Last Updated on February 19, 2024 by Michael Morten Sonne
Table of Contents
- Intoduction
- The “unknow” limit for many organizations
- How to check what objects are consuming Entra ID Directory quota limit
- Entra ID objects there counts
- Configuring alerts for validation and quota exhaustion
- Conclution
Intoduction
The inability to create new users in Entra ID persists even when syncing users from On-prem Active Directory to Entra ID via your Microsoft Entra ID Connect Server. Moreover, creating app registrations for automation and other purposes is prohibited, effectively halting almost all operations.
During my recent tenure at a large organization, we encountered this issue, albeit too late 😂😂
And this issue shouldn’t occur for you either, so I’m sharing it here—voilà!
Addressing these changes requires the involvement of Senior Engineers at Microsoft, and the alterations may take up to 48 hours to reflect in the Entra ID backend as I understud when I have the direct contact to the support person on Teams (got this kind of help/support many times, and this is so helpfull when this kind of issues happens!) 👍
Entra ID (before known as Azure Active Directory) is Microsoft’s Identity as a Service platform there are the “backend” in all services like Azure IaaS, Microsoft 365 (Exchange Online, Teams, SharePoint, etc.), Defender XDR, Defender for Cloud Apps and so on, but also if you use Entra ID as a Identity Provider (IdP) for Single Sign On to applications and other SaaS services – a lot of services used in many organisations!
It is a global service utilized by millions of organizations worldwide. To ensure the service is usable for this extensive user base, Microsoft operates within certain “limits” necessary to manage the operations efficiently across these worldwide organizations. In Entra ID, one of these limits is the object limit.
All data resides within a database or another format, consuming storage space and IOPS, thereby necessitating meticulous control and management 😉
Understanding your Entra ID tenant’s object limit becomes crucial during troubleshooting sessions involving Entra ID Connect synchronization issues, scalability challenges, and other vague cloud behaviors. This information holds particular relevance when facing hindrances like user and group creation and similar processes.
It is also common when, for instance, you enrolling numerous new devices into Intune, such as during a migration from SCCM, or when registering new devices through the Company Portal.
This scenario commonly arises when, for instance, enrolling numerous new devices into Intune, such as during SCCM migration, or registering new devices via the Company Portal. This approach streamlines Office application management, like Outlook, Teams, and OneDrive, and facilitates the integration of App protection policies on mobile devices, among other functions. Similarly, it applies when inviting a significant number of new Guest users from another organization for B2B purposes or similar functions within your Entra ID tenant.
The “unknow” limit for many organizations
All Entra ID’s limits are described on the Service limits and restrictions – Microsoft Entra ID | Microsoft Learn page on Microsoft Docs. For Entra ID’s object limit, the following is shared:
“By default, a maximum of 50,000 Microsoft Entra resources can be created in a single tenant by users of the Microsoft Entra ID Free edition. If you have at least one verified domain, the default Microsoft Entra service quota for your organization is extended to 300,000 Microsoft Entra resources.
The Microsoft Entra service quota for organizations created by self-service sign-up remains 50,000 Microsoft Entra resources, even after you perform an internal admin takeover and the organization is converted to a managed tenant with at least one verified domain. This service limit is unrelated to the pricing tier limit of 500,000 resources on the Microsoft Entra pricing page.”
And there is a lot more to read – but it is not covered in this post 😉
To go beyond the default quota, you must contact Microsoft Support to get help 😎
How to check what objects are consuming Entra ID Directory quota limit
Entra ID Portal
This method does not display everything in the same view or count them together.
- Login to Entra ID Admin Center (Microsoft Entra admin center )
- Under Identity > Overview you will see this:

This will provide you with a overview of the object status within Entra ID (sample data here from my lab tenant).
However, as mentioned previously, this does not encompass all the objects within the Entra ID database for your tenant. It only covers users, groups, applications, and devices, excluding custom RBAC roles, App registrations, and similar entities as you can se under here.
