Last Updated on May 5, 2024 by Michael Morten Sonne
Intoduction
Enhancing Cybersecurity Operations Through Timely Stakeholder Notifications
Receive near real-time email notifications when actions take place in Microsoft Defender XDR
Reminder: This feature is in Public Preview – and is therefor NOT in Generally Available state!
To start with – it was some time ago some new post´s was out here, and I know it… ❤️
But I have been doing some stuff in the backend and the overall security on this blog, as some time have been used on that – and a lot other in my homelife – but I will focus more here again – stay tuned!
Not only effective in cybersecurity operations are this a team effort. When there is an important incident, it is crucial to ensure that key stakeholders on the team are promptly informed – information and that internal is hard allways right? 🤪
In the realm of cybersecurity, effective operations is about collaboration and timely communication among all team members. When faced with critical incidents, the swift notification of key stakeholders becomes paramount. This proactive approach not only cultivates awareness but also significantly reduces response times and fosters alignment among relevant parties. The essence of these immediate notifications lies in expediting remediation or response actions, particularly concerning entities like identities or devices within an organization’s environment.
Ensuring comprehensive visibility across pertinent stakeholders stands as a cornerstone in this process. Whether these actions are automatically triggered by the system or initiated manually by members of the Security Operations Center (SOC), the critical factor lies in promptly reaching the appropriate team members. Rapid dissemination of information among the right individuals significantly bolsters the efficiency and effectiveness of incident response efforts.
You are not siting in front of your SOC / Monitoring dashboard allways right? 🤔
In essence, the seamless flow of information plays a pivotal role in fortifying cybersecurity strategies. By swiftly informing the relevant stakeholders, organizations can minimize the impact of potential threats, enhance their incident response capabilities, and foster a cohesive approach to safeguarding their digital assets.
Remember, in the ever-evolving landscape of cybersecurity, timely communication is not merely a best practice but a necessity in fortifying an organization’s defense against potential threats.
New feature in Defender XDR
Some weeks ago as I remember, Microsoft where excited to announce the public preview of email notifications for actions taken within Microsoft Defender XDR. This feature enables the SOC and relevant stakeholders (e.g., security admins, IT) to receive notifications whenever an automated or manual action is taken. It allows them to:
- Improve stakeholder alignment – stakeholders can be notified on certain actions and assets, according to relevance for there job – to much nonsense is easyly just deletes and not read! Stop doing this please 🤞
- Gain visibility into the remediation and actions that take place in real time – rules can be set to receive emails on automated (e.g., contain device, disable user) or manual actions (e.g., live response, isolate device, delete email and so on – there is a ton of actions 😂)
- Get notified about actions according to their state – notifications can be set to be sent when an action fails, succeeds, or both if you need that 😘
You can now receive email notifications for manual and automated actions that take place in your environment for Defender for Endpoint, Defender for Identity and Defender for Office 365! 🙌🥳
The scenarios for automatic email notifications
Here are some examples where a SOC can benefit from creating email-based notifications for both a system-automated and a manual action taken in Microsoft Defender XDR (ping me if you know more – I will be happy to add it here if okay 😎
Automated Attack Disruption and Enhanced Visibility in Microsoft Defender XDR
Automatic attack disruption within Microsoft Defender XDR is a powerful feature designed to swiftly neutralize ongoing threats, including ransomware, by taking immediate action, such as disabling compromised user accounts or isolating affected devices. However, these actions are executed only when there is a high degree of confidence in their necessity. To ensure that relevant teams are promptly informed about any containment actions taken automatically, users can establish specific rules of notifications about etc. this action – nice right? 😎
By setting up these rules, IT, SOC, and helpdesk teams can receive email notifications whenever a compromised user account or device is affected. This proactive notification mechanism facilitates swift awareness among the respective teams, enabling them to promptly investigate and remediate issues. Ultimately, this approach aims to bring affected users back online swiftly, restoring productivity across the organization.
Again: You are not siting in front of your SOC / Monitoring dashboard allways right? 🤔
Furthermore, in the realm of cybersecurity, certain assets such as domain controllers (DCs) hold critical significance and are subject to close monitoring by the SOC. To enhance visibility and alertness around sensitive actions, like the initiation of a ‘live response’ session on one or more DCs, the SOC team now has the capability to configure notification rules. These rules trigger notifications whenever there is a successful or even a failed attempt to establish a ‘live response’ session, ensuring heightened awareness and vigilance among security personnel. This is nice – and again, you can do this on a long list of actions! 😍🙌
These strategic notifications not only expedite incident response but also empower cybersecurity teams to proactively manage and mitigate potential risks. With this enhanced visibility into critical actions and automated response mechanisms, organizations can reinforce their defense strategies, effectively combatting threats while maintaining operational efficiency.
