Last Updated on July 5, 2023 by Michael Morten Sonne
Intoduction
Microsoft’s Defender for Endpoint (MDE) – is a cloud-based security platform that empowers the largest enterprises in the world with Threat & Vulnerability Management, Endpoint Detection & Response, Attack Surface Reduction, and so much more to help enterprises to prevent, detect, investigate, and respond to advanced threats – in words: A unified platform for preventative protection, post-breach detection, automated investigation, and response.
Personal in my own tenant I use it – and cool to see all the insigts and fun about it, and you should take a look too! 😉😁
You can take advantage of the Microsoft’s Defender for Endpoint P2 3-month trial right here (no credit card needed) to learn about this technology in a test environment and get your cloud security skills with the evaluation lab to test it out for FREE 🎉🎁!
Whether you already use MDE in your organization, you’re thinking about switching to MDE, or you’re looking to gain some cloud security skills to add to your resume, having a lab environment is the best way to learn and play around with these features without causing big chaos at work or in a production setup.
In this blog, I’ll show you how to set up a test environment in no time and we’ll even simulate a ransomware attack against your environment! (Hahahahaha 🦹)
See more here to: Microsoft Defender for Endpoint | Microsoft Security
Now let’s start
First we need to start a trial so we get some licenses to play with – here we need to sign up here the special link here Microsoft’s Defender for Endpoint P2 3-month trial right here as over at the public page Microsoft Defender for Endpoint to start a free trial only have a link to a free 1-month trial 😲😭
Before you can hit the ground running, we need to set up your account (it wont take long time).
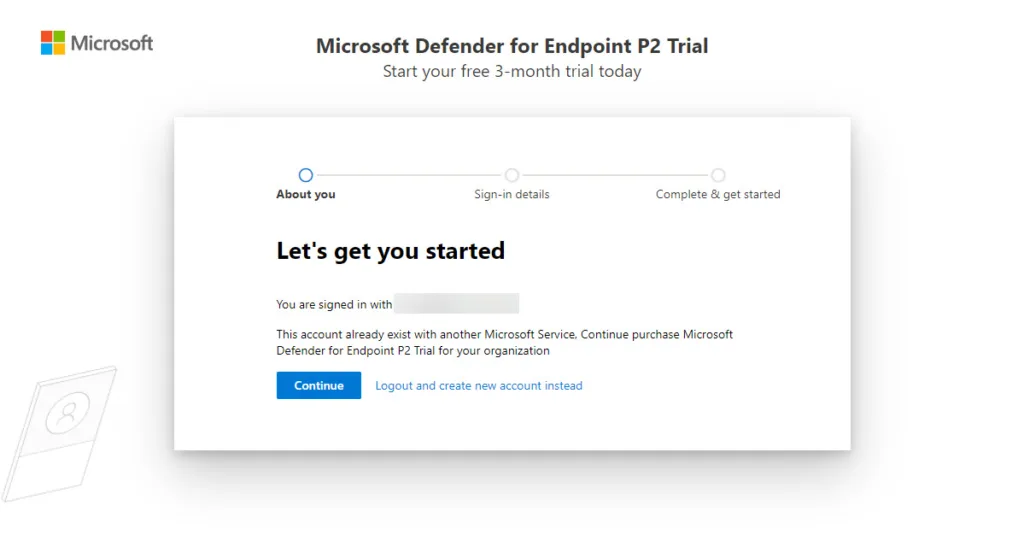
- Enter your email address on the web page to start the sign-up process and login if you have an existing tenant/lab
- Click Continue when you are ready to signup for the trial and have permissions to do this
- Now you have a trial licens for MDE to play around with!
If you not have an account/tenant to use, we need to signup for a new account first.
To do this you need to perform this:
- Go to Microsoft’s Defender for Endpoint P2 3-month trial right here and input an email you want to use.
- Click Next and confirm you will configure your accont. Then you will need to enter a first name, last name, phone number, contry and choose a company name and so on.
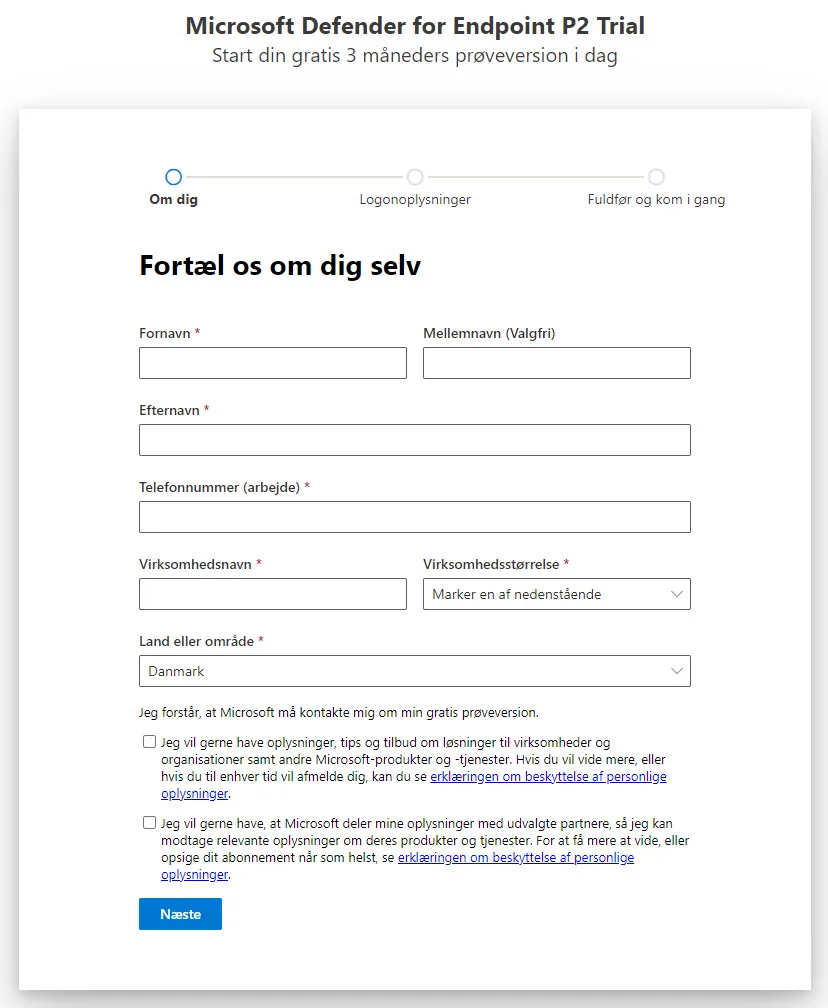
- Verify your phone number with a call or text then choose a name for your tenant. This name will be used when you sign in to your test tenant – so pick a good one you can remember! 😁
- Time to create the account that you will be using to access MDE. You can also review the trial agreement here (which tis strongly recommend).