Graph Explorer
You can quickly test this in the Graph Explorer: https://developer.microsoft.com/en-us/graph/graph-explorer.
You can navigate to the Graph Explorer at aka.ms/ge too 👍
Now sign into Graph Explorer with your account that has access to the directory (and the right permissions is needed to give that assess)
The GET command we need to use require the following API permission for Microsoft Graph:
- Organization.Read.All
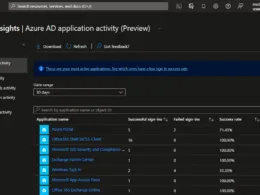
Run the beta query (GET):
https://graph.microsoft.com/beta/organization?$select=directorySizeQuotaHere you will see an output like this:

Entra ID objects there counts
The objects listed here contribute to the quota count for Entra ID:
- Users
- Groups
- Contacts
- Devices
- Applications
- Deleted Applications
- Service Principals
- Roles (Custom roles too)
- Extensionproperties
If you encounter strange issues when creating objects, decided on the following approaches to address the issue – please review:
- Verify Entra ID quota exhaustion and identify the objects consuming Entra ID resources.
- Remove obsolete objects, such as users and devices, from Entra ID.
- Contact Microsoft Support to request a quota increase for your specific tenant.
If you followed below approach to identify the root cause and ensure it will not happen again, below the steps:
- Configuring Alerts for Validation and Quota Exhaustion:
- Setting up alerts to validate and monitor Entra ID object counts regularly.
- Implementing daily alerts specifically for Entra ID object count variations (this depends – you can comment the code out/remove it in the script provided if needed).
- Enabling alerts for Entra ID object quota exhaustion (with this script etc.).
- Root Cause Analysis:
- Conducting a investigation to identify the root cause of the issue – to many new enrollment of devivces or some automation or synces on-prem objects?
- Baseline for Entra ID Objects:
- Establishing a baseline for necessary Entra ID objects within the organization involves considering synced on-prem Active Directory objects. It’s essential to note that not all on-prem Active Directory objects need to synchronize with Entra ID. This selective synchronization ensures that only relevant objects integrate into the Entra ID environment. If otherwise, accounts, etc., can be misused or compromised, potentially leading to attacks from on-premises to Entra ID.
Read more about this etc. in this post: Azure AD – Why use Cloud-Only Administrative/normal accounts and how to protect them in Azure AD from on-premises attacks – Blog – Sonne´s Cloud (sonnes.cloud) - Determining the expected count of objects such as users, computers, etc.
- Establishing a baseline for necessary Entra ID objects within the organization involves considering synced on-prem Active Directory objects. It’s essential to note that not all on-prem Active Directory objects need to synchronize with Entra ID. This selective synchronization ensures that only relevant objects integrate into the Entra ID environment. If otherwise, accounts, etc., can be misused or compromised, potentially leading to attacks from on-premises to Entra ID.
- Object Quota Adjustment:
- Comparing the baseline with the current object count.
- If required, increasing the object quota based on the established baseline and actual need.
In the following sections, each of these actions need to be explained further for clarity – but not in this post 😉
Configuring alerts for validation and quota exhaustion
We wanted to add alerts to ensure we is notified if we are nearing the limit (but before this happens!).
You can achieve this by using etc. an Automation Account account in Azure to run the script or run it on a server you use for automation today – its a PowerShell script, so it´s easy to use and run in many places with a internet connection! 😎
What to use – a PowerShell script
We can automate this process using a PowerShell script—all we need are the appropriate permissions and a platform where the PowerShell script can access the Microsoft Graph API.
The provided script, designed for illustrative purposes, employs a Teams Webhook to transmit messages to a Teams Channel. This channel may reside internally within your IT/AD department or elsewhere. You retain the flexibility to incorporate additional methods or eliminate my Teams Webhook code as required.