How to setup
The first is here shows the easy configuration to setup email notification in Microsoft Defender XDR, while the next shows you what a notification will look like when delivered to your inbox.
It´s easy and straightforward as you can see here:
- Login to your Microsoft 365 Defender portal with your Security Administrator or Global Administrator role (if your organization is using role-based access control (RBAC), you can only create, edit, delete, and receive notifications based on device groups that you are allowed to manage!)
- In the navigation pane of Microsoft Defender XDR, select Settings > Microsoft 365 Defender. Under General, select Email notifications (direct link over here 😉).
- When you are here, you have 3 options – Incidents, Actions (this is focus in this post) and Threat analytics as you can see here:
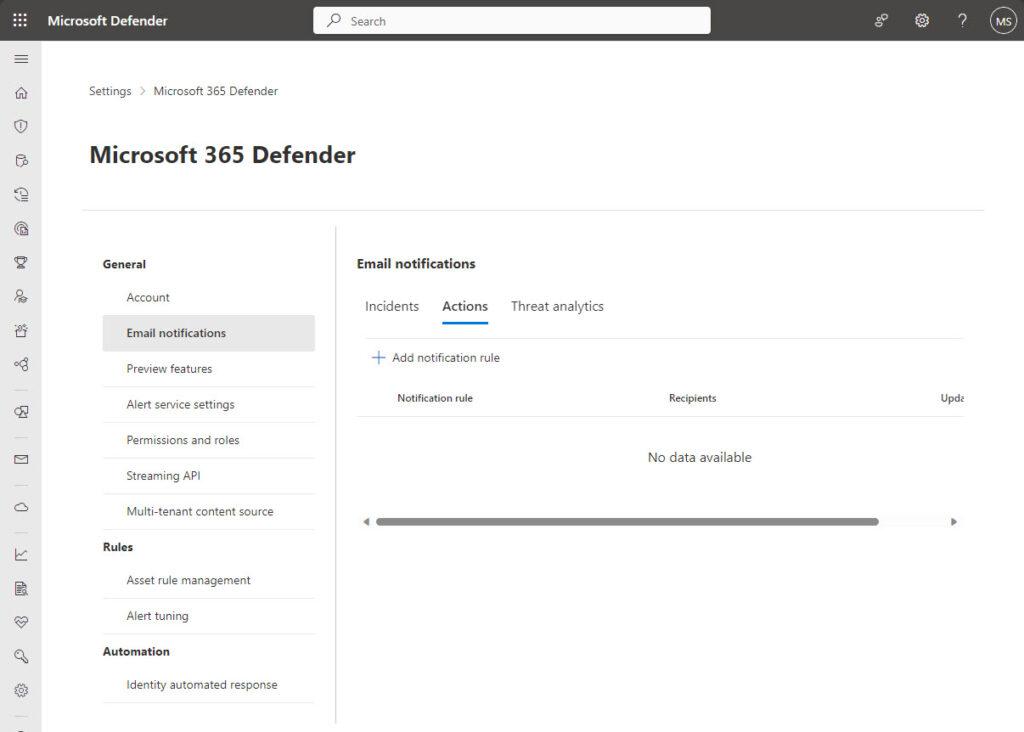
To create a new rule, click on Add notification rule and you will see this. Add a rule name and a description under Basics. Both Name and Description fields accept letters, numbers, and spaces only:
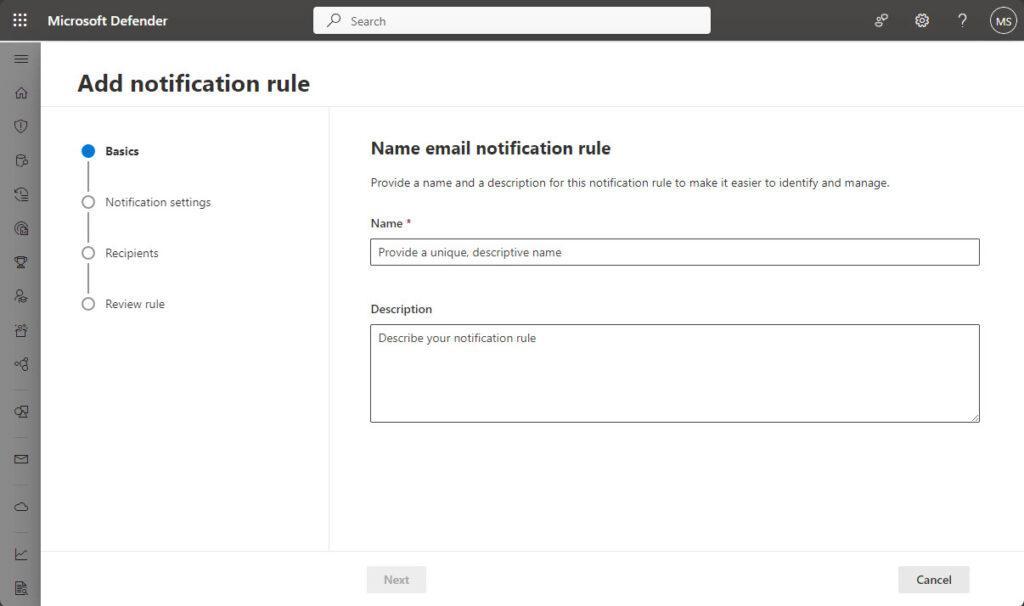
Remembering you to do this on rules and so on you offen create, so its easyer for other to understand the rules and so on – do you?😉
Proceed to the next section by selecting Next located at the bottom of the pane. On the next side the fun is happening – now the rule settings for the notifications itself! 😍
Under Action source you can select Automated actions and/or Manual response actions and under Action you can choose multiple actions available in the checklist.