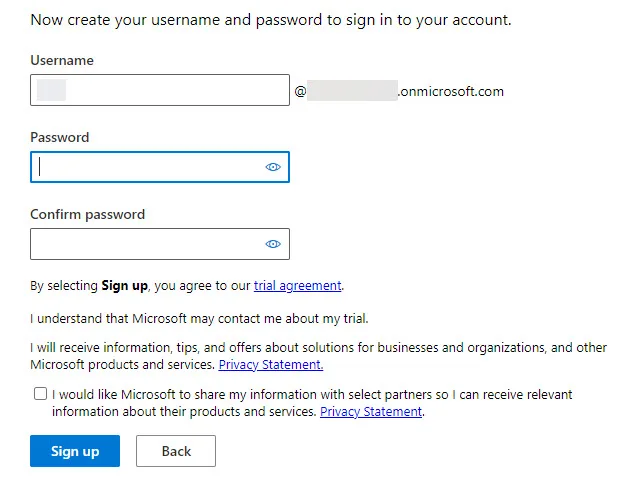
- Confirm your details then get Get Started!
Once you sign in with your new account, you will be at https://security.microsoft.com – This is your new playground – This is here you find Microsoft Defender for Endpoint and many other cool stuff if you have the licenses!
To follow all the news and updates regarding Defender for Endpoint – heads out to Microsoft 365 Defender Blog – Microsoft Community Hub and see it all! 😉
Yeah okay great – Now What? Now its time to some fun stuff!
Now you can actually get your hands dirty with the many features of MDE. Fortunately for us, Microsoft offers us evaluation labs where we can access virtual machines in Azure to play with for free, simulate attacks that are provided in the MDE portal (you can also use your own attacks if you want! 😉🥳)
The evaluation lab allows us to learn about Microsoft Defender for Endpoint without having to onboard our own devices, although I will touch on that later, because that is something you should be familiar with!
Why use evaluation labs?
Conducting a comprehensive security product evaluation can be a complex process requiring cumbersome environment and device configuration before an end-to-end attack simulation can actually be done. Adding to the complexity is the challenge of tracking where the simulation activities, alerts, and results are reflected during the evaluation.
The Microsoft Defender for Endpoint evaluation lab is designed to eliminate the complexities of device and environment configuration so that you can focus on evaluating the capabilities of the platform, running simulations, and seeing the prevention, detection, and remediation features in action.
Setup Attack Simulations
When setting up the evaluation lab is quite simple, first click Evaluation lab in the left pane under the Evaluation & tutorials drop-down menu, then click the blue Setup lab button.
A direct link is here: Evaluation lab – Microsoft 365-sikkerhed

If you not see a tab Evaluation lab in the left pane, understand that it can take several minutes for your test tenant to get completely set up on the backend.
When your tenant is ready for lab setup you can choose the amount of devices you want in the lab. They will be deleted after a certain amount of time for cleanup and free the ressoruces for other, but you can request more after they are deleted – so dont worry 😉
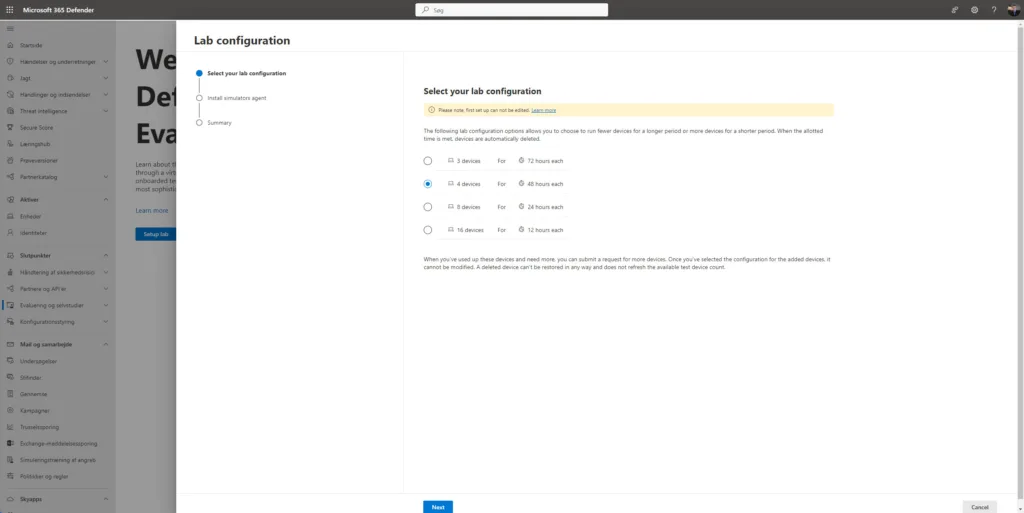
Agree to the terms (you need to open them and click Accept) and enter your email and name.
