional URLs listed in the mde-streamlined-urls-commercial.xlsx (live.com) list from Microsoft NEW).
Overview of the old domains MDE use
This solution will off coruse simplify new and future deployment and management of MDE cloud services and provide the option of configuring allow-lists using static, MDE-dedicated IP ranges in network security devices that do not support host name resolution.
The following MDE-specific services are replaced under the new domain:
- Cloud-delivered Protection & MAPS Service: 2-5 URLs
- *.wdcp.microsoft.com, *.wd.microsoft.com, .cp.wd.microsoft.com
- Malware Sample Submission Storage Service: 20 blob URLs
- <region>.blob.core.windows.net (general domain for Storeage Accounts in Azure – finally gone!)
- MDE AutoIR Service: 10 generic blob URLs
- automatedirstrprd<region>.blob.core.windows.net
- MDE Command & Control Service: 10 URLs
- winatp-gw-<region>.microsoft.com
All the “old” service endpoint (as per. 29-10-2023 from officel docs) is:
| Category | Consolidated URLs |
|---|---|
| MAPS: cloud-delivered protection | *.wdcp.microsoft.com *.wd.microsoft.com |
| Cloud protection & security intelligence updates for macOS and Linux | unitedstates.x.cp.wd.microsoft.com europe.x.cp.wd.microsoft.com unitedkingdom.x.cp.wd.microsoft.com x.cp.wd.microsoft.com https://www.microsoft.com/security/encyclopedia/ adlpackages.aspx |
| Malware Sample Submission Storage | ussus1eastprod.blob.core.windows.net ussus2eastprod.blob.core.windows.net ussus3eastprod.blob.core.windows.net ussus4eastprod.blob.core.windows.net wsus1eastprod.blob.core.windows.net wsus2eastprod.blob.core.windows.net ussus1westprod.blob.core.windows.net ussus2westprod.blob.core.windows.net ussus3westprod.blob.core.windows.net ussus4westprod.blob.core.windows.net wsus1westprod.blob.core.windows.net wsus2westprod.blob.core.windows.net usseu1northprod.blob.core.windows.net wseu1northprod.blob.core.windows.net usseu1westprod.blob.core.windows.net wseu1westprod.blob.core.windows.net ussuk1southprod.blob.core.windows.net wsuk1southprod.blob.core.windows.net ussuk1westprod.blob.core.windows.net wsuk1westprod.blob.core.windows.net |
| Defender for Endpoint Auto-IR Sample Storage | automatedirstrprdcus.blob.core.windows.net automatedirstrprdeus.blob.core.windows.net automatedirstrprdcus3.blob.core.windows.net automatedirstrprdeus3.blob.core.windows.net automatedirstrprdneu.blob.core.windows.net automatedirstrprdweu.blob.core.windows.net automatedirstrprdneu3.blob.core.windows.net automatedirstrprdweu3.blob.core.windows.net automatedirstrprduks.blob.core.windows.net automatedirstrprdukw.blob.core.windows.net |
| Defender for Endpoint Command and Control | winatp-gw-cus.microsoft.com winatp-gw-eus.microsoft.com winatp-gw-cus3.microsoft.com winatp-gw-eus3.microsoft.com winatp-gw-neu.microsoft.com winatp-gw-weu.microsoft.com winatp-gw-neu3.microsoft.com winatp-gw-weu3.microsoft.com winatp-gw-uks.microsoft.com winatp-gw-ukw.microsoft.com |
| EDR Cyberdata | events.data.microsoft.com us-v20.events.data.microsoft.com eu-v20.events.data.microsoft.com uk-v20.events.data.microsoft.com |
Endpoints/URLs left for consolidation still
The following URLs are not included in consolidation for now as it looks like. Please ensure you maintain connectivity with the following Windows-required URLs: (for full list see mde-urls-commercial.xlsx (live.com))
| Category | Endpoint/URL (not included) |
| CRL* | crl.microsoft.com ctldl.windowsupdate.com www.microsoft.com/pkiops/* www.microsoft.com/pki/* |
| EDR Cyberdata** | events.data.microsoft.com us-v20.events.data.microsoft.com eu-v20.events.data.microsoft.com uk-v20.events.data.microsoft.com |
| MU / WU | go.microsoft.com definitionupdates.microsoft.com https://www.microsoft.com/security/encyclopedia/adlpackages.aspx |
| SmartScreen/Network Protection | *.smartscreen-prod.microsoft.com *.smartscreen.microsoft.com |
| Windows Notification Service*** | *.wns.windows.com login.microsoftonline.com login.live.com |
**EDR Cyberdata is in scope for future consolidation work. This service has static IPs available under the ‘OneDSCollector’ Azure service tag (see: Home Page – Azure IP Ranges). Traffic for these IPs is not limited to EDR cyber data- its shared across Microsoft applications such as Office, Intune, Teams, etc.