Note that response actions will vary depending on the Defender workload enabled in your environment – the actions here is depending on your licensing 🤑💸

Here is an example of some actions like Isolate a device, start a Live Response session or etc. Offboard a device!
You can choose to be notified based on the device groups where the response actions are applied in the Device groups scope. To be notified of response actions taken in all current and future device groups, selecting All device groups. To be notified of response actions taken in devices that belong to your selected device group, choose Selected device groups.

And now to a new question for you – have you control of your Device Groups in Defender XDR? 😂🤪
If not – read this: Create and manage device groups in Microsoft Defender for Endpoint | Microsoft Learn
In Microsoft Defender XDR, you can create device groups and use them to:
- Limit access to related alerts and data to specific Microsoft Entra user groups with assigned RBAC roles
- Configure different auto-remediation settings for different sets of devices
- Assign specific remediation levels to apply during automated investigations
- In an investigation, filter the Devices list to specific device groups by using the Group filter.
You can create device groups in the context of role-based access (RBAC) to control who can perform specific action or see information by assigning the device group(s) to a user group. For more information, see Use role-based access control to grant fine-grained access to Microsoft Defender portal | Microsoft Learn.
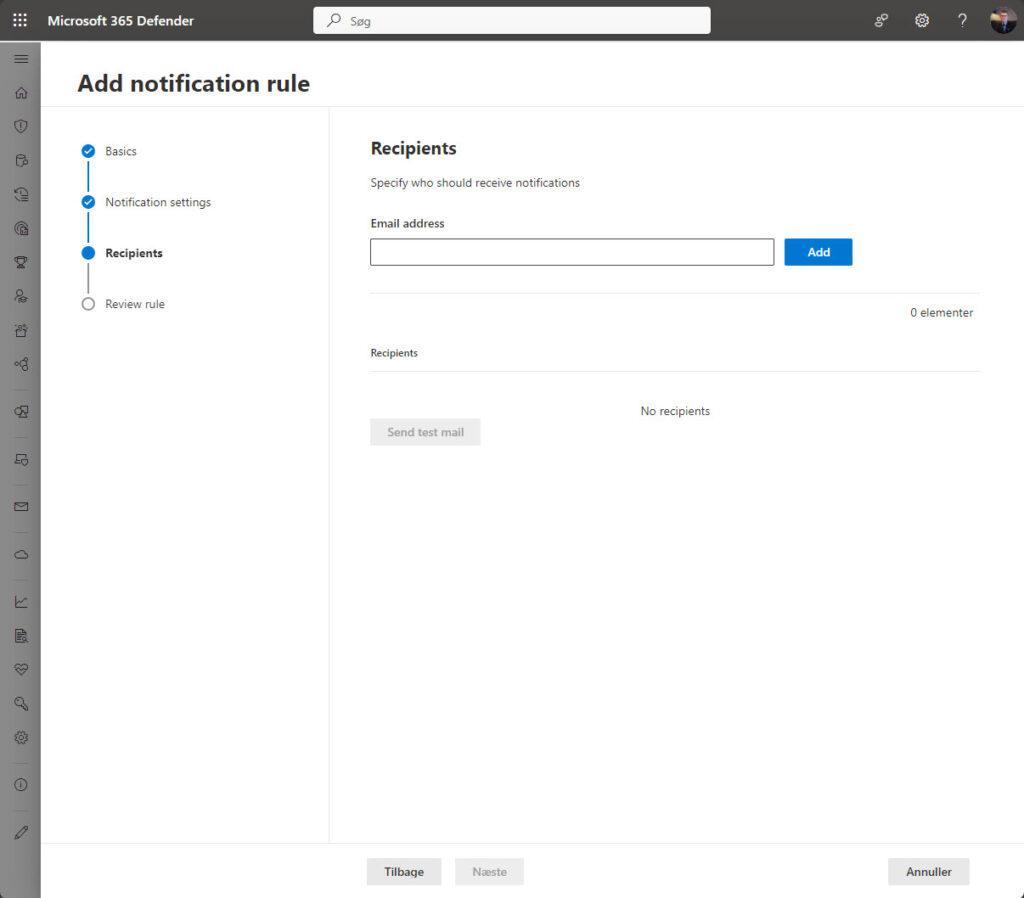
Recipients of the notifications is set on the last page in the wizard – but for now (a bit sad), there is no auto complete for etc. identityes or distribution lists in your tenant – hope we will see this soon! 🙀🫢
Separate multiple addresses by adding a comma at the end of each address. Select Add to add the recipients. You can see the recipients at the bottom of the pane after successfully adding addresses.