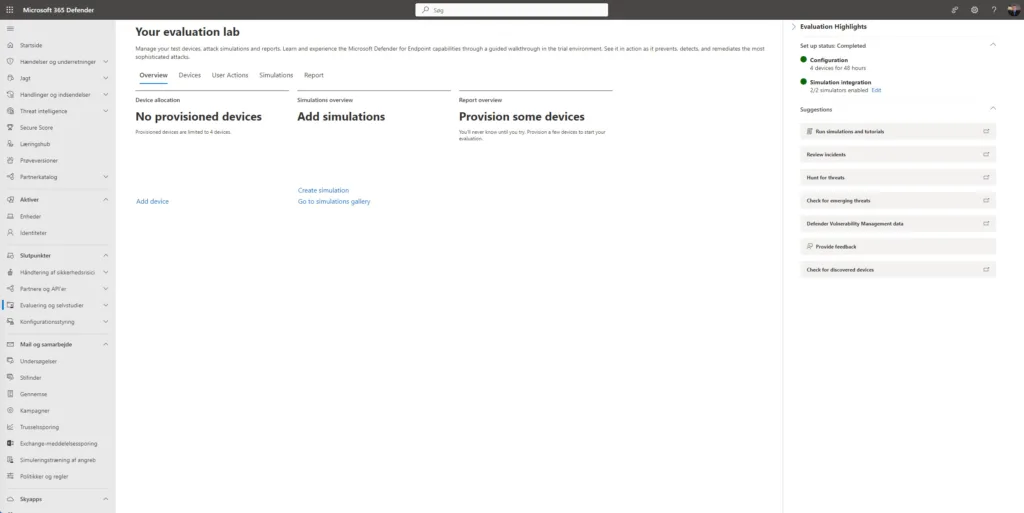
On the summary page you can click on Setup lab then your evaluation lab will look like this
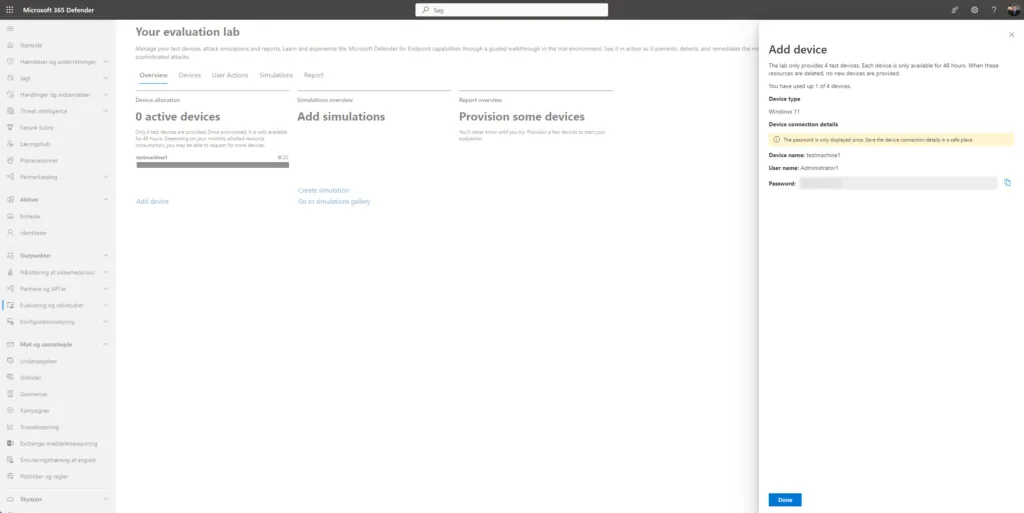
To setup devices to use as you selected before, click on Add device and choose the operating system you want, currently you can choose Windows 10, Windows 11, Windows Server 2016 , Windows Server 2019 or a Linux Ubuntu server. Then click Add device.
There is some different setup and use cases – select the setup and Available Tools for your need.
Once you add the device, you will see a machine name along with login credentials. Make sure to copy the password, because you will actually be able to access this virtual machine with these credentials – keep them as it will only be showed once!
Your new device will take a few minutes to get started up and setup, but while you wait, you can head over to Tutorials & simulations in the left pane of MDE and check out some of the attack simulations provided there you can play with.
Once your device is ready, head back to the Evaluation lab in the left pane and click on Create simulation near the middle.