Should you desire, you can expand its functionality to send emails as well. However, that might be like spam, don’t you think? 😂🤪
If you have any suggestions for improvement, feel free to let me know or create a pull request on GitHub. There’s ample room for enhancement, and I aim to refine it gradually if necessary and as time allows. 😎
The script direct from GitHub:
Requirements
- Microsoft Graph API permissions (Organization.Read.All)
- An App registration with client secret or certificate (recommened to use certificate besed…)
- A place to run the script from (etc. an Azure Automation account or a server with internet connection)
Configure Microsoft Graph API permissions in Entra ID for the app registration
In order to gather the required data for the script, it is necessary to create an App registration in Entra ID. This registration is utilized for the connection to the MS Graph API.
- Open your Microsoft Entra admin center portal
- Go to the Applications menu under Identity and under here, select App registrations
- Click on New registration

- A new wizard will appear, prompting us to provide a application name. The remaining fields can be left as default for this task 😉
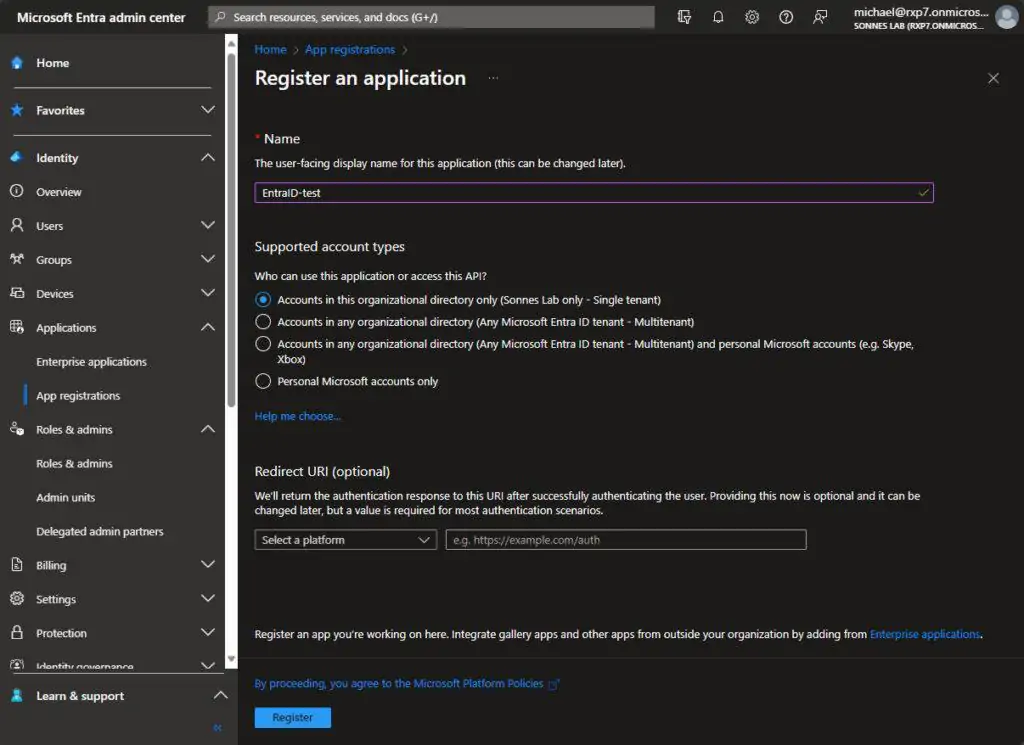
- Next, click on Register and the new App registration will be successfully created. It will appear in the list under App registrations.
The Entra ID role Application Administrator or Global Administrator is needed to create this
- Now is necessary to assign the required API permissions to the app registration. To do this, click on the app registration you have just created.