***WNS is an optional service used for decreasing initial connection time of Live Response. Still get full functionality of Live Response without this URL.
Expanding network configuration options
Previously the non/low use of dedicated IPs made configuring Defender for Endpoint more challenging for environments using older firewalls devices without hostname resolution or wildcard support for firewall rules and so on.
For more flexibility across diverse network environments, Microsoft now offer an alternative to URLs. Security teams can use static IP ranges that are dedicated to Defender for Endpoint or subscribe to the Azure service tag. – minimizing the complexity of frequent updates to network security rules. Learn more about that here: Azure virtual network service tags.
Configure connectivity using the simplified domain
Configure your environment to allow connections with the simplified Defender for Endpoint domain: *.endpoint.security.microsoft.com. For more information, see Configure your network environment to ensure connectivity with Defender for Endpoint service.
You must maintain connectivity with remaining required services listed under the updated list. For example, Certification Revocation List, Windows update and SmartScreen.
Configure connectivity using static IP ranges
With streamlined connectivity, IP-based solutions can be used as an alternative to URLs. These IPs cover the following services:
- MAPS
- Malware Sample Submission Storage
- Auto-IR Sample Storage
- Defender for Endpoint Command and Control
The EDR Cyber data service must be configured separately if you are using the IP method (this service is only consolidated on a URL level).You must also maintain connectivity with other required services including SmartScreen, CRL, Windows Update, and other services.
In order to stay up to date on IP ranges, it is recommended to refer to the following Azure service tags for the Microsoft Defender for Endpoint services. The latest IP ranges will always be found in the service tag. For more information, see Azure IP ranges.
| Service tag name | Defender for Endpoint services included |
|---|---|
| MicrosoftDefenderForEndpoint | MAPS, Malware Sample Submission Storage, Auto-IR Sample Storage, Command and Control. |
| OneDsCollector | EDR Cyberdata Note: The traffic under this service tag isn’t limited to Defender for Endpoint and may include diagnostic data traffic for other Microsoft services. |
The following table lists the current static IP ranges as this post is written. For latest list, refer to the Azure service tags.
| Geo | IP Ranges |
|---|---|
| US | 20.15.141.0/24 20.242.181.0/24 20.10.127.0/24 13.83.125.0/24 |
| EU | 4.208.13.0/24 20.8.195.0/24 |
| UK | 20.26.63.224/28 20.254.173.48/28 |
| AU | 68.218.120.64/28 20.211.228.80/28 |
Remaining services required for connectivity
With the new streamlined experience, most of the individual required URLs or domains for Defender for Endpoint services will no longer be required for connectivity. These individual URLs will be funneled into a consolidated URL (and resolved then to the IP ranges).
Some required services like core services to Windows and updates, are not included in the URL consolidation (that make sense), therefore remains to be configured separately. Learn more about this in the new Defender for Endpoint required URL list.
To align with Defender for Endpoint security and compliance standards, data will be processed and stored in accordance with the tenant’s physical location. Based on client location, traffic may flow through different Azure datacenter regions. For more information, see Microsoft Defender for Endpoint data storage and privacy | Microsoft Learn.
Prerequisites
To use the new streamlined onboarding experience devices must meet specific prerequisites. Please make sure each device meets the minimum operating system, Windows KB, and antivirus version requirements before proceeding.
Devices running on the Microsoft Monitoring Agent (MMA) agent will need to continue onboarding using the MMA method and its corresponding required URL set. Windows devices running RS1 through RS4 can use the streamlined onboarding experience but will require a longer list of URLs.