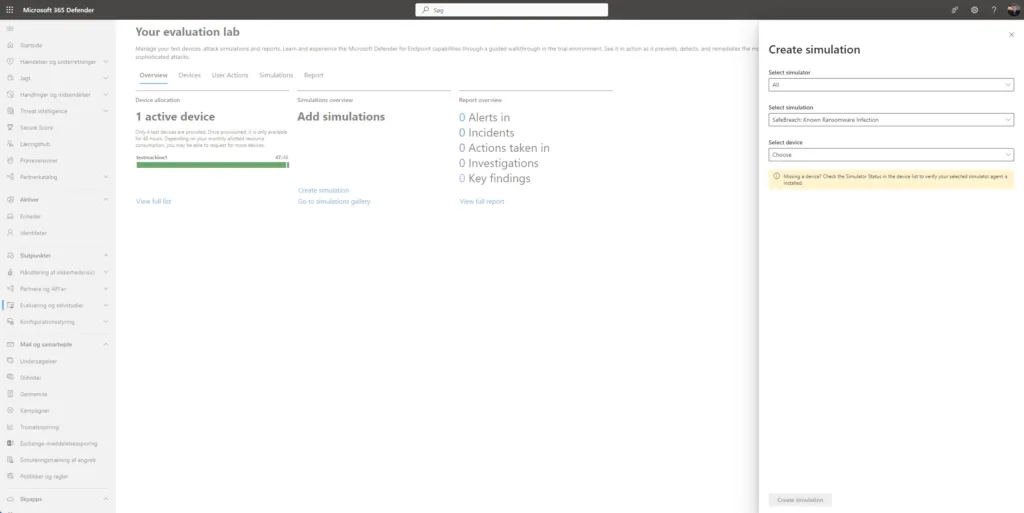
Select your new device and the simulation you want to run, then click the blue Create simulation button. For this tutorial, I will be going with the Known Ransomware Infection simulation 👨💻
The Sample SafeBreach ransomware infection is simulated in this scenarios as per this post is created:
- WannaCry 2.0 Ransomware
- Trojan-Ransom.Win32.Locky.bl
- JAFF Ransomware
- JAFF Ransomware Dropper
- ZepplinRansom
- NotPetya
- Ryuk Ransomware
- Ryuk Ransomware Dropper
- Nemty Ransomware
- Ransom.BitPaymer