- Under the App registration, go to the menu API permissions
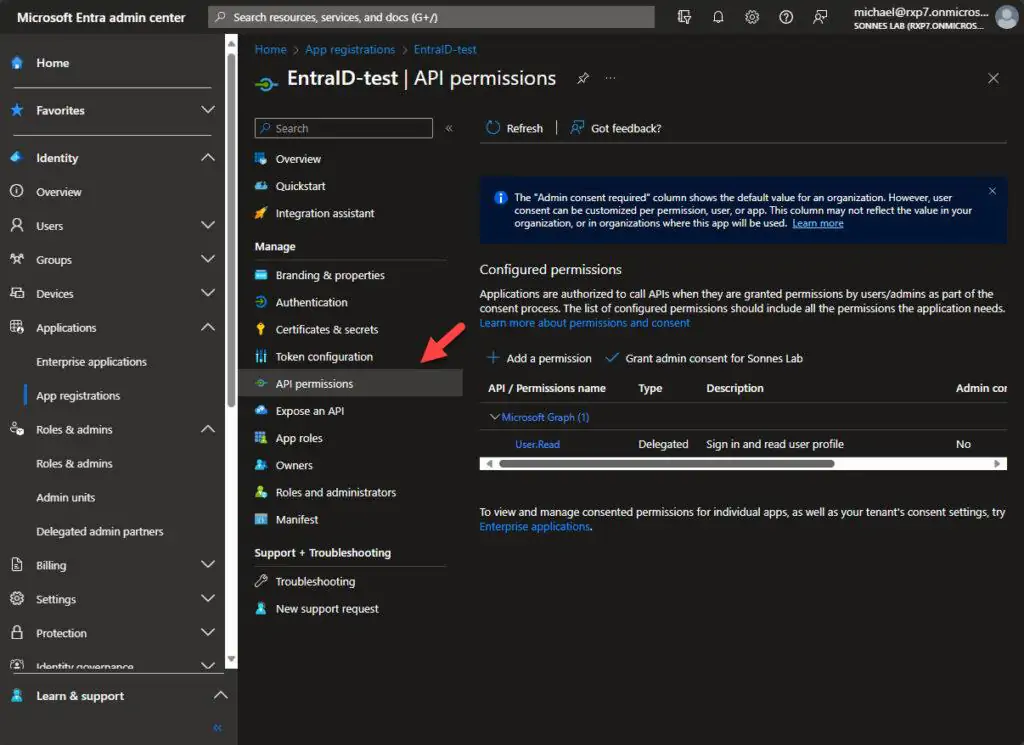
- Now click on Add a permission
- Under Request API permissions, select Microsoft APIs then Microsoft Graph
- Under What type of permissions does your application require select Application permissions
- Find Organization.Read.All under the Organization part
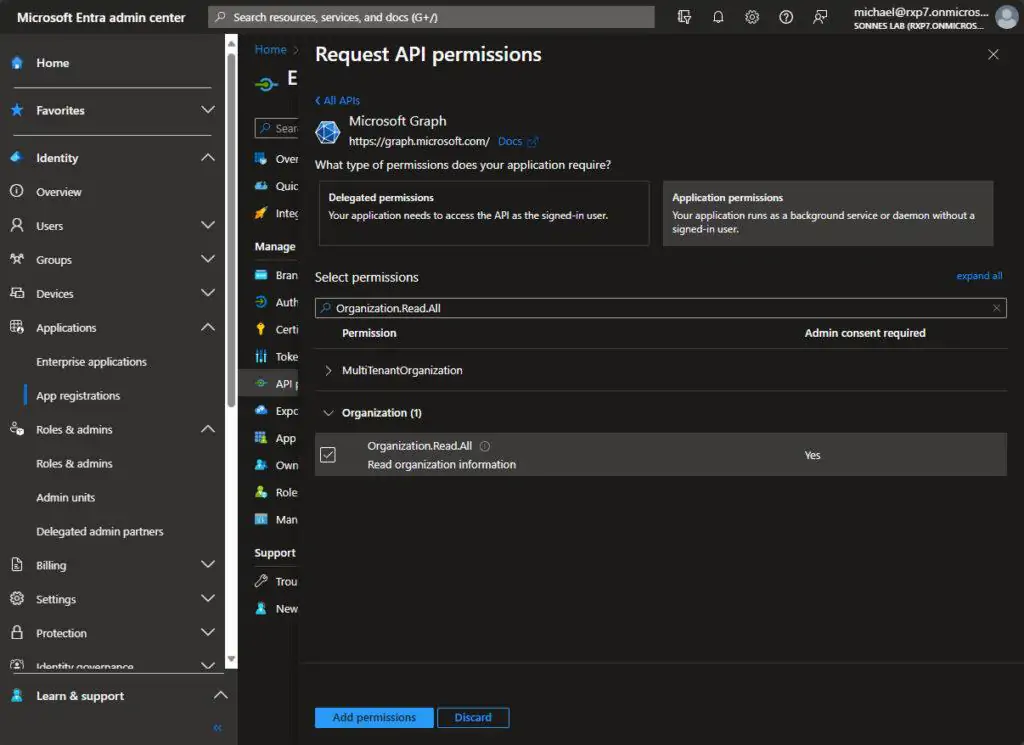
- Click on Add permissions
- The required API permissions have been added, but the access is not yet granted. We need to provide consent to activate these permissions.