After you filled in the email(s) – you can test the notification to if you click on Send test mail on the wizard – we get the overview of the new rule like this:
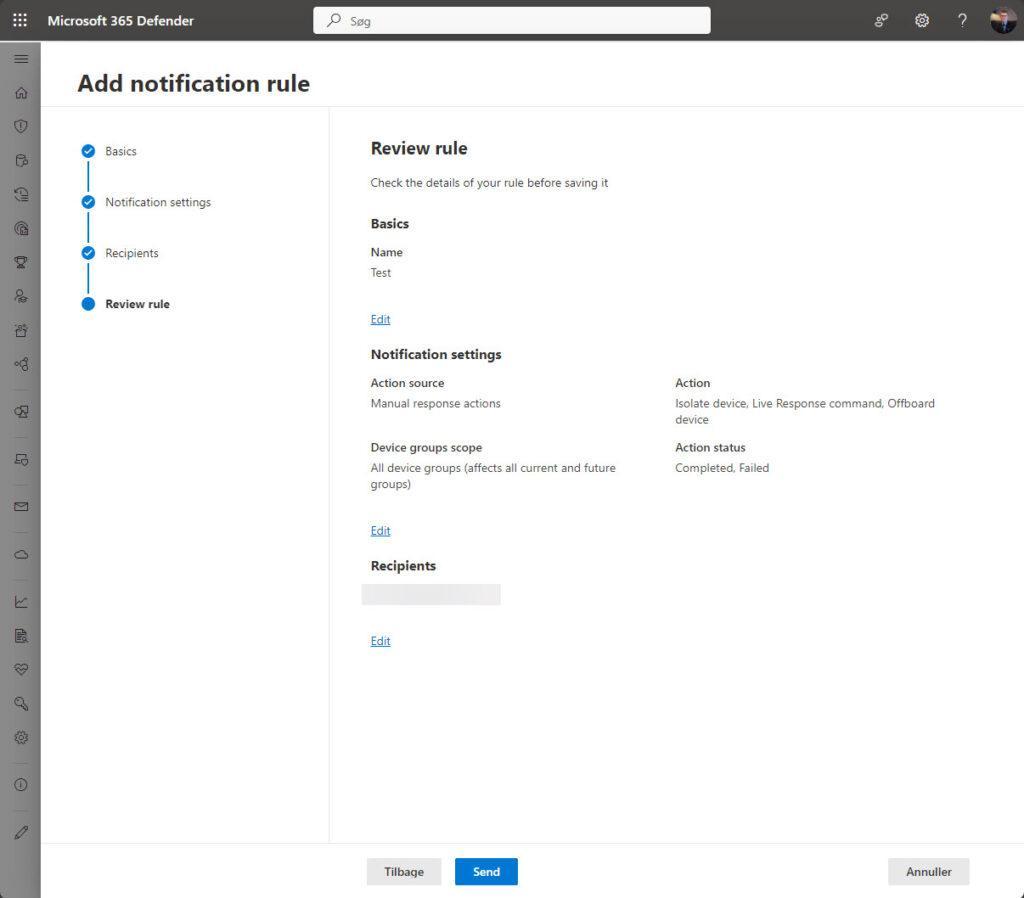
Select Submit at the bottom of the pane to finish the rule creation. Recipients will then start receiving notifications through email based on the settings you just had setup. The new rule appears in the Notifications rule list under the Actions tab in the Microosft Defender XDR Portal.
Now your rule is ready – time to play! 🤪
The notification there is send to you
A few seconds or around that later (it depends on your mailflow/scanning too) you will then get a notification with some details (but from my take and others, we need more information in the notification!)

Conclusion
As I have been in the process under the Private Preview too – it´s fun to follow the development of features with Microsoft – and also to give a lot of feedback to PM´s in the teams – and to find all the funny bugs and fun delays in the beginning for sending of notifications too – but its there, but still some small features needed to be added – we hope it´s getting added soon! 😉🙌
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