Last Updated on February 24, 2024 by Michael Morten Sonne
Intoduction
In Public Preview as this post is written
Introducing the Updated Advanced Settings Page for Microsoft Defender for Identity – Now “Alerts Thresholds”
Thrilled to share that the Microsoft Defender for Identity (MDI) team has revamped the Advanced Settings page, now known as ‘Alerts Thresholds.’, offering a more tailored and flexible approach to your monitoring preferences.
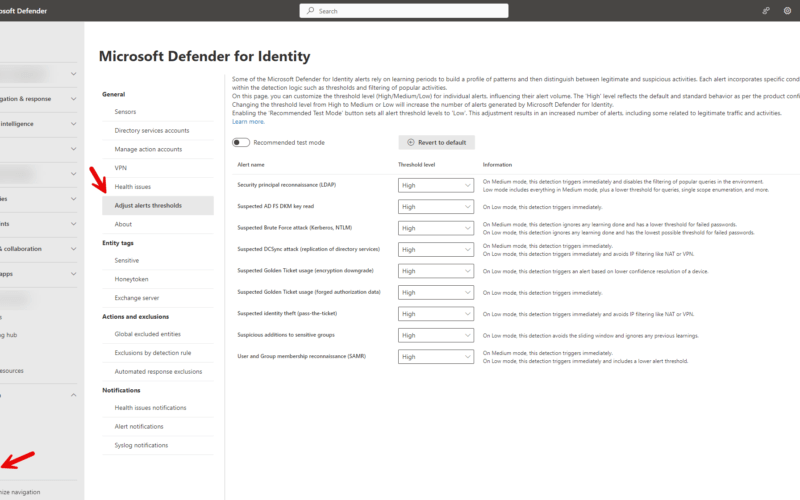
Defender for Identity alerts utilize learning periods to establish patterns and distinguish between legitimate and suspicious activities. Each alert incorporates specific conditions in the detection logic, including alert thresholds and filtering for popular activities. Utilize the Adjust alert thresholds page to tailor the threshold level for specific alerts, thereby influencing their alert volume.
What’s new
Now, with ‘Alerts Thresholds,’ you have unparalleled control over the threshold level for each alert on your list, regardless of the ‘Remove Learning Period’ setting. Let’s delve into the key updates:
- Flexible Threshold Adjustment: Easily adjust the threshold level for each alert, empowering you to customize your monitoring experience according to your specific needs.
- Default Behavior – High Level: The ‘High’ level represents the default behavior, ensuring a standard alert configuration for your convenience.
- Alert Volume Control: Transition from ‘High’ to ‘Medium’ or ‘Low’ to fine-tune your alert volume based on your preferences and operational requirements.
- Recommended Test Mode: Enable ‘Recommended Test Mode’ to set all thresholds to ‘Low,’ creating an ideal environment for comprehensive testing and analysis.
It’s important to note that alerts are triggered immediately under certain conditions. If the Recommended test mode option is selected, or if a threshold level is set to Medium or Low, alerts will be triggered promptly, regardless of whether the alert’s learning period has concluded. This flexibility allows users to actively manage and fine-tune the alerting behavior based on their specific testing or monitoring requirements, nice! 👌
Use cases
The enhanced ‘Alerts Thresholds’ feature opens up a multitude of use cases to optimize your MDI experience:
- Validation of MDI Security Alerts – Removing Learning Periods:
- Effectively validate MDI security alerts without constraints imposed by learning periods.
- Adjust Alert Trigger Logic Based on Customer Needs:
- Tailor alert trigger logic to meet specific customer requirements. For instance, fine-tune MDI detections with built-in thresholds, trigger delays, Suspected identity theft detections, Suspected DCSync attack (replication of directory services), and IP address profiling, ensuring accurate assessments such as identifying of NAT devices.
How to try it
Prerequisites
- To view the Adjust alerts thresholds page in the Microsoft Defender XDR portal you need access at least as a Security viewer.
- To make changes on the Adjust alerts thresholds page you need access at least as a Security administrator.
Enable Preview features
Change only the default and recommend alert thresholds from the default (High) only after careful consideration.
To experience this feature, it’s necessary to activate the Preview Features within the Microsoft Defender XDR Portal.