Click on Grant admin censent for <tenant name> for the API permissions to be activated
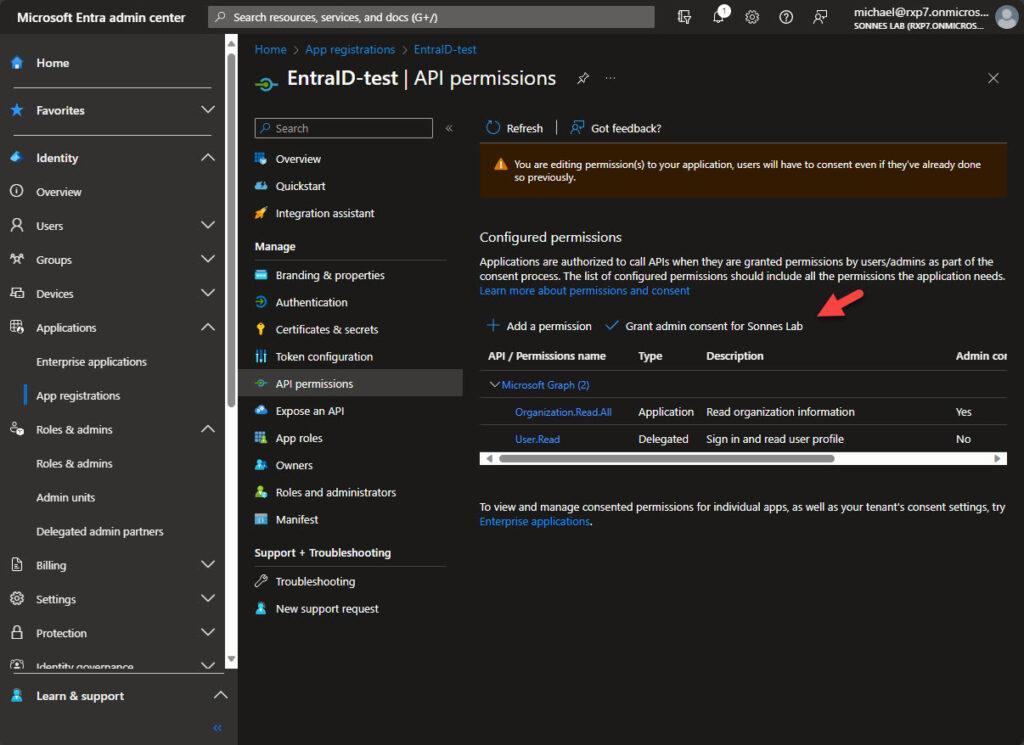
- Next, navigate to the Certificates & secrets menu.