Licenses
Applicable licenses is:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for Business
- Microsoft Defender Vulnerability Management
So – the hole Microsoft Defender for Endpoint suite! 😍
Do you want to experience Defender for Endpoint? Sign up for a free trial right here!.
This link gives you a Microsoft Defender for Endpoint P2 Trial free for a 3 month period from Microsoft with 25 licenses! 🙌
Supported Operating Systems
(As this is written)
- Windows 10 version 1809+
- Windows 11
- Windows Server 2019
- Windows Server 2022
- Windows Server 2012 R2, Server 2016 R2, fully updated running Defender for Endpoint modern unified solution (installation through MSI).
- macOS and Linux supported releases running product version 101.2309+ on Insider Fast (Beta). Note: Microsoft will update the documentation once this is available.
Windows Minimum Component Versions:
- Microsoft Defender Antimalware client: 4.18.2211.5
- Microsoft Defender Engine: 1.1.19900.2
- Microsoft Antivirus (Security Intelligence): 1.391.345.0
- Minimum Windows KB/Sense version: >10.8040.*/ March 8th 2022+ (see table in public documentation)
MacOS/Linux Minimum Component Version:
- 2309+ version.
Allways – check Microsoft docs for newest information 😉
Onboarding and migration from the “Standard” to new “Streamlined” connection

First confirm your devices meet the prerequisites and make sure that your network environment is properly configured to support the new streamlined onboarding experience.
The new streamlined experience enables you to configure your network with either the consolidated domain or IPs. Learn more about configuring network connectivity.
Now when all is done, your network and devices are updated to communicate with the required destinations, you now can begin the device onboarding or migration process 👌🥷
Make sure to confirm successful connectivity with Defender for Endpoint services before moving forward.
Remember that the end-user experience or how Defender for Endpoint functions on a device will not change. Only the URLs or IPs that a device uses to connect to the service will change!
For exitsting devices already onboarded to your Defender for Endpoint tenant using the standard method that wish to migrate to the streamlined onboarding method, just run the streamlined package on the device and then reboot the device – yes, that´s it (have tested too to by my self under the development and after) 🥳
Remember that the types of onboading is as follows:

Once the device is rebooted, the device should (if not, check the next step Check the connectivity to the new endpoints) automatically switch over to the new connectivity and communicate to the Microsoft Defender for Endpoint service again.
For most operating systems, device offboarding is not required to migrate. During migrations, device ID’s are retained and there is no loss of data history. So this is nice and cool – data/history on devices like this is important!
Windows 10 versions 1607, 1703, 1709, and 1803 do not support reonboarding. Offboard first and then onboard using the updated package. These versions also require a longer URL list.
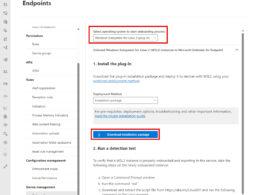
If all this is correct, then heads up and download the streamlined onboarding package in the Microsoft Security Portal under Settings > Endpoint > Onboarding alongside the standard onboarding approach before (and alltime). To get started, follow the instructions here.
The onboarding itself it not covered here for now – let´s see later.
But – it´s not heard – so test it and migrate your devices! 👌

Migration recommendations
- As allways – start small! The recommended approach is to begin with a limited set of devices – ofc!
Utilize any of the supported deployment tools to apply the onboarding blob, and subsequently, monitor the connectivity and test the features in MDE to ensure that is works in your enviroment. If you’re implementing a new onboarding policy, take care to exclude the device from any pre-existing onboarding policies to avoid conflicts.
I have used Intune for test and local script to test it 😉 - Validate and monitor upgraded devices. Once the initial onboarding of the limited set of devices is complete, confirm that the devices have successfully joined the network and are effectively communicating with the service.
- Complete migration for all devices. Now, you have the option to progressively introduce the migration to a broader array of devices. To finalize the migration, you can substitute the existing onboarding policies and eliminate the old URLs from your network devices.
Check the connectivity to the new endpoints
To check connections to the new endpoints, we can check this with Advanced Hunting in the Defender Portal.
For this, go to the Advanced Hunting page in the Microsoft Defender portal here
Run the following query to ensure devices are connecting with the proper MDE endpoints (by checking the RemoteURL column for ‘endpoint.security.microsoft.com’).