To do this, go to Home – Microsoft Defender > System > Settings > Preview features and set the toggle under Preview features from Off to On:
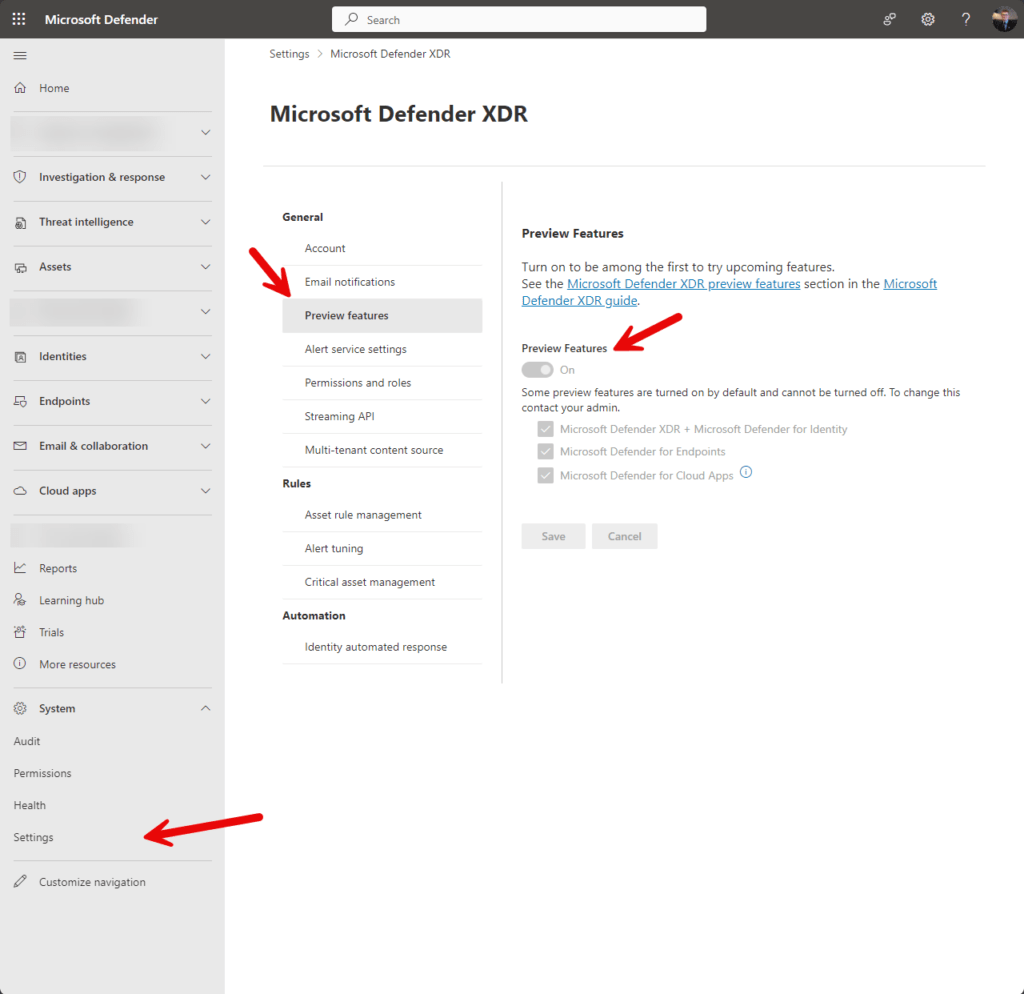
The new settings page
You can start exploring the enhanced flexibility of the ‘Alerts Thresholds’ feature today. Dive into the revamped settings and unlock a new level of customization for your monitoring preferences.
Explore, customize, and stay secure with Microsoft Defender for Identity – now with ‘Alerts Thresholds.’
To find the portal, go to Home – Microsoft Defender > System > Settings >Identities > Alert and Thresholds
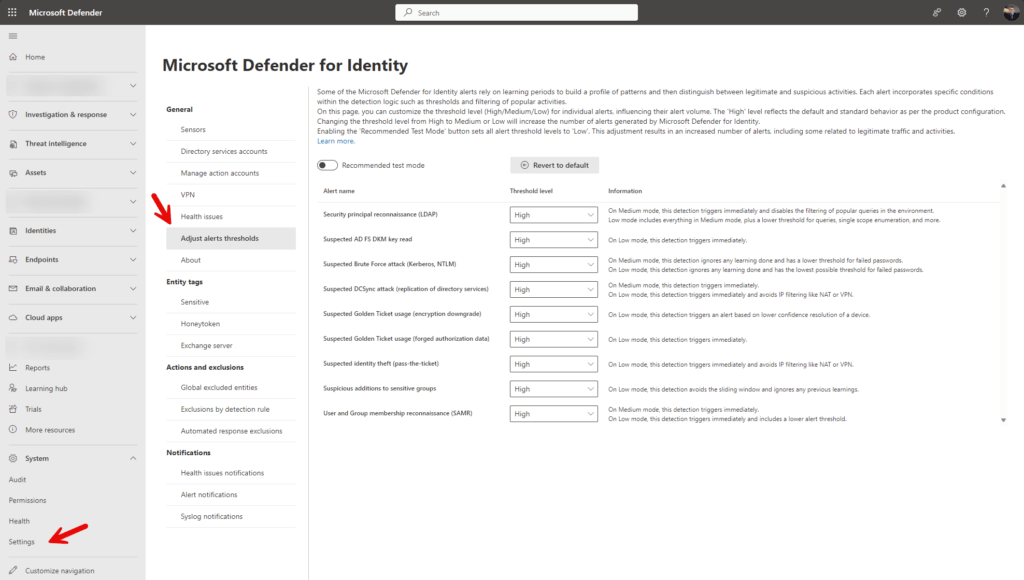
- Find the alert you wish to modify the threshold for, and then choose the desired threshold level to apply. The options is:
- High is the default value, and applies standard thresholds to reduce false positives.