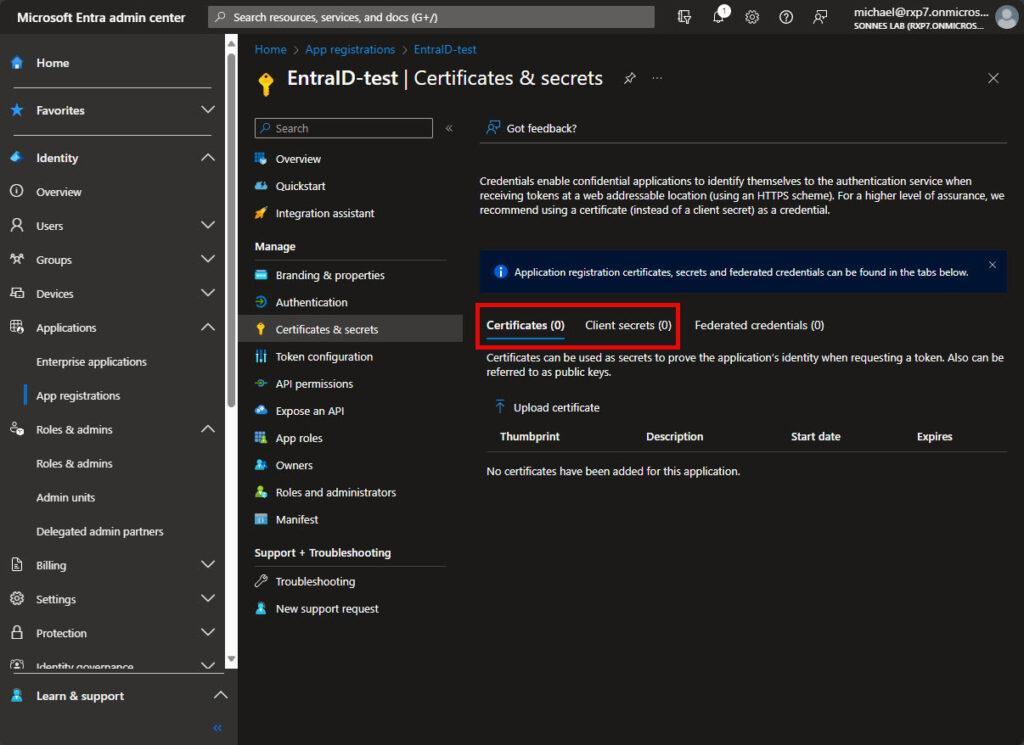
- Here, you have the option to include a client secret (similar to a password) explicitly for this App registration or utilize the public section of a certificate (preferred: from a public Certificate Authority or self-signed) where the private key remains stored on the server or automation account, without necessitating a “password”.
Certificate generation is not covered here in this blog post.
Once this setup is completed, you’re almost prepared to configure the task to run. However, we still require the webhook URL for the Teams Channel messages to be send to from the script when needed 🤪
Follow the next part, and you will get it!
Create webhook URL to send messages to a Teams channel
The webhook URL is used as an endpoint to deliver messages or data directly to a Teams channel, allowing automated or scripted processes to send information to that specific channel.
The script here for my sample have a pin into a Teams channel webhook.
As of today, it appears that this option is unavailable in the new Teams client – we hope it comes in the future!
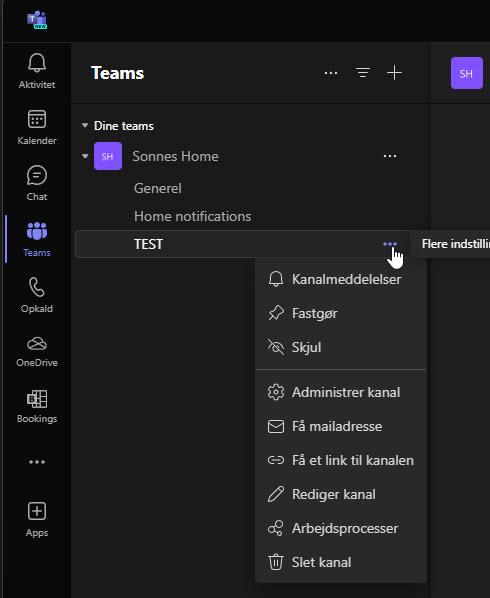
- To obtain the Teams Channel webhook URL, navigate to the Connections menu for the channel, as shown here. Add a webhook if it hasn’t been added already.