Once your simulation has been created on the machine, click on the Devices tab so you can watch the fireworks. Click the three dots next to your device then click Connect. This will allow you to download an RDP (Remote Desktop Protocol) file and connect to your device with the password you made sure to copy.. right? 🙃
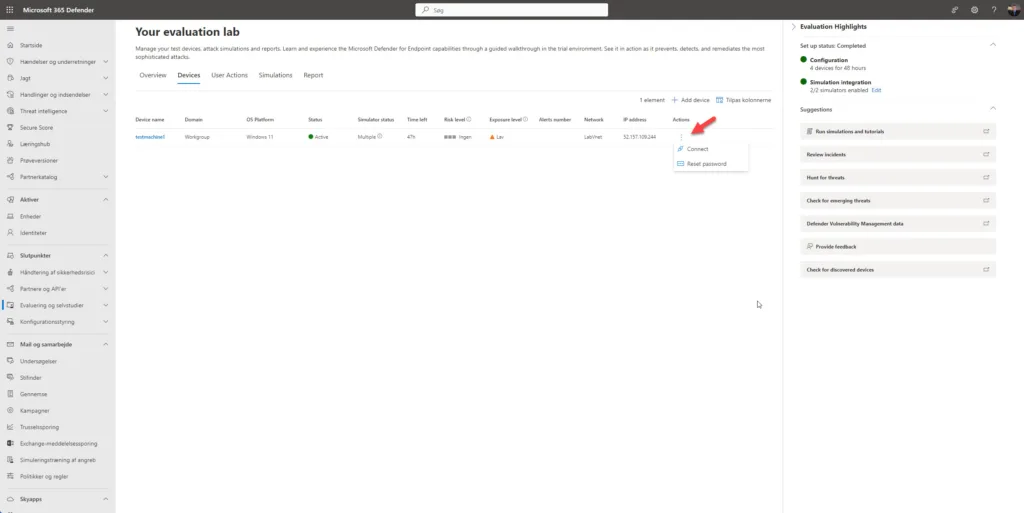
Once connected you may see Defender notifications popping up as your device battles for its life against the simulation attacks – haha 🤣🥹😲
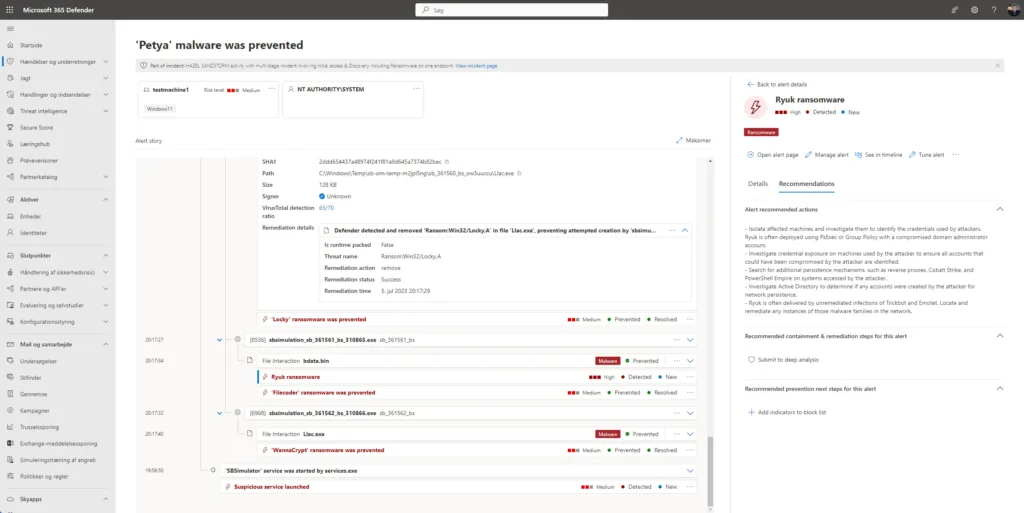
You can click on the notifications to see more details within the Windows Defender GUI
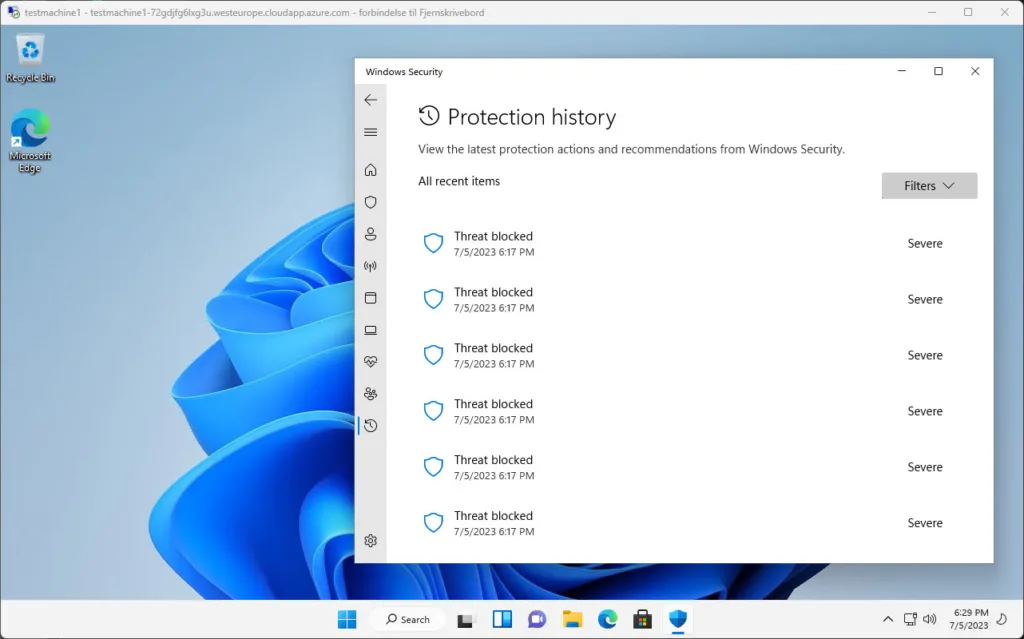
See more about the Attack Simulations and there actions