DeviceNetworkEvents
| where DeviceName contains "YourDeviceName" //Put the name of a device here
| where ActionType == "ConnectionSuccess" and LocalIPType != "Loopback" and RemoteUrl
!endswith "v20.events.data.microsoft.com"
| where InitiatingProcessFolderPath contains "windows defender"
| where RemoteUrl != ""
| project Timestamp, DeviceName, RemoteIP, RemoteUrl, InitiatingProcessFileName,
InitiatingProcessFolderPath And if all is good – it should look like:


Use can use this KQL also to select the data from the DeviceInfo table too:
DeviceInfo
| where DeviceName contains "YourDeviceName" //Put the name of a device here
| project Timestamp, ConnectivityTypeThe following query can be used to identify devices on which you have run the onboarding script (Registry there includes the new URL). Note this may not necessarily mean the device is connecting yet (i.e. MMA devices, reboot not initiated):
DeviceRegistryEvents
| where ActionType == "RegistryValueSet" and RegistryValueName == "OnboardingInfo"
| where RegistryValueData has "endpoint.security.microsoft.com"
| distinct DeviceNameIf all in the onboarding was well and (onboarded and rebooted), check the OnboardedInfo key in the Registry Editor at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Advanced Threat Protection.

Please note the field may be updated in Registry prior to reboot (reboot is still necessary for previously onboarded devices for full connectivity switch).
Download client analyzer for Windows OS
- The latest stable edition is available for download from following URL: https://aka.ms/MDEAnalyzer
- The latest preview edition is available for download from following URL: https://aka.ms/BetaMDEAnalyzer
Download client analyzer for macOS or Linux
- The latest stable edition will be integrated into the MDE for Endpoint agent. Ensure that you are running the latest edition for either macOS or Linux.
- The latest preview edition is available for direct download from following URL: https://aka.ms/XMDEClientAnalyzer
There is more ways to check this on too – they are listed here:
- Tracking with advanced hunting in Microsoft 365 Defender
- Track locally using Event Viewer (for Windows)
- Run tests to confirm connectivity with Defender for Endpoint services
- Checking the registry editor
- PowerShell detection test
This is realy nice tools to troubleshoot! 👌
How to use client analyzer tool
You can use MDE Client Analyzer (Beta) to validate connectivity with new URLs pre-onboarding.
To test this, run MDE Client Analyzer (Beta) on the device to confirm pre-onboarding connectivity with the new endpoints:
- Download and extract Client analyzer from https://aka.ms/BetaMDEAnalyzer
- Download ‘simplified’ onboarding package for relevant OS. Package found under: Settings > Endpoints > Device management > Onboarding in the Microsft 365 Defender portal.
- Extract the .cmd from onboarding package (you need to use this method for this)
- Open a Command Prompt as administrator
- Run mdeclientanalyzer.cmd -o from within MDEClientAnalyzer folder. The
command will use parameters from onboarding script to test the connectivity.
Etc.: mdeclientanalyzer.cmd -o “C:\Temp\WindowsDefenderATPLocalOnboardingScript.cmd” - View the connectivity results within the HTML output file or command prompt
Things to know
- The streamlined onboarding experience is currently not supported for APIs. This includes Microsoft Defender for Cloud and Microsoft Intune.
- The new streamlined onboarding experience has specific prerequisites that do not apply to the standard onboarding experience. Please make sure your devices meet the prerequisites before continuing.
Learn more
Read more on this sites, as the documentation over time can change:
Conclusion
The introduction of this new method for deploying security services within Microsoft Defender for Endpoint marks a significant step forward in simplifying the traditionally challenging and complex process of configuring connectivity between endpoints and security services. This change not only streamlines the deployment process but also enhances the overall management of these services!
By making device connectivity and onboarding more efficient and user-friendly, this innovation is poised to greatly benefit engineering teams and IT professionals. I have seen a lot of writelisting and so on in my time in IT – and it takes time… time from other stuff!
It was also for me fun to test this with the product team under the development as a member of Microsoft Customer Connection Program – www.aka.ms/JoinCCP.
This is then shared now as the announcing is public – as else, under NDA with information I cant share.
I think this is all for this one 🙌
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