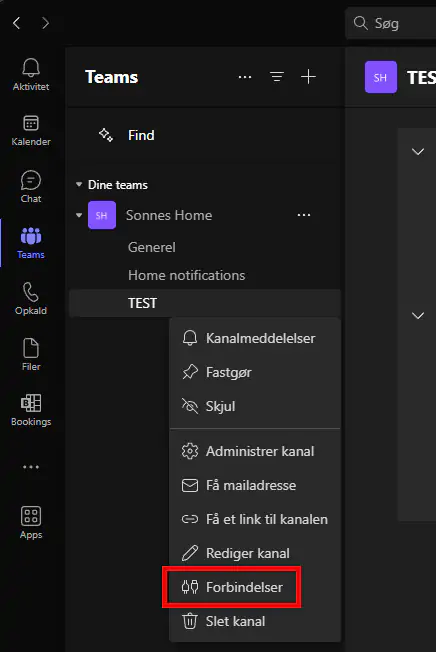
- In the new window, click on Add if you haven’t installed an existing webhook, or select Edit if you’ve already added one to retrieve the URL.
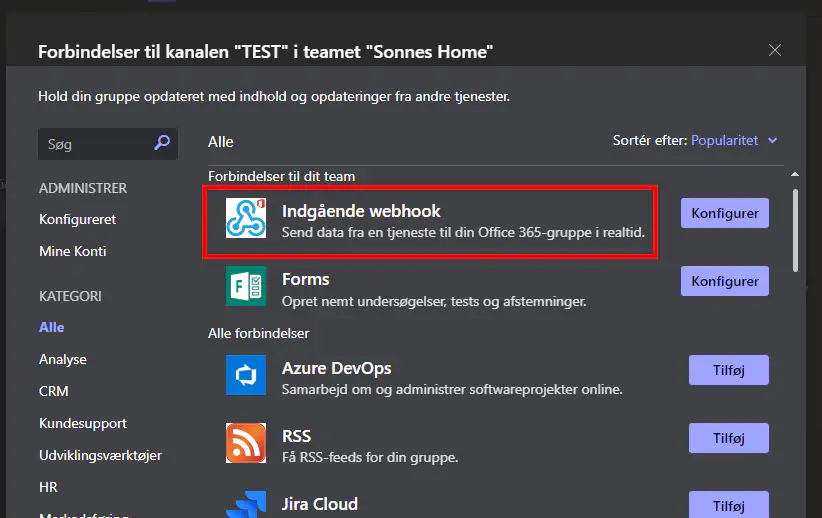
- Assign a specific name to the webhook for easy identification of its purpose, then click on Create.
- Once the Webhook URL is generated and copy it immediately. Save it for future use as it won’t be displayed again!
Having obtained the webhook URL, we can now use it to send messages to the Teams Channel through our PowerShell script. Additionally, we’ll utilize the Microsoft Graph API to retrieve the usage of our Entra ID quota.
Not to the script part 🥳🎉
Usage of the script – parameter usage
To utilize the PowerShell script for the desired purpose, specific arguments need to be passed into it to work.
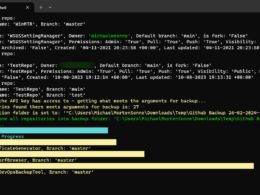
Connect with a certificate:
.\EntraID-QuotaAndNotification.ps1 -ClientId "YOUR_APP_ID" -TenantId "YOUR_TENANT_ID" -CertificateThumbprint "YOUR_CERT_THUMBPRINT" -WebhookUrl "YOUR_WEBHOOK_URL"Connect with a client secret:
.\EntraID-QuotaAndNotification.ps1 -ClientId "YOUR_APP_ID" -TenantId "YOUR_TENANT_ID" -ClientSecret "YOUR_CLIENT_SECRET" -WebhookUrl "YOUR_WEBHOOK_URL"
This script allows for the configuration of either a certificate or a client secret along with essential identifiers such as ClientId, TenantId, and the webhook URL.