Go back in your MDE portal as alerts/incidents will be lighting up like a Christmas tree – so head over to Alerts under the Incidents & alerts drop-down in the left pane now! 🥳
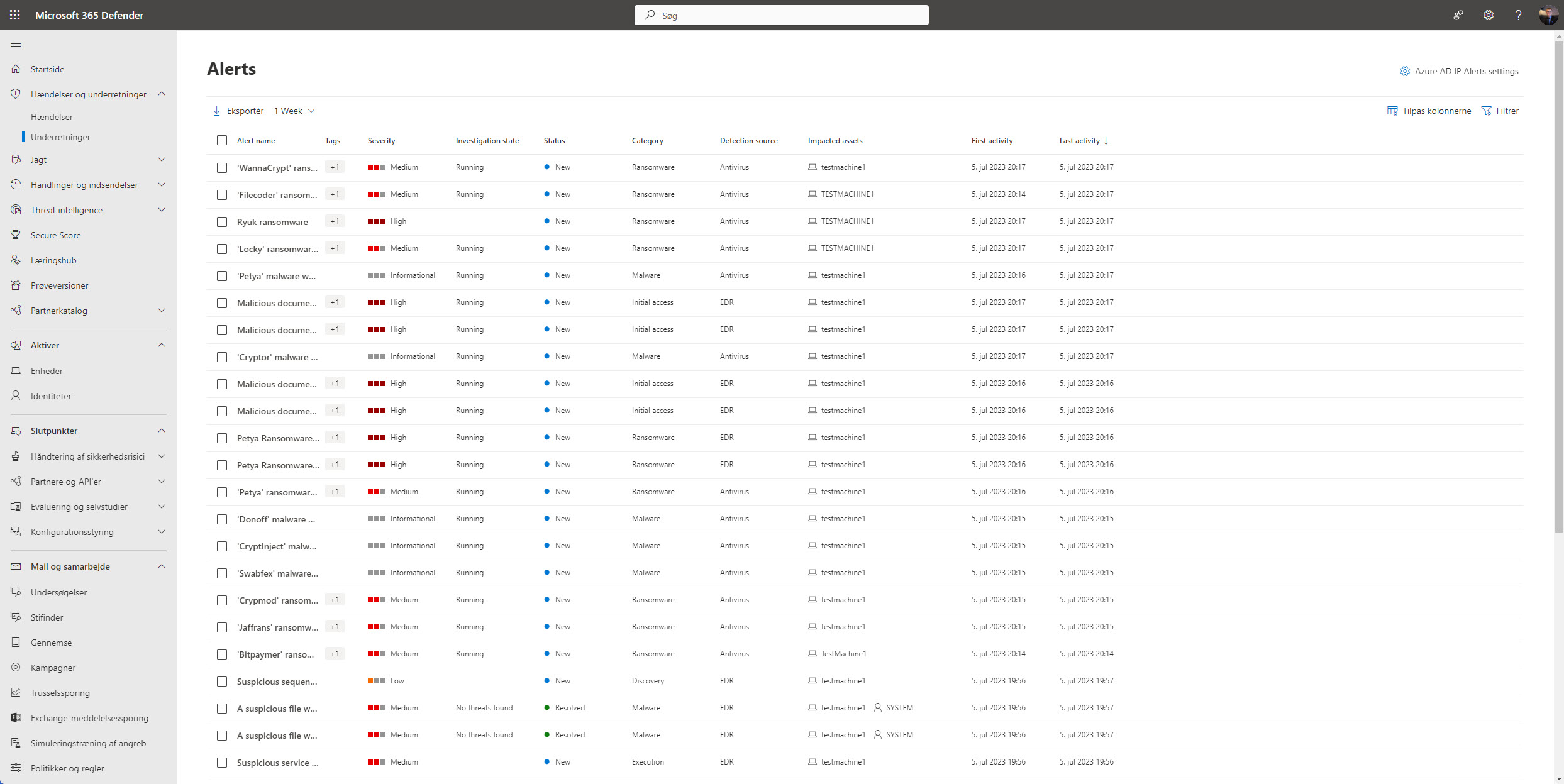
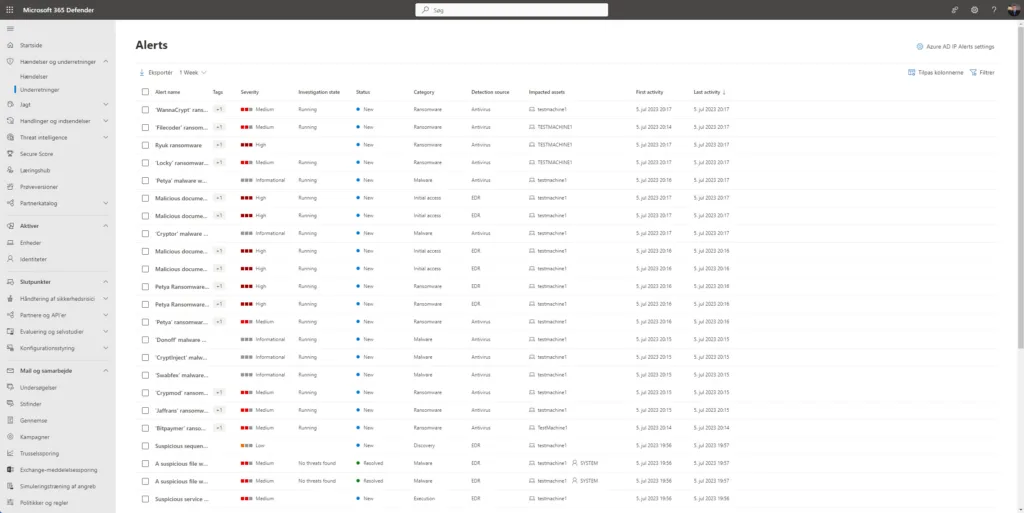
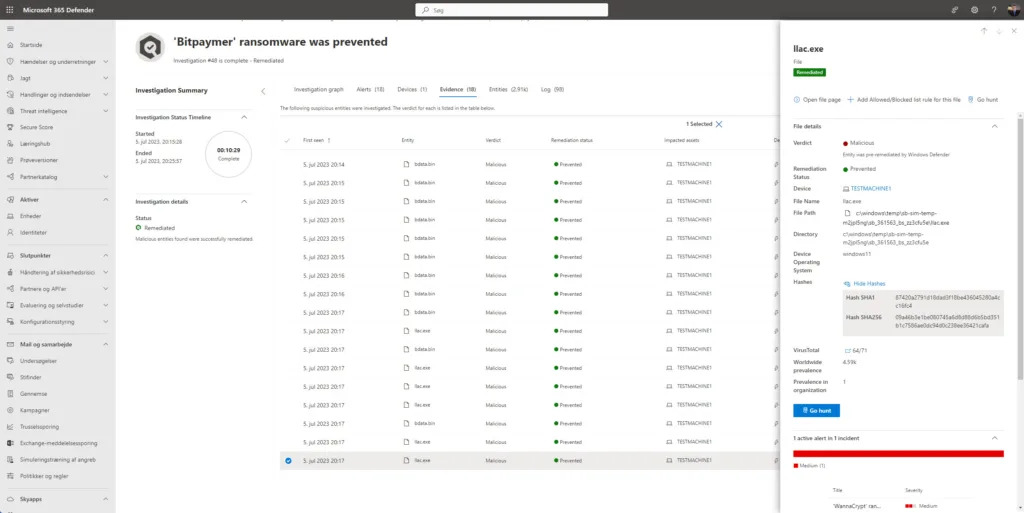
Now click one of the alerts and you’ll see an abundance of information about the alert and what has happen on the test VM – and there is a lot of usefull information!
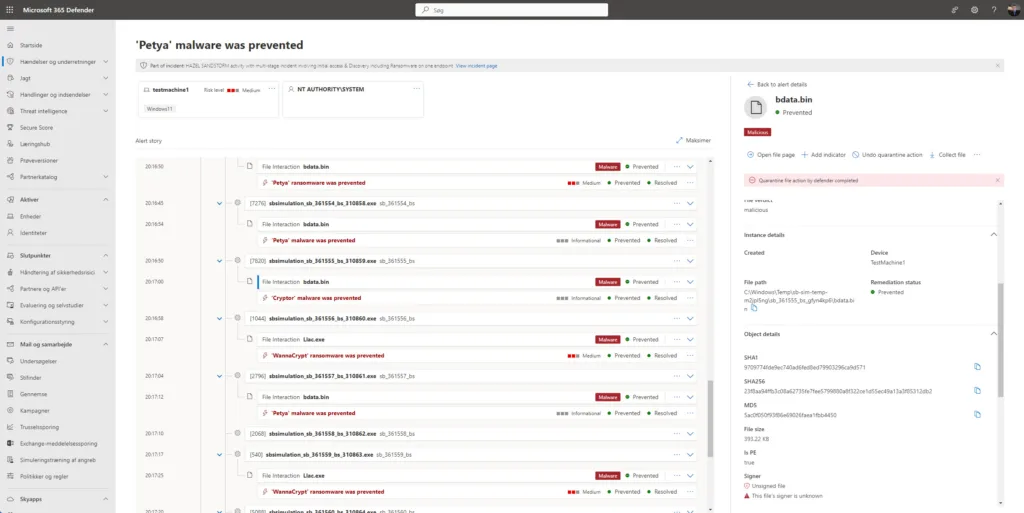
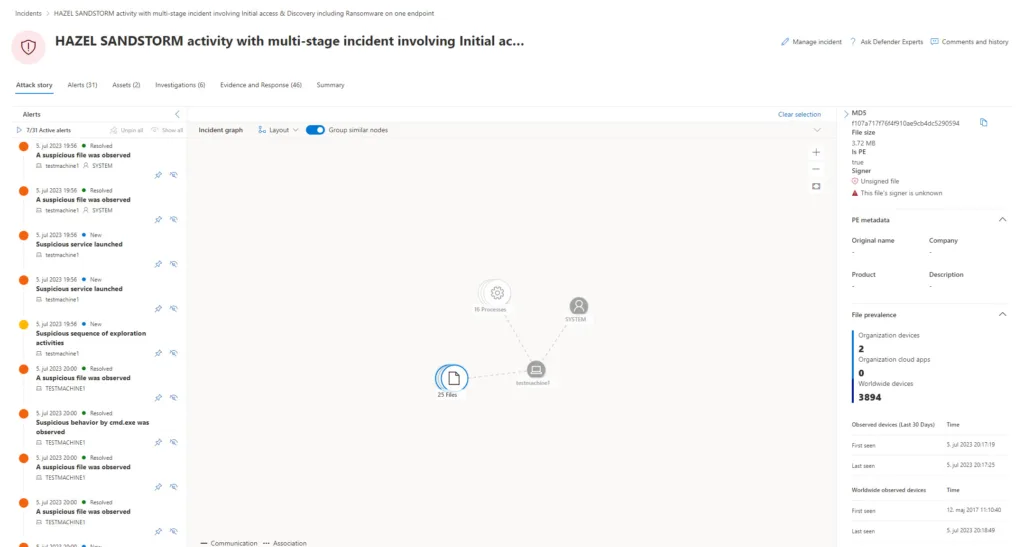