- Medium and Low thresholds increase the number of alerts generated by Defender for Identity.
- If you choose either Medium or Low, the Information column will highlight key details to assist you in comprehending how the alteration influences the alert behavior – read it!
- Select Apply changes to save your changes.
Select Revert to default and then Apply changes to reset all alerts to the default threshold (High). Returning to the default setting is permanent, and any adjustments made to your threshold levels will be discarded and cannot be recovered.
Activate Test Mode
The Recommended test mode feature is crafted to provide a understanding of all Defender for Identity alerts, encompassing those associated with genuine traffic and activities. This facilitates an efficient evaluation of Defender for Identity in your enviroment.
If you have recently implemented Defender for Identity, opt for the Recommended test mode to switch all alert thresholds to Low, thereby amplifying the number of triggered alerts.
During the Recommended test mode, threshold levels in the portal become read-only. Once your testing is complete, deactivate the Recommended test mode to revert to your initial settings.
Click on Apply changes to ensure the preservation of your modifications. Then you are ready! 🥳🔐
Supported detections for threshold configurations
The table below outlines the categories of detections that allow modifications to threshold levels, along with the implications of selecting Medium and Low thresholds.
Cells labeled as N/A signify that the threshold level is not applicable or supported for the specific detection. I think more will come over time
| Detection | Medium | High |
|---|---|---|
| Security principal reconnaissance (LDAP) | When set to Medium, this detection triggers alerts immediately, without waiting for a learning period, and also disables any filtering for popular queries in the environment. | When set to Low, all support for the Medium threshold applies, plus a lower threshold for queries, single scope enumeration, and more. |
| Suspicious additions to sensitive groups | N/A | When set to Low, this detection avoids the sliding window and ignores any previous learnings. |
| Suspected AD FS DKM key read | N/A | When set to Low, this detection triggers immediately, without waiting for a learning period. |
| Suspected Brute Force attack (Kerberos, NTLM) | When set to Medium, this detection ignores any learning done and has a lower threshold for failed passwords. | When set to Low, this detection ignores any learning done and has the lowest possible threshold for failed passwords. |
| Suspected DCSync attack (replication of directory services) | When set to Medium, this detection triggers immediately, without waiting for a learning period. | When set to Low, this detection triggers immediately, without waiting for a learning period, and avoids IP filtering like NAT or VPN. |
| Suspected Golden Ticket usage (forged authorization data) | N/A | When set to Low, this detection triggers immediately, without waiting for a learning period. |
| Suspected Golden Ticket usage (encryption downgrade) | N/A | When set to Low, this detection triggers an alert based on lower confidence resolution of a device. |
| Suspected identity theft (pass-the-ticket) | N/A | When set to Low, this detection triggers immediately, without waiting for a learning period, and avoids IP filtering like NAT or VPN. |
| User and Group membership reconnaissance (SAMR) | When set to Medium, this detection triggers immediately, without waiting for a learning period. | When set to Low, this detection triggers immediately and includes a lower alert threshold. |
For additional information on all alerts within Defender for Identity, please refer to this page: Security alerts in Microsoft Defender for Identity – the list is loooong 🤣🔐
Review security alerts
Alerts from Defender for Identity can be accessed from multiple locations, including the Alerts page, the Incidents page, the pages of individual Devices, and from the Advanced hunting page. Here I show how to use the Alerts page.
In the Microsoft Defender XDR portal select Incidents & alerts > Alerts.
To see alerts from Defender for Identity, on the top-right select Filter, and then under Service sources select Microsoft Defender for Identity, and then select Apply.
Conclusion
In summary, the enhanced Alerts Thresholds feature in Microsoft Defender for Identity provides users with greater flexibility and customization options. Admins can now adjust threshold levels for specific alerts, optimizing their monitoring experience based on individual needs.
The introduction of Recommended Test Mode streamlines comprehensive testing by setting all thresholds to ‘Low’. However, users should be cautious when reverting to default settings, as it is an irreversible action.
Additionally, the ability to activate Test Mode allows for a thorough evaluation of Defender for Identity alerts, offering valuable insights into both legitimate and suspicious activities.
The read-only nature of threshold levels during test mode ensures consistency in testing, and users can easily apply changes as needed. The detailed table outlines supported detections for threshold adjustments, aiding users in making informed decisions.
Overall, these updates empower admins to fine-tune their alert configurations, contributing to a more efficient and tailored security monitoring experience.
It was an enjoyable experience testing it during the Private Preview phase as a participant in the Microsoft Customer Connection Program! 😉🔐
Thank you for taking the time to visit my blog. Kindly share it with others if you find it helpful for them! 😉🔐👍
Stay tuned for the new post about something cool! 🥳
References
What’s new – Microsoft Defender for Identity | Microsoft Learn