The messages sent to Teams
For information, the max limit is set manualy in the code to trigger the diffrent messages – so numbers showen here is correct. The final scripts work as it should 👍
Entra ID Quota limit is okay
This it how it should be normal – all is good, and here is space for manu new objects in Entra ID! 🤩

Entra ID Quota limit will soon be exceeded
This it how it will be when you have a lot if objects in Entra ID – all is still good and here is still space for more objects in Entra ID – but keep an eye on this, as someday it can be used!
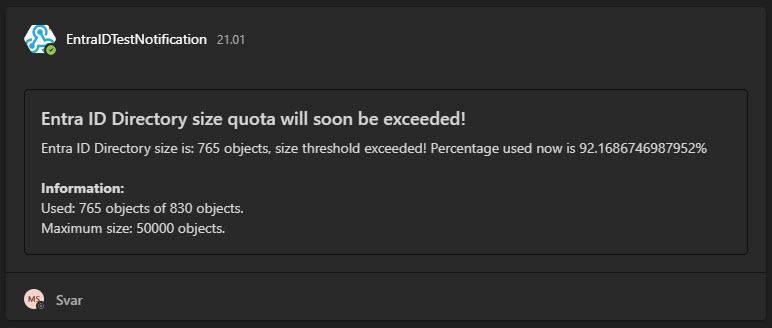
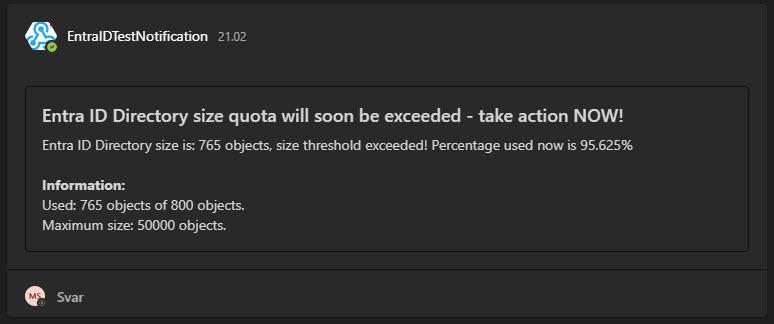
Entra ID Quota limit will soon be exceeded – take action now
This it how it will be when you have a lot if objects in Entra ID and it will soon exceeded – all is not much space left for more objects in Entra ID – but keep an eye on this, as someday it can be used fully – then nothing will work when you trying to create a new user in Entra ID (portal or via Sync from On-prem), create a new group or so!
Entra ID Quota limit is exceeded
This is the scenario when there’s no available space for additional objects in Entra ID. If there’s no room for more objects in Entra ID, any attempt to create a new user in Entra ID (via the portal or through synchronization from an on-premises source), establish a new group, or similar actions will fail.
⚠️ CLEANUP! ⚠️

Conclution
The count of objects in the Entra ID tenant might prove useful one day—be mindful!
This approach offers a convenient means to collect such information and sustain a historical perspective. There is certainly room for enhancement, and I intend to refine it incrementally, if needed and as time allows.
As previously mentioned, please feel free to create a pull request on GitHub to propose any enhancements or modifications to the script. Your contributions would be valued and highly appreciated.
Remember: Contact Microsoft Support for assistance because you can’t extend your Entra ID qouta limit by yourself if needed, and a simple “cleanup” is not sufficient.
To get the help needed, create a support request, or ask Azure community support. You can also submit product feedback to Azure community support.
You can read more here: Error (This company has exceeded the number of objects that can be synchronized) displays in a directory synchronization report – Active Directory | Microsoft Learn
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
As the Christmas holiday approaches and the new year draws near, I have something in development for 2024. Let’s strive to bring it to fruition!
Stay tuned for the new post about something cool! 🥳