Microsoft Defender for Endpoint automatically lumped all of these alerts into an incident and began an automated investigation. This investigation provides defenders with context about the alerts.
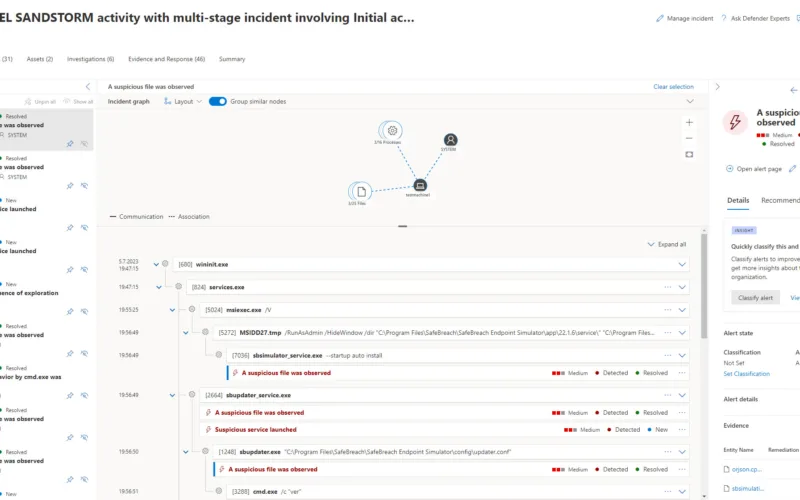
Click on Incidents in the left pane to see that information – then click on a incident name then click the Investigations tab.
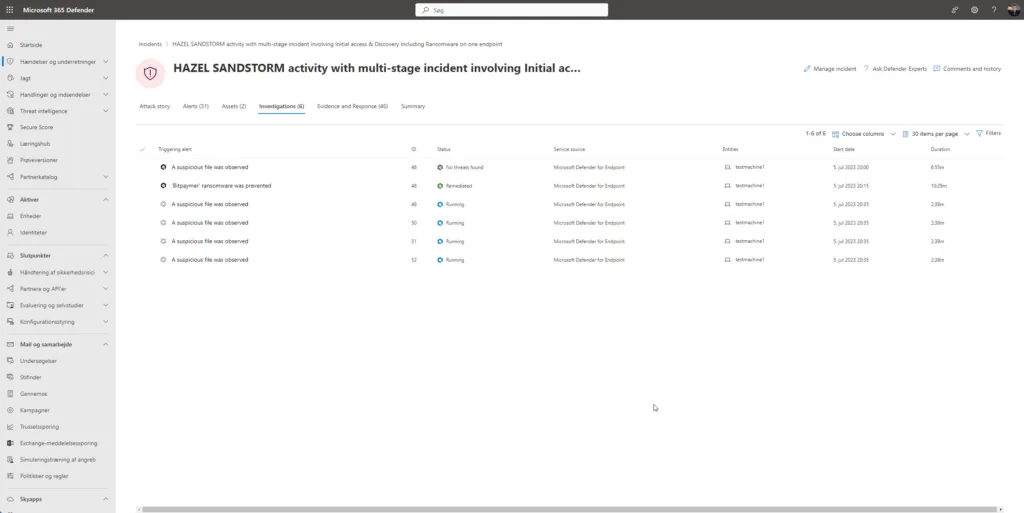
Here you can see the automated investigation and relation information. Click on it to dive deeper 😲
Here you’ll see an interactive graph of the investigation. Click on one of the components of the graph or on one of the tabs and dive into the information generated by the investigation.
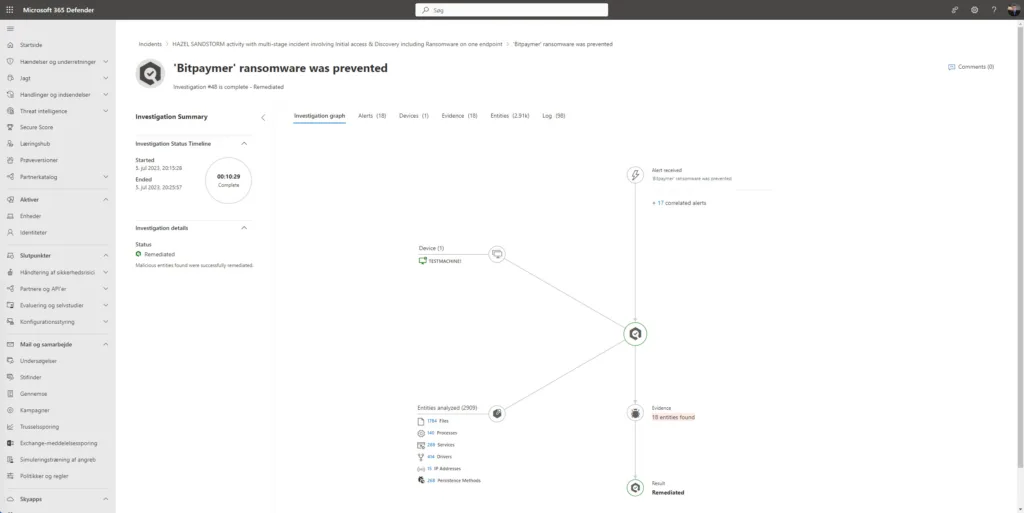
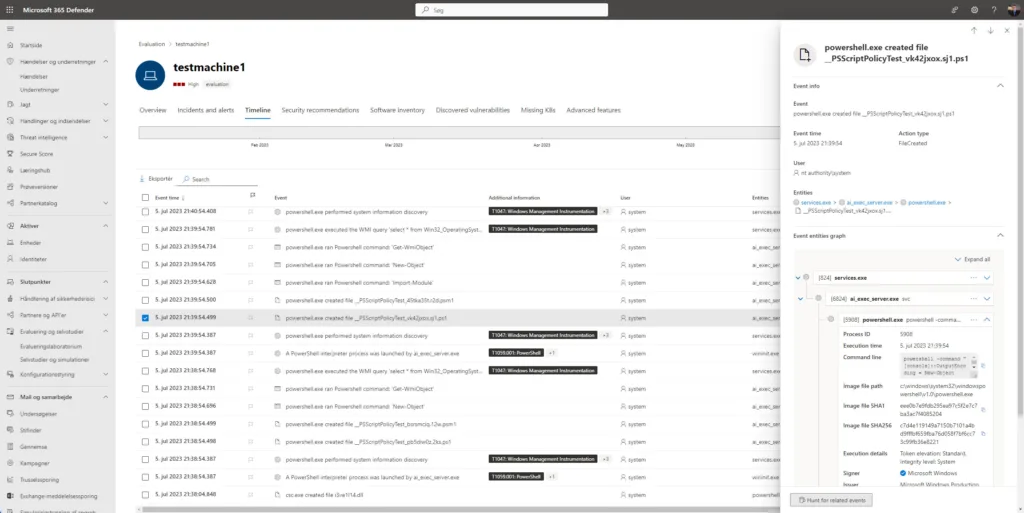
The Microsoft Defender for Endpoint device timeline helps you research and investigate anomalous behavior on your devices more quickly. You can explore specific events and endpoints to review potential attacks in your organization. You can review specific times of each event, set flags to follow up for potentially connected events, and filter to specific date ranges.
In Microsoft Defender for Endpoint, Techniques are an additional data type in the event timeline. Techniques provide more insight on activities associated with MITRE ATT&CK techniques or sub-techniques.
Select a Technique to open its corresponding side pane. Here you can see additional information and insights like related ATT&CK techniques, tactics, and descriptions.
That was exciting to get a quick look into wasn’t it? There’s plenty more to explore in the Microsoft Defender for Endpoint portal so I urge you to try some more simulations, play around with the numerous features, check out the official Microsoft docs about MDE, and subscribe to this blog as there will be more MDE content to come.
The next most be regarding Onboarding Your First Devices 😉
Conclusion
Creating a free lab using Microsoft Defender for Endpoint and simulating etc. ransomware attacks can be a highly valuable and educational exercise.
However, it’s important to note that simulating ransomware attacks should be conducted in a controlled environment and with proper authorization. Care should be taken to ensure that the lab environment is isolated from the production environment to prevent any accidental damage or data loss. Additionally, organizations should comply with all legal and ethical considerations when conducting such simulations.
Overall, a free lab with Microsoft Defender for Endpoint and simulated ransomware attacks can be a valuable tool in strengthening cybersecurity defenses, improving incident response capabilities, and enhancing the overall security posture of an organization.
Microsoft Defender for Endpoint (MDE), formerly known as MDATP, is an enterprise-level endpoint security platform. MDE offers Endpoint Detection & Response (EDR) for both Windows, Windows Server and Linux servers (Integration with Microsoft Defender for Cloud), Mac OS and Linux servers – but you can use it on Android and iOS also to protect the devices here. MDE is the cloud-platform designed to help prevent, detect, investigate, and respond to advanced threats.
Se more here: Onboard to the Microsoft Defender for Endpoint service | Microsoft Learn
While the names are similar, Windows Defender is an antivirus, but Microsoft Defender for Endpoint (MDE) is a cloud-based security platform capable of Endpoint Detection & Response (EDR), automated investigations, web content filtering, and much more.
And you can Integration with Microsoft solutions – Defender for Endpoint directly integrates with various Microsoft solutions, including:
- Microsoft Defender for Cloud
- Microsoft Sentinel
- Intune
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Identity
- Microsoft Defender for Office
- Skype for Business (I hope not you using this 🙃🤣)
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